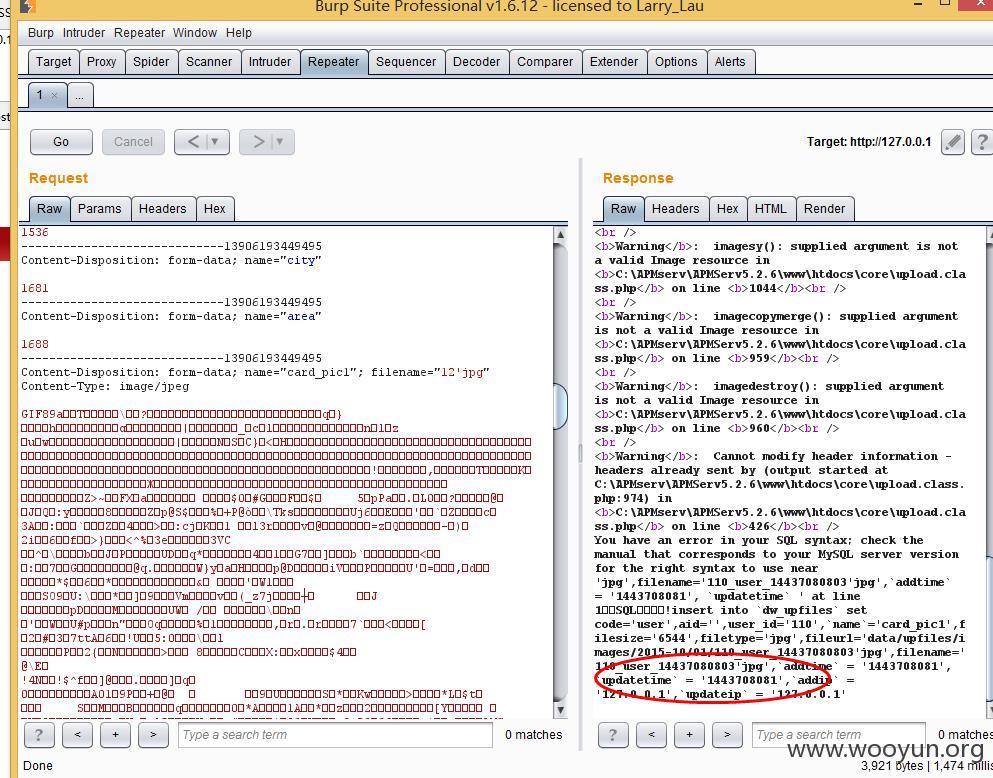
出现在upload文件上
可以看到文件名没有验证然后带入sql查询
跟踪下在哪里调用了
在module/user/user.inc.php中
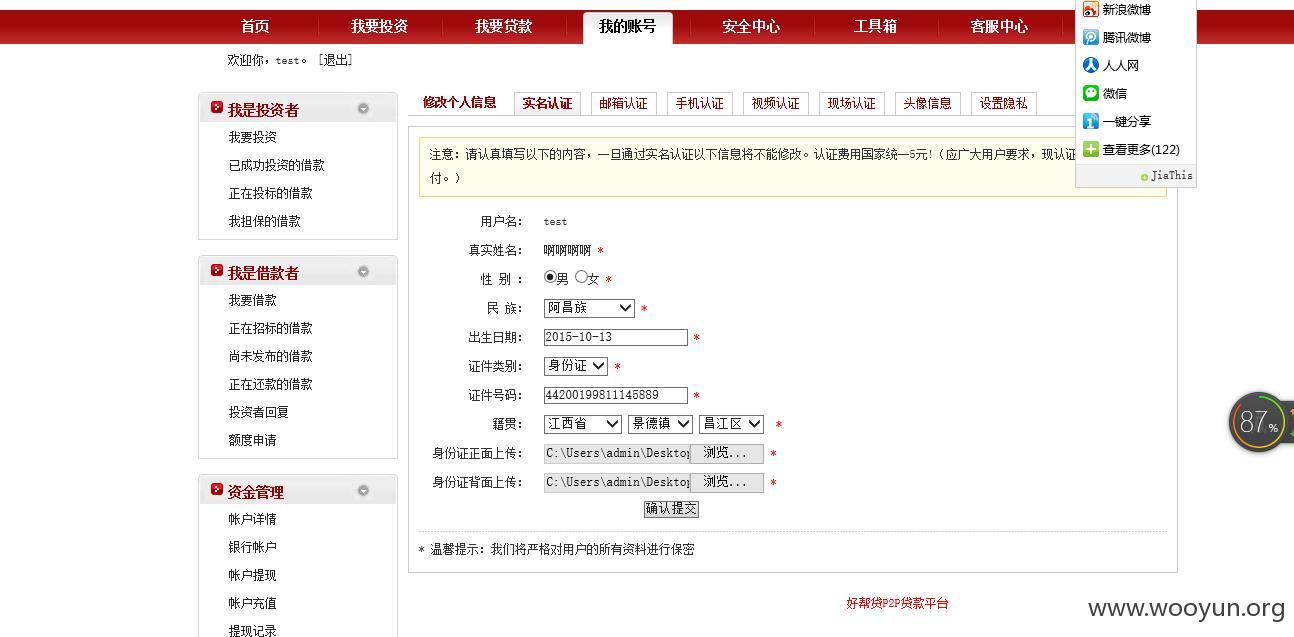
实名认证那里
因为是FILE数组所以不受gpc/waf
我们测试下带入单引号
http://127.0.0.1/index.php?user&q=code/user/realname
抓包修改提交,看看报错
出现在upload文件上
可以看到文件名没有验证然后带入sql查询
跟踪下在哪里调用了
在module/user/user.inc.php中
实名认证那里
因为是FILE数组所以不受gpc/waf
我们测试下带入单引号
http://127.0.0.1/index.php?user&q=code/user/realname

抓包修改提交,看看报错





