漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0100986
漏洞标题:phpems多处水平权限漏洞可进行订单操作
相关厂商:phpems
漏洞作者: 路人甲
提交时间:2015-03-12 18:47
修复时间:2015-04-30 18:48
公开时间:2015-04-30 18:48
漏洞类型:非授权访问/权限绕过
危害等级:高
自评Rank:10
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-12: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-04-30: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
phpems多处水平权限漏洞可进行订单操作
详细说明:
3.网站多处存在平行权限漏洞
存在漏洞的代码位置在/app/user/center.php的payfor()函数中
public function payfor()
{
$subaction = $this->ev->url(3);
$orderstatus = array(1=>'待付款',2=>'已完成',99=>'已撤单');
$this->tpl->assign('orderstatus',$orderstatus);
switch($subaction)
{
case 'remove':
$oid = $this->ev->get('ordersn');
$order = $this->order->getOrderById($oid);
if($order['orderstatus'] == 1)
{
$this->order->delOrder($oid);
$message = array(
'statusCode' => 200,
"message" => "订单删除成功",
"callbackType" => 'forward',
"forwardUrl" => "reload"
);
}
else
$message = array(
'statusCode' => 300,
"message" => "订单操作失败"
);
exit(json_encode($message));
break;
case 'orderdetail':
$oid = $this->ev->get('ordersn');
if(!$oid)exit(header("location:index.php?user-center"));
$order = $this->order->getOrderById($oid);
$alipay = $this->G->make('alipay');
$payforurl = $alipay->outPayForUrl($order,WP.'index.php?route=user-api-alipaynotify',WP.'index.php?route=user-api-alipayreturn');
$this->tpl->assign('payforurl',$payforurl);
$this->tpl->assign('order',$order);
$this->tpl->display('payfor_detail');
break;
default:
if($this->ev->get('payforit'))
{
$money = intval($this->ev->get('money'));
if($money < 1)
{
$message = array(
'statusCode' => 300,
"message" => "最少需要充值1元"
);
exit(json_encode($message));
}
$args = array();
$args['orderprice'] = $money;
$args['ordertitle'] = "考试系统充值 {$args['orderprice']} 元";
$args['ordersn'] = date('YmdHi').rand(100,999);
$args['orderstatus'] = 1;
$args['orderuserid'] = $this->_user['sessionuserid'];
