漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0137596
漏洞标题:同程旅游网移动端某接口泄漏(可查询订单/机票/酒店/电影等部分信息)
相关厂商:苏州同程旅游网络科技有限公司
漏洞作者: 1937nick
提交时间:2015-08-28 22:20
修复时间:2015-08-28 23:16
公开时间:2015-08-28 23:16
漏洞类型:未授权访问/权限绕过
危害等级:高
自评Rank:18
漏洞状态:厂商已经修复
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-28: 细节已通知厂商并且等待厂商处理中
2015-08-28: 厂商已经确认,细节仅向厂商公开
2015-08-28: 厂商已经修复漏洞并主动公开,细节向公众公开
简要描述:
高rank 送京东礼品卡 小激动
详细说明:
在某处看到同程移动端求测的状态我就来了,高rank 送京东礼品卡
类似一样的漏洞 以前在某处提交过 厂商说此问题之前有发现,评级低!
怎么现在有出现这种问题了呢? 羞羞的
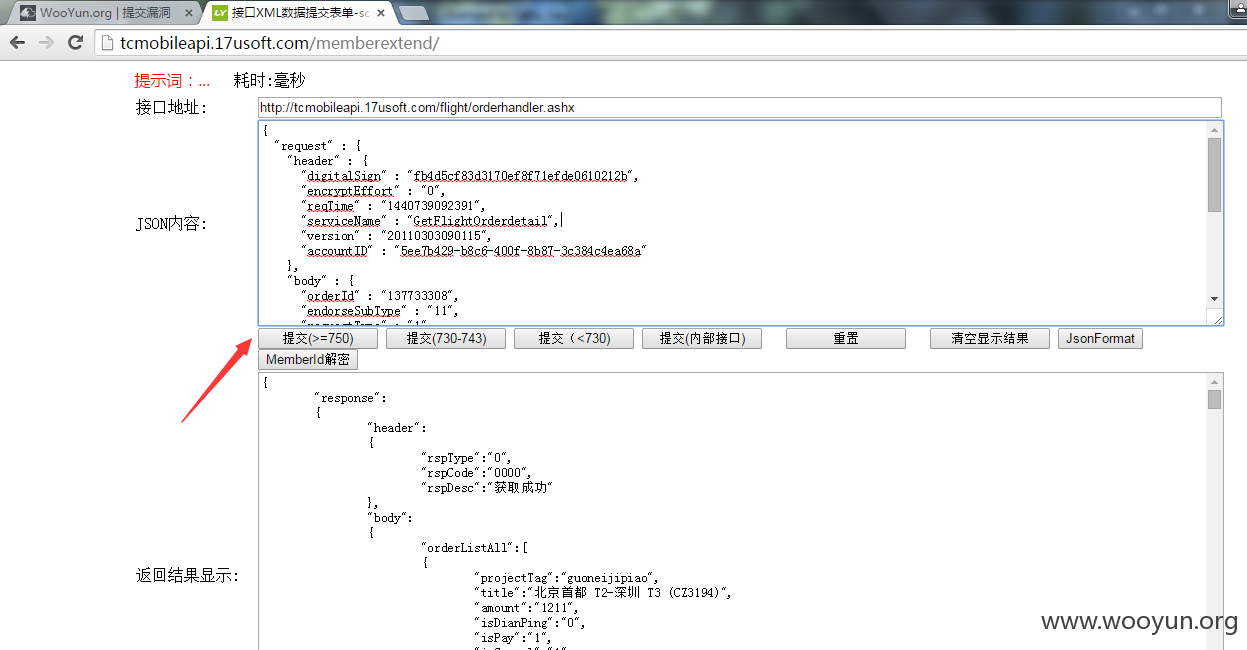
UARL: http://tcmobileapi.17usoft.com/memberextend/
1.机票接口地址:http://tcmobileapi.17usoft.com/flight/orderhandler.ashx
JSON
tID" : "5ee7b429-b8c6-400f-8b87-3c384c4ea68a"
},
"body" : {
"orderId" : "137733308",
"endorseSubType" : "11",
"requestType" : "1",
"clientInfo" : {
"refId" : "5866741",
"mac" : "10685e02588a205a100baa911e483423",
"clientIp" : "192.168.1.103",
"networkType" : "wifi",
"extend" : "2^com.tongcheng.iphone,4^8.4,5^iPhone5_2",
"versionType" : "iPhone",
"deviceId" : "4eaf3c51d6b4846d8599c297d9eb94347b64d4f8",
