中兴能源
http://www.zte-e.com/
注射点(搜索页面,其他页面参数都做了类型转换,本来以为没希望了,但发现搜索页面输入'时报错,通过报错页面发现搜索关键字未处理输入类型和特殊字符):
http://www.zte-e.com/cn/Search.aspx?Keyword='
共264个数据库
选择zte1314库,获取表
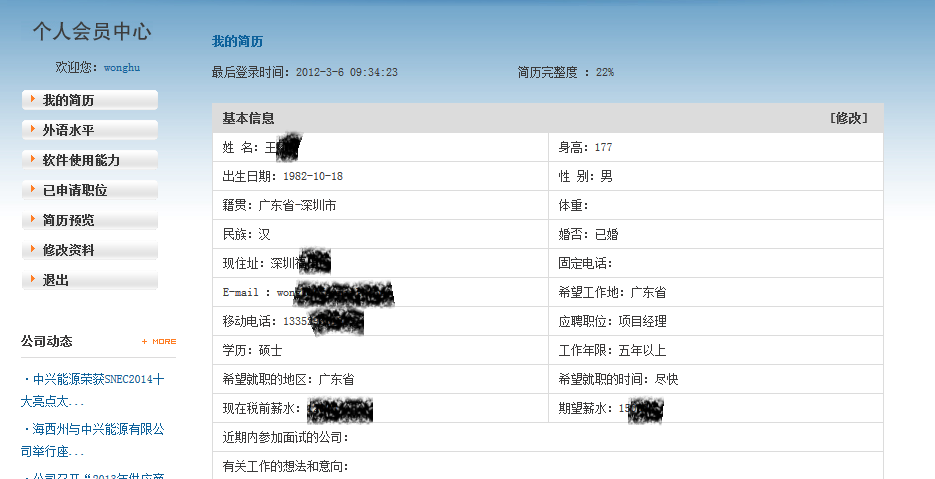
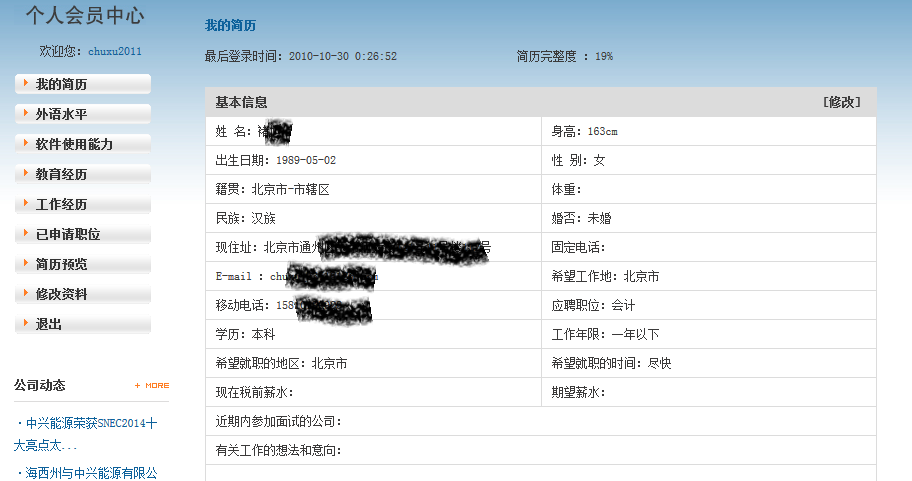
