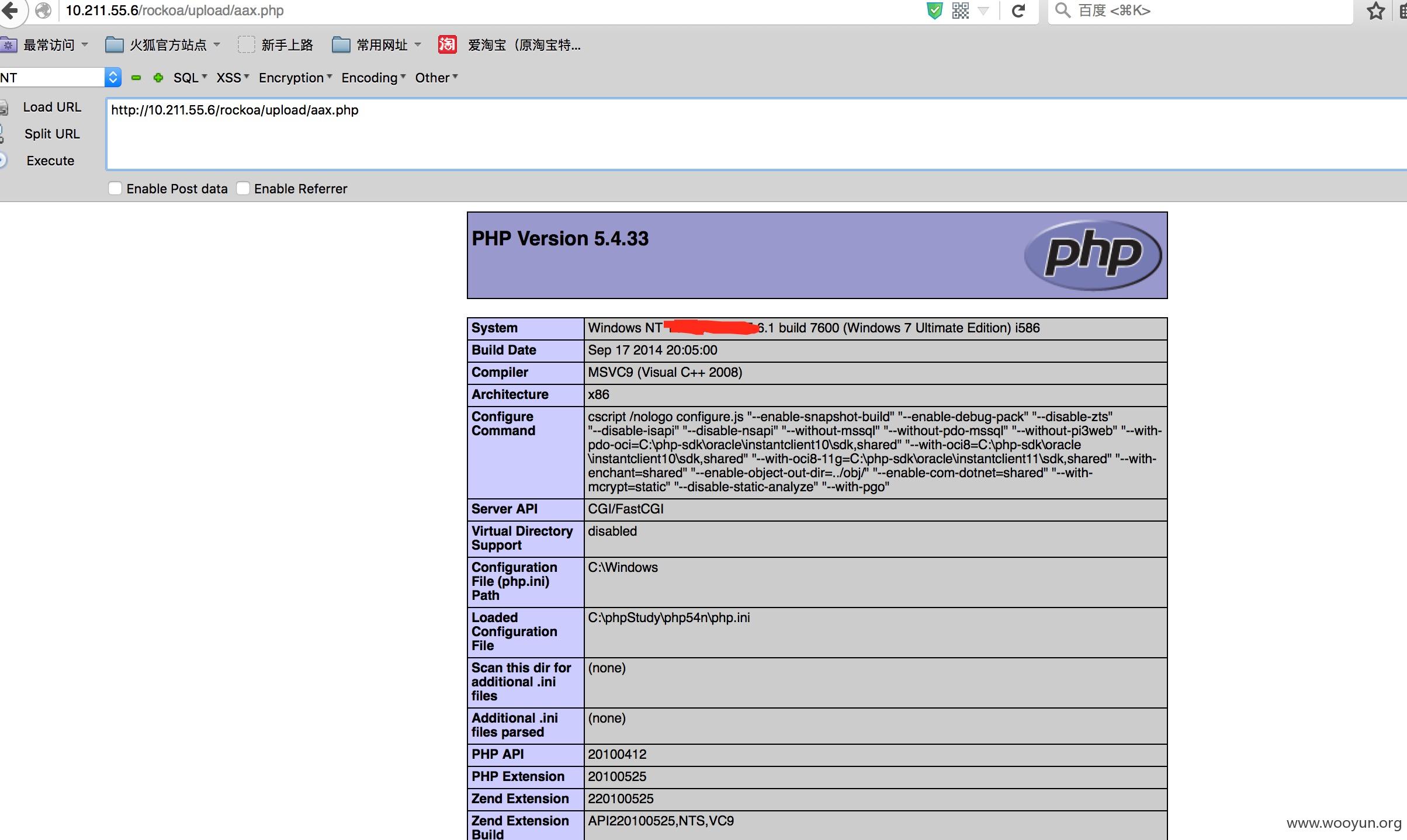
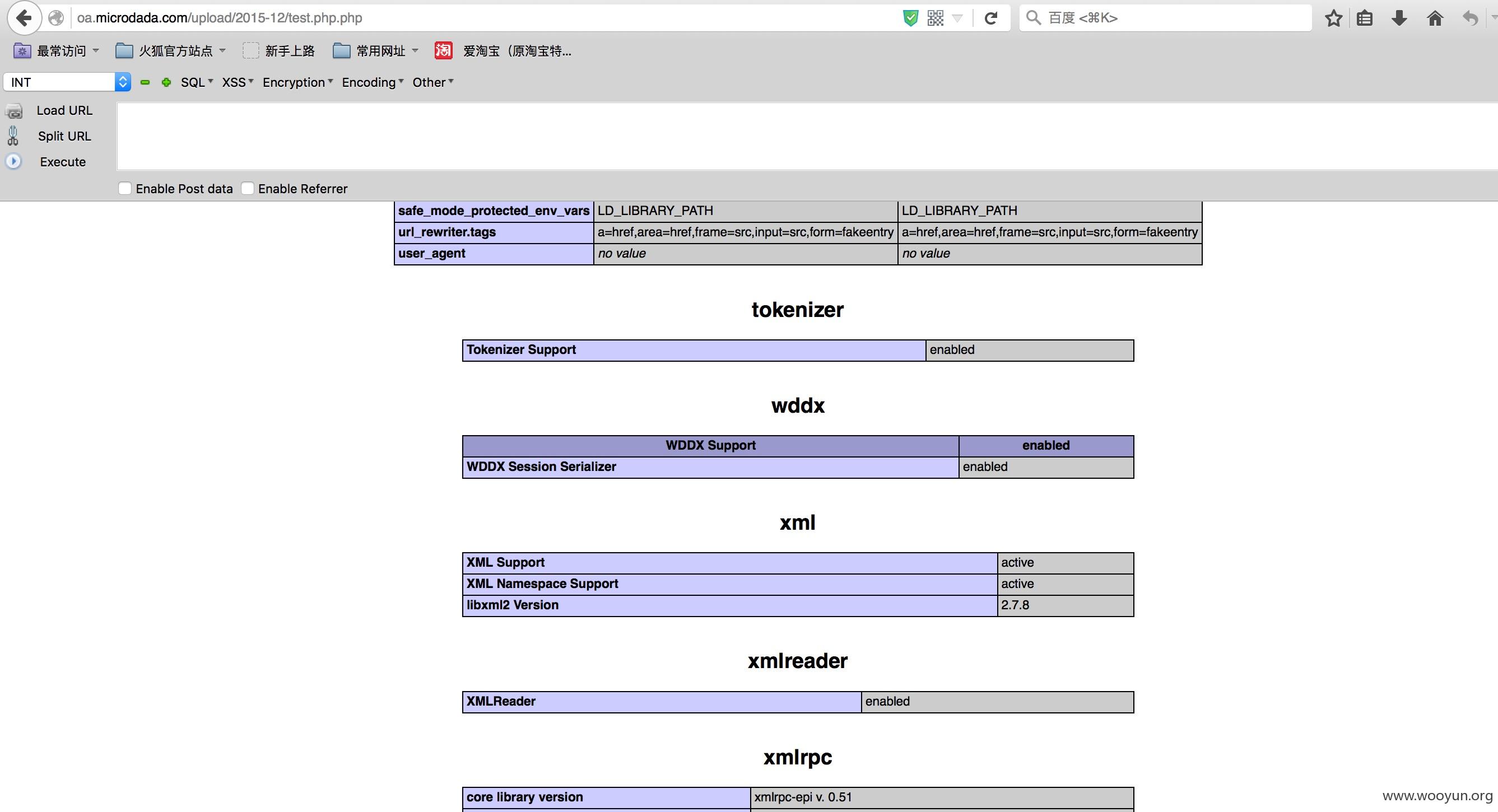
0x01 后台bypass
C:/phpStudy/WWW/rockoa/webrock/login/loginAction.php
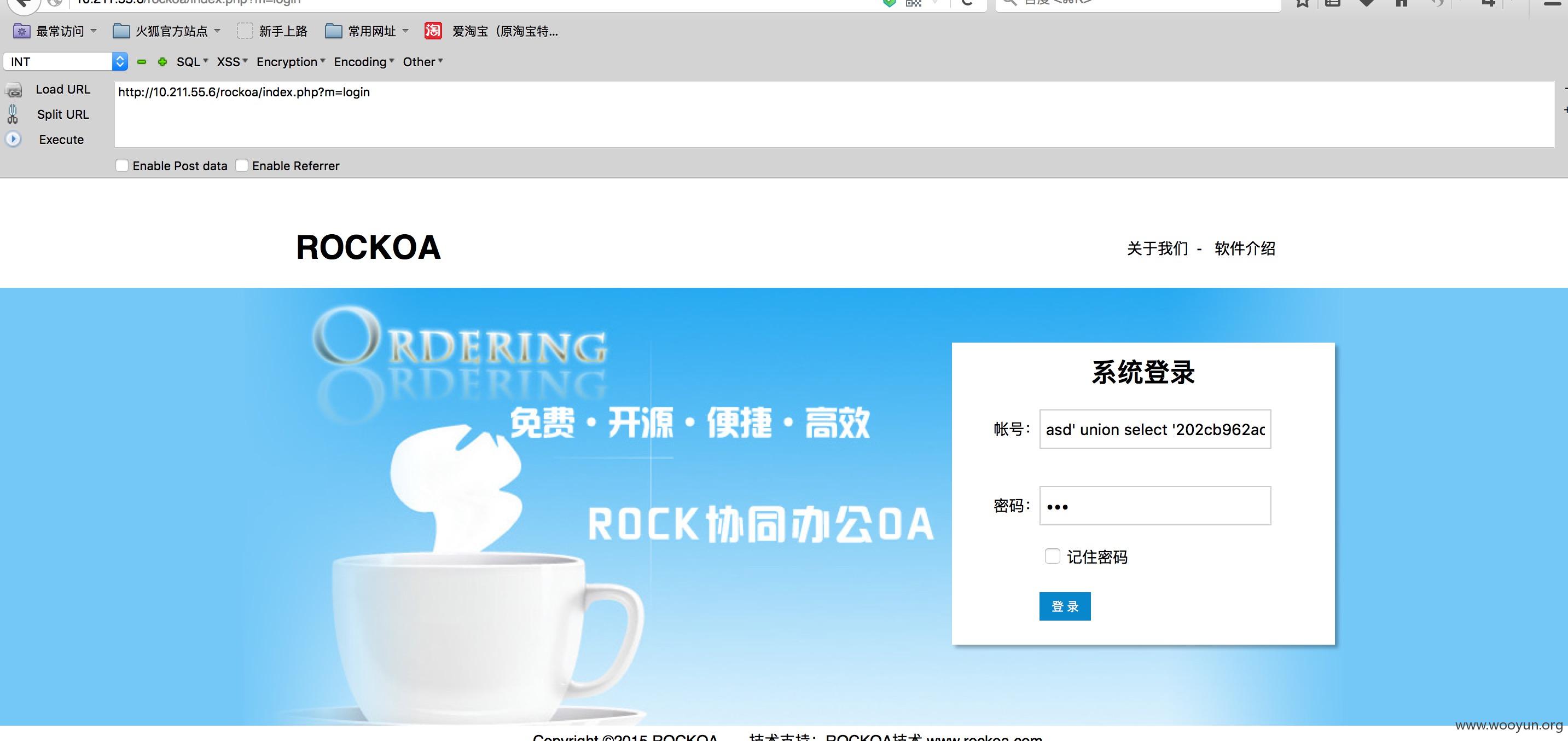
在登陆的地方存在注入,但是会验证一次密码,所以我们通过union select 型的注入直接bypass,进入后台。
