LebiShop商城系统最新版十一处SQL注入
这里也是需要有商家账号权限
首先注册普通用户账户,然后申请注册商家账户
申请商家用户是默认开发注册的
Shop.Supplier.Ajax.ajax_config文件
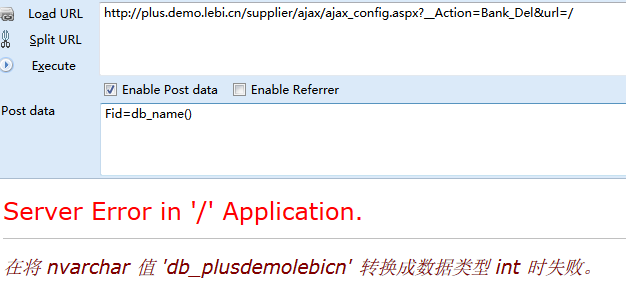
第一处SQL注入
第二处SQL注入
第三处SQL注入
第四处SQL注入
第五处SQL注入
第六处SQL注入
第七处SQL注入
第八处SQL注入
第九处SQL注入
第十处SQL注入
参数aids在GetList方法中的in条件语句中产生注入
第十一处SQL注入
上述SQL注入都是在通过RequestTool.RequestString方法获取参数值
这里只是进行了单引号的转义
然后参数值进入了数据库执行的in条件SQL语句
在in条件语句中没有单引号保护,导致RequestTool.RequestString的处理无效
导致恶意sql语句进入sql条件语句中,最终导致SQL注入产生