漏洞概要
关注数(24)
关注此漏洞
漏洞标题:艺龙旅行网某平台Padding Oracle Vulnerability信息泄露漏洞
提交时间:2015-03-12 18:10
修复时间:2015-04-26 18:10
公开时间:2015-04-26 18:10
漏洞类型:敏感信息泄露
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-03-12: 细节已通知厂商并且等待厂商处理中
2015-03-12: 厂商已经确认,细节仅向厂商公开
2015-03-22: 细节向核心白帽子及相关领域专家公开
2015-04-01: 细节向普通白帽子公开
2015-04-11: 细节向实习白帽子公开
2015-04-26: 细节向公众公开
简要描述:
艺龙旅行网某平台Padding Oracle Vulnerability信息泄露漏洞
详细说明:
用猪猪侠的wydomain扫二级域名扫出来个corp.elong.com
凭经验猜想应该很多系统平台会在这个域名下,于是,百度corp.elong.com
找出来个
http://elearning.corp.elong.com/
在线学习平台
顺手看了下源代码,发现存在
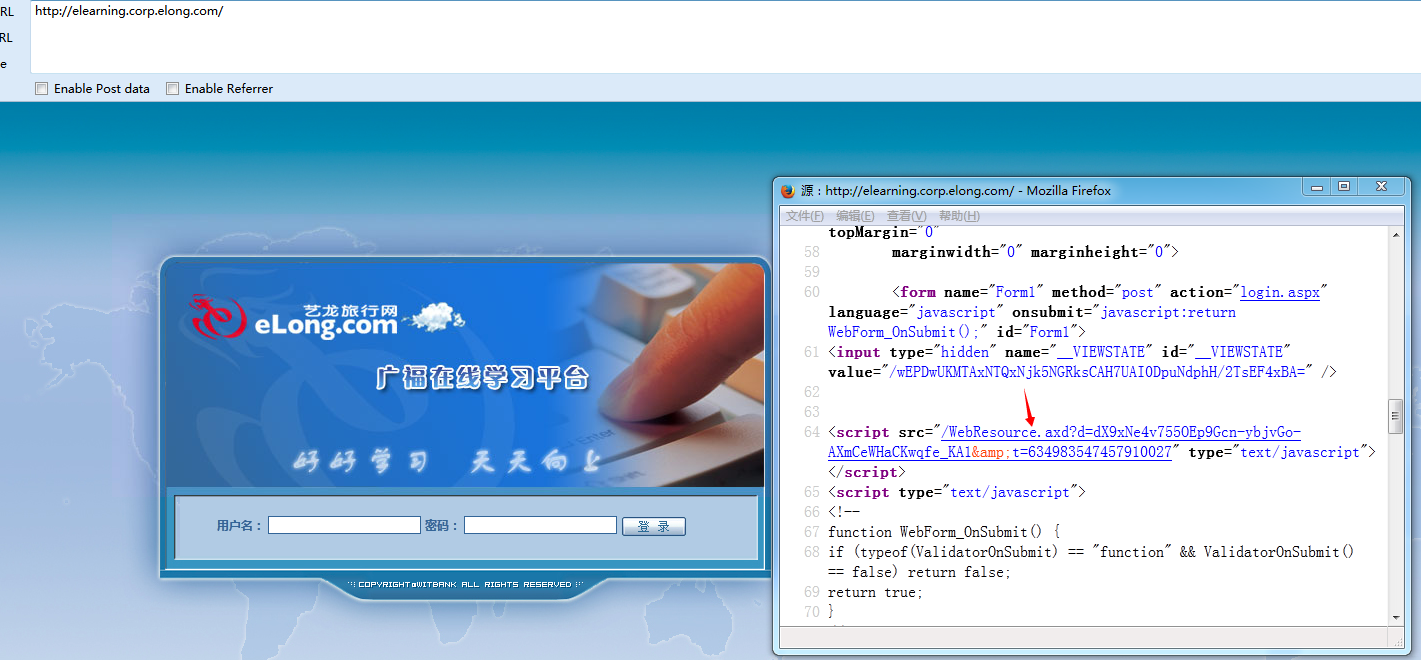
于是测试一下看是否存在Padding Oracle Vulnerability信息泄露漏洞,一试还真有.
漏洞证明:
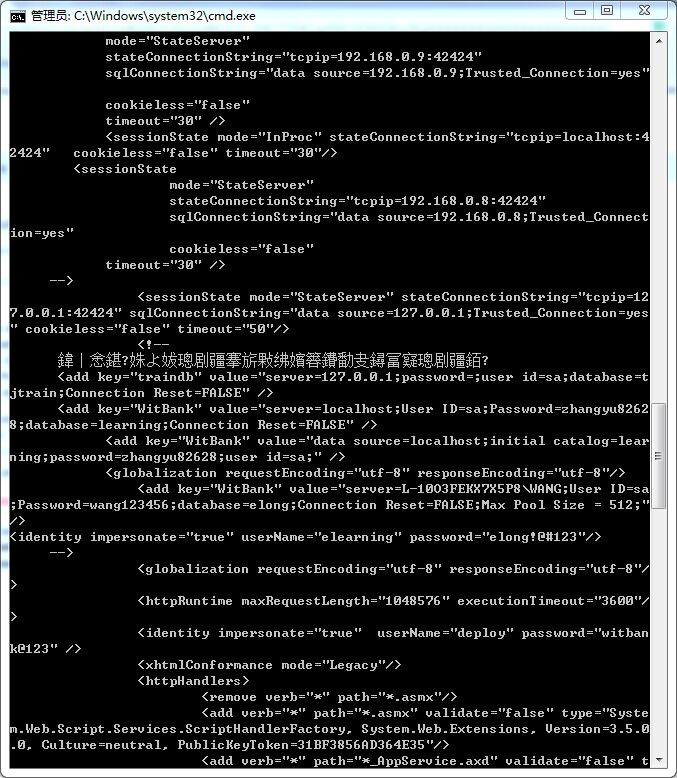
跑最后这一步实在太久了,晚上睡觉的时候开始跑,跑到下午才跑出来
修复方案:
版权声明:转载请注明来源 几何黑店@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:5
确认时间:2015-03-12 20:05
厂商回复:
多谢白帽子提醒,我们会尽快修复。
最新状态:
暂无