构造adminuser为
adminpass为123
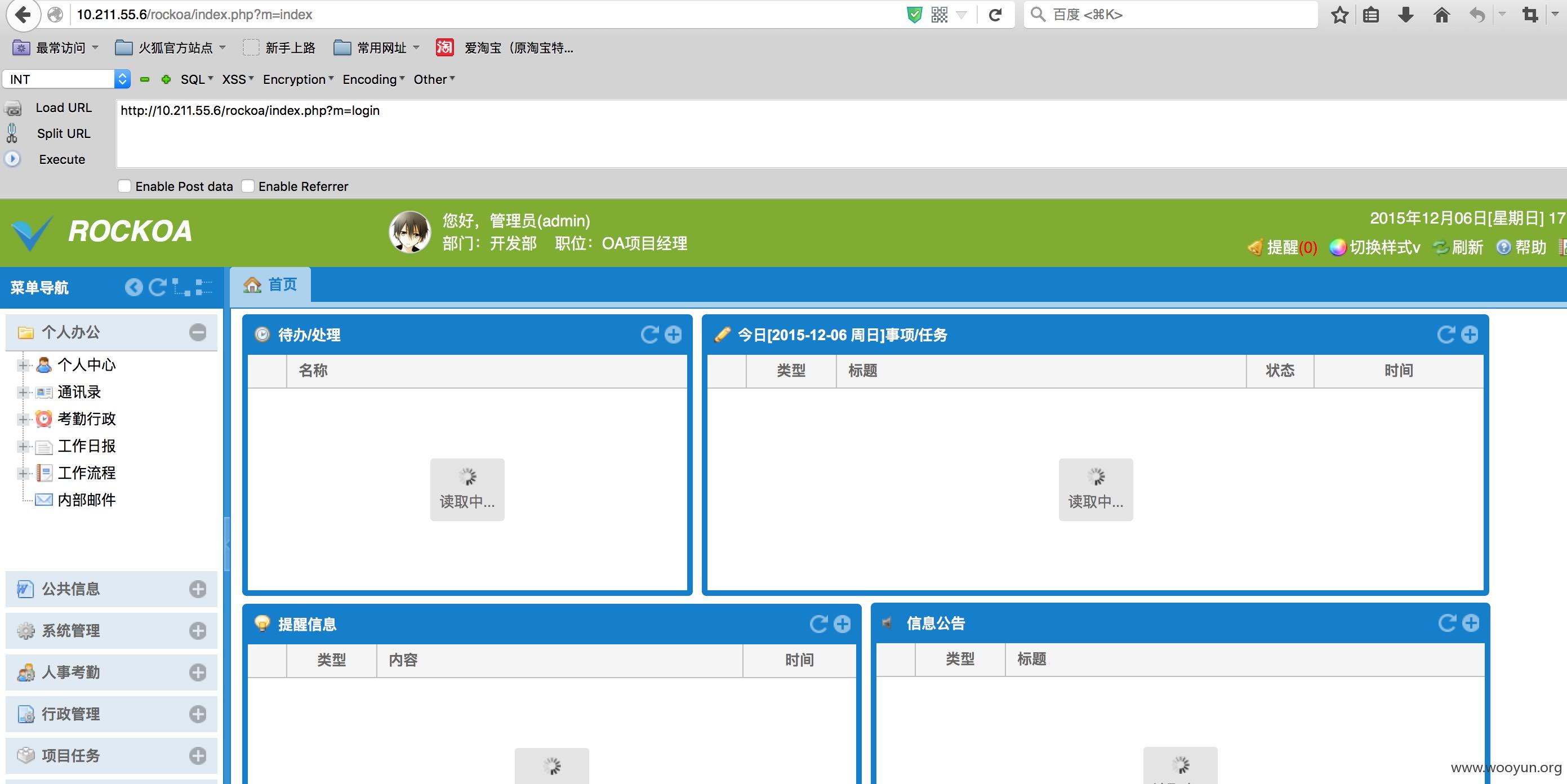
这样就可以直接进入后台了。
0x02 Getshell
第一种情况 需要登录,然后无限制getshell
C:/phpStudy/WWW/rockoa/mode/upload/uploadajax.php
这段代码的意思就是先生成一个temp文件,其中内容是base64过的,然后从temp文件里面读取内容并且base64解码一次,然后写入文件中。
其中savepath和filename变量我们都可以控制,这样就可以写shell了。
在进入这个流程之前,还有两个逻辑判断要izztbo变量为真 boolc1变量为假
其中if(!$boolc1 || $botxtl)$izztbo = true; 只要一个为真就行,由于boolc1又savepath是否为空的来,我们只要给savepath赋值即可。最好构造这样的数据包
就可以在upload下生成一个aax.php的shell
第二种情况 无需登录,但是有限制条件
由于没有登录所以$optid = (int)$rock->session(QOM.'adminid',0);获取的opted的值为0 在后面这个判断if(!$boolc1 && $optid==0)$boolc1 = true;导致boolc1为真,所以后面的流程都不能进去,就只能写一个tempfile 了,由于$tempfile = $allfile.'.temp'; 所以只能配合apache的解析漏洞或者iis的解析漏洞利用了,直接构造数据包
然后生成
随便测试了一个