$args['ordercreatetime'] = TIME;
$args['orderuserinfo'] = array('username' => $this->_user['sessionusername']);
$this->order->addOrder($args);
$message = array(
'statusCode' => 200,
"message" => "订单创建成功",
"callbackType" => 'forward',
"forwardUrl" => "index.php?user-center-payfor-orderdetail&ordersn=".$args['ordersn']
);
exit(json_encode($message));
}
else
{
$page = $this->ev->get('page');
$args = array();
$args = "orderuserid = '".$this->_user['sessionuserid']."'";
$myorders = $this->order->getOrderList($args,$page);
$this->tpl->assign('orders',$myorders);
$this->tpl->display('payfor');
}
}
}
该函数switch中的前两个条件一个是用于删除订单,一个用于查看订单细节,进入具体代码
case 'remove':
$oid = $this->ev->get('ordersn');
$order = $this->order->getOrderById($oid);//这里的提交oid可以由URL参数ordersn指定
if($order['orderstatus'] == 1)
{
$this->order->delOrder($oid);
$message = array(
'statusCode' => 200,
"message" => "订单删除成功",
"callbackType" => 'forward',
"forwardUrl" => "reload"
);
}
else
$message = array(
'statusCode' => 300,
"message" => "订单操作失败"
);
exit(json_encode($message));
break;
case 'orderdetail':
$oid = $this->ev->get('ordersn');
if(!$oid)exit(header("location:index.php?user-center"));
$order = $this->order->getOrderById($oid);//这里的oid也可以由URL参数ordersn指定
$alipay = $this->G->make('alipay');
$payforurl = $alipay->outPayForUrl($order,WP.'index.php?route=user-api-alipaynotify',WP.'index.php?route=user-api-alipayreturn');
$this->tpl->assign('payforurl',$payforurl);
$this->tpl->assign('order',$order);
$this->tpl->display('payfor_detail');
break;
无论是删除订单还是查看订单细节他们的条件变量都是用户可控的,就是说可以在URL参数中人为指定,因而导致了平行权限的问题,直接结果就是可以遍历用户订单和删除任意用户订单。
验证:
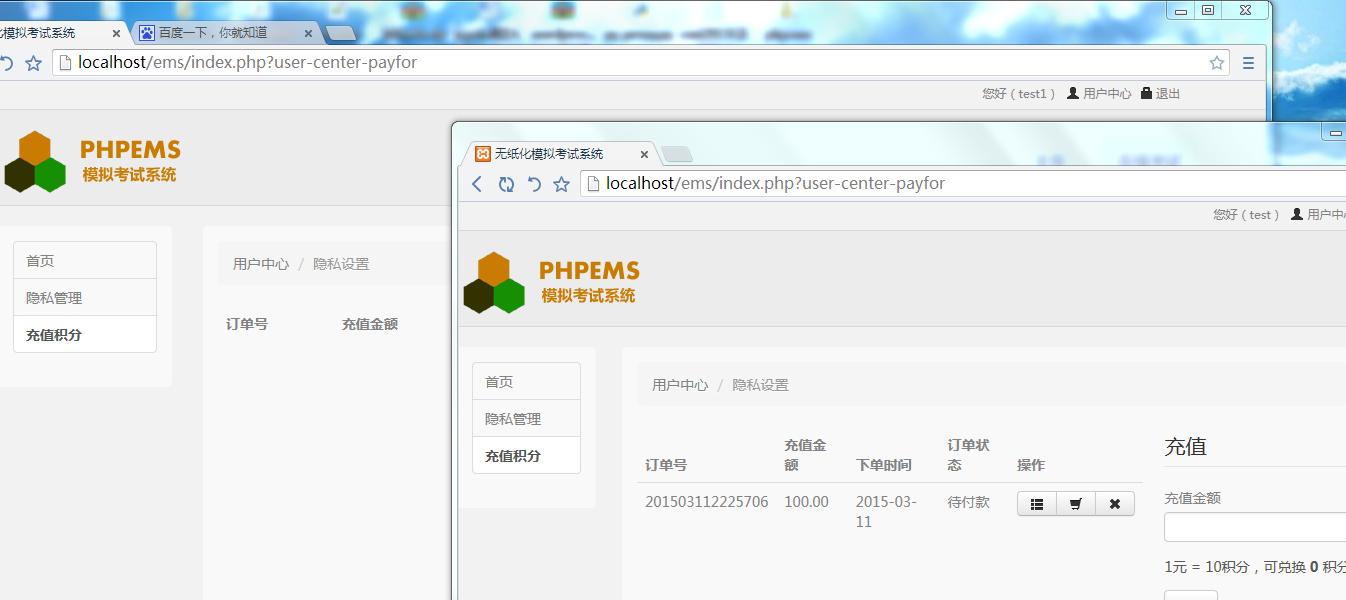
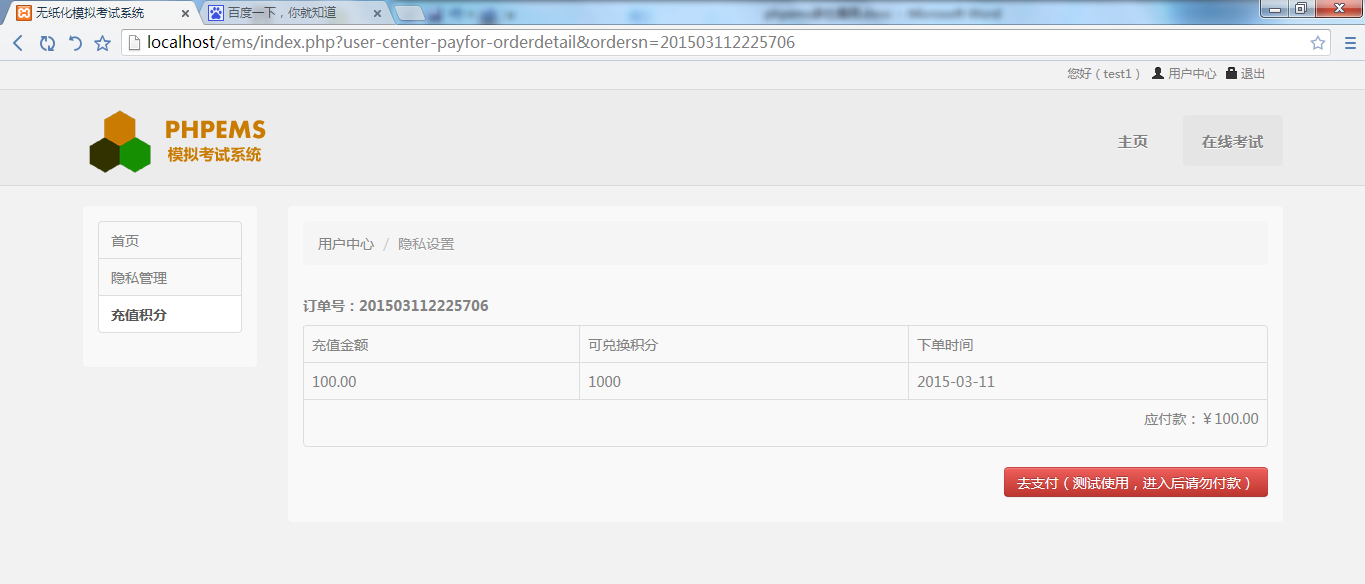
注册两个用户,test和test1 test有一封订单,test1没有
但现在以test1用户访问链接
可以看到test1用户看到了test用户的订单,OVER!
漏洞证明:
修复方案:
增强逻辑验证起码加上_session[username]
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