"versionNumber" : "7.5.0"
},
"endorseType" : "1",
"memberId" : "I0_d697650ed0d55a266b81ef6c18fdad5d"
}
}</code>
JSON输入后点击 提交(>=750) 查询
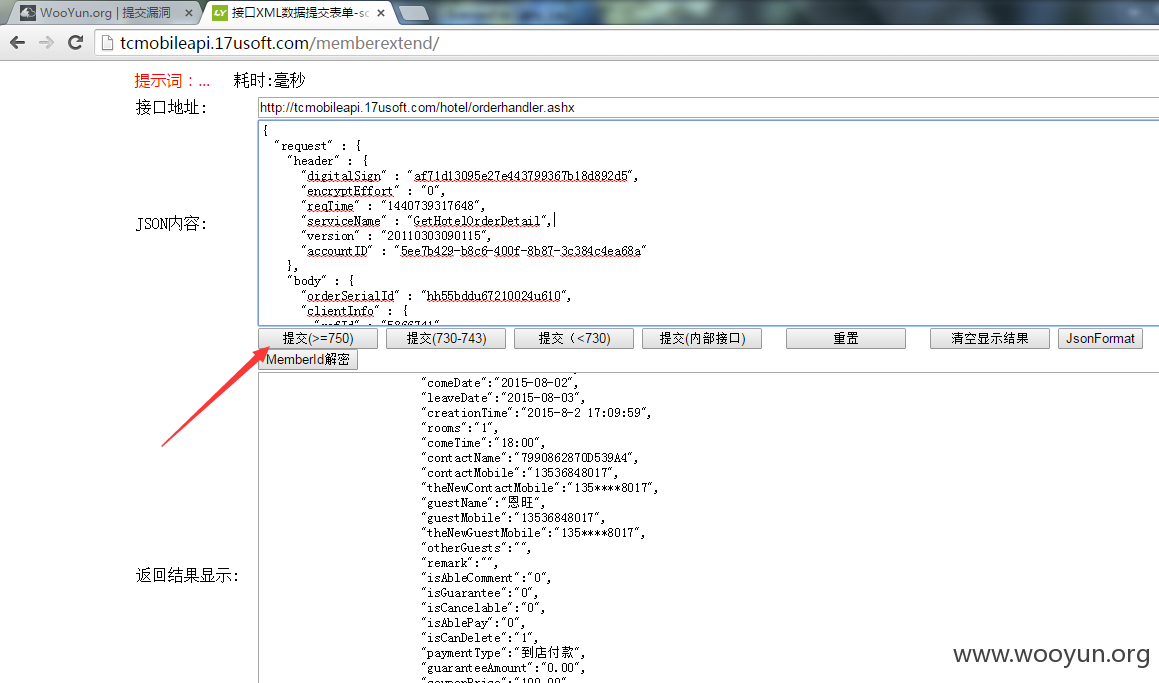
2.酒店接口地址:http://tcmobileapi.17usoft.com/hotel/orderhandler.ashx
JSON
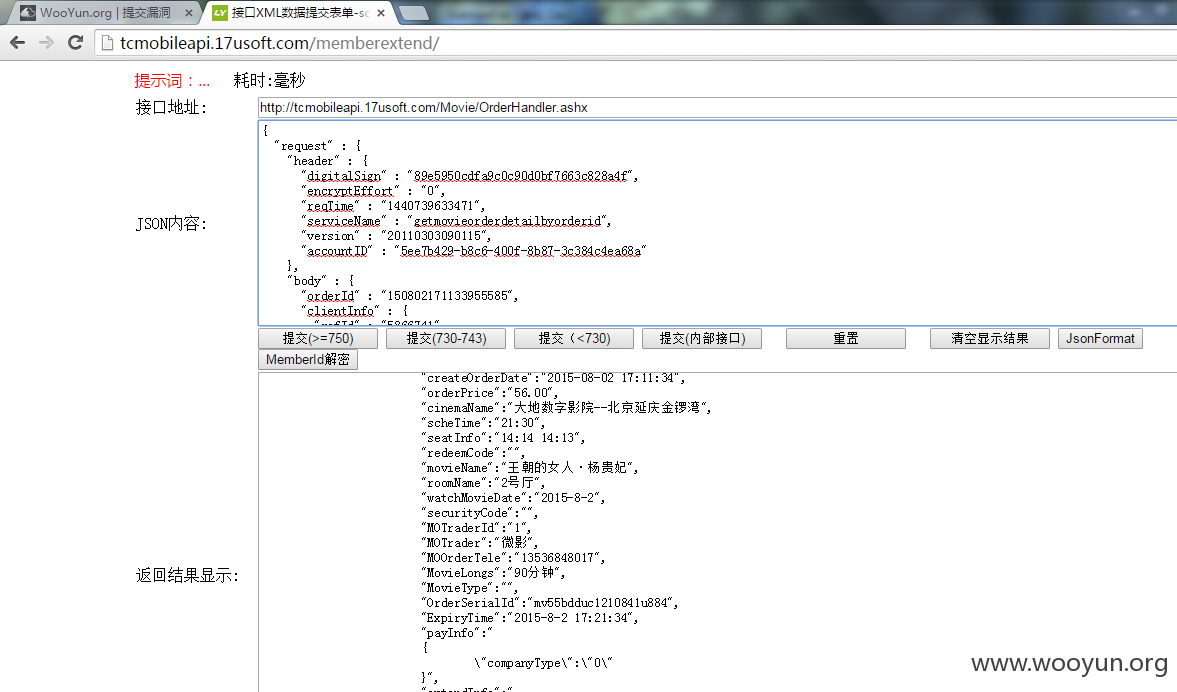
3.电影接口地址:http://tcmobileapi.17usoft.com/Movie/OrderHandler.ashx
JSON
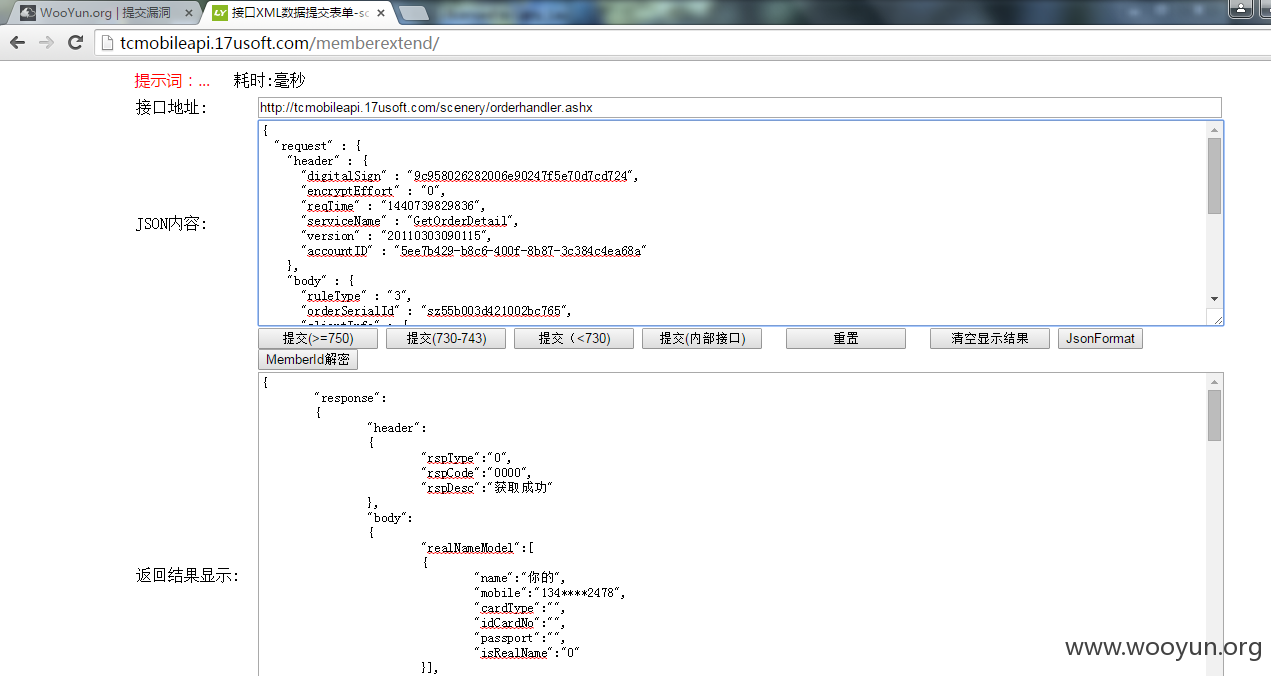
4.旅游接口地址:http://tcmobileapi.17usoft.com/scenery/orderhandler.ashx
JSON
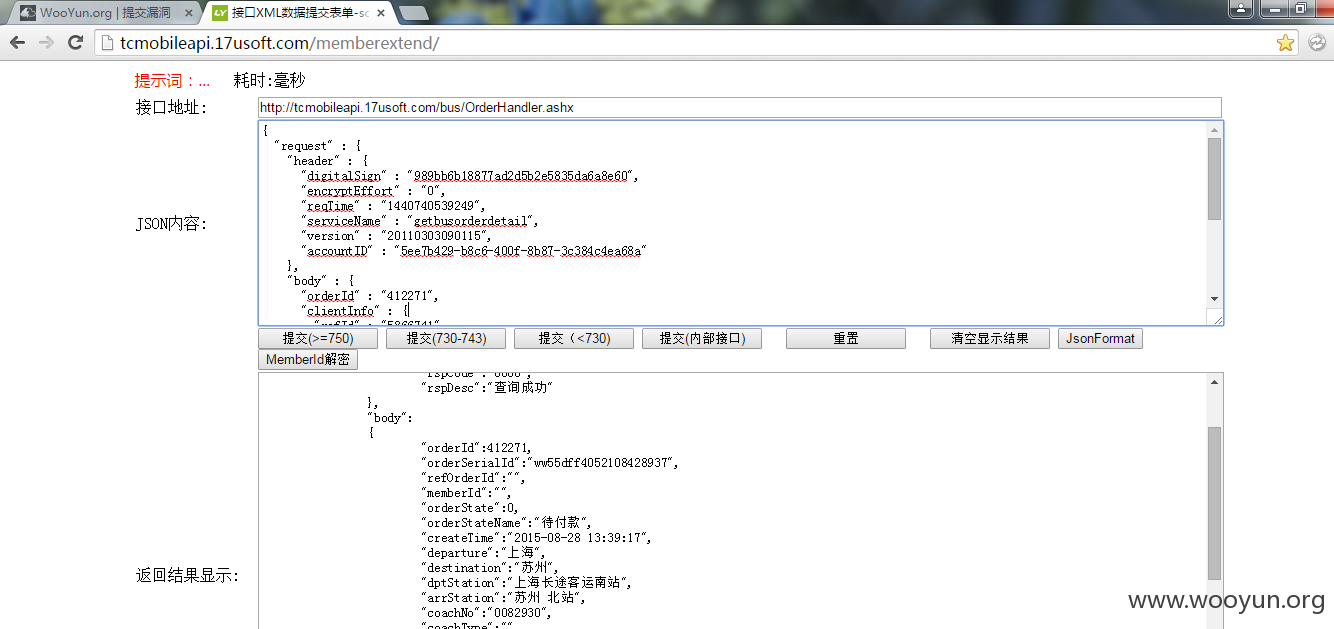
5汽车票接口地址:http://tcmobileapi.17usoft.com/bus/OrderHandler.ashx
JSON
还有其他接口我就不测试了 你比我还懂的
漏洞证明:
羞羞的
修复方案:
..........
版权声明:转载请注明来源 1937nick@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:3
确认时间:2015-08-28 23:11
厂商回复:
感谢关注同程旅游,第一个接口测试页面没什么影响,只是为了方便调试接口,不过还是限制下。洞主后面列的这些本来就是APP中间层的接口啊,要不然客户端信息从哪儿查。接口都是验证签名的,不花时间逆向客户端也无法伪造请求签名,洞主也没有提到越权查看其他人的信息的问题,我没看懂危害在哪里?
最新状态:
2015-08-28:调试页面已删,但是这种没什么影响的,抱歉,给不了高rank和礼品卡。
2015-08-29:这个漏洞因为沟通的原因产生了一些误会,在此道歉。因为调试页面删除了不好按洞主提交时的测试方式复现,周一我们会在测试环境测试,如果确实存在问题我们会补上rank和礼品卡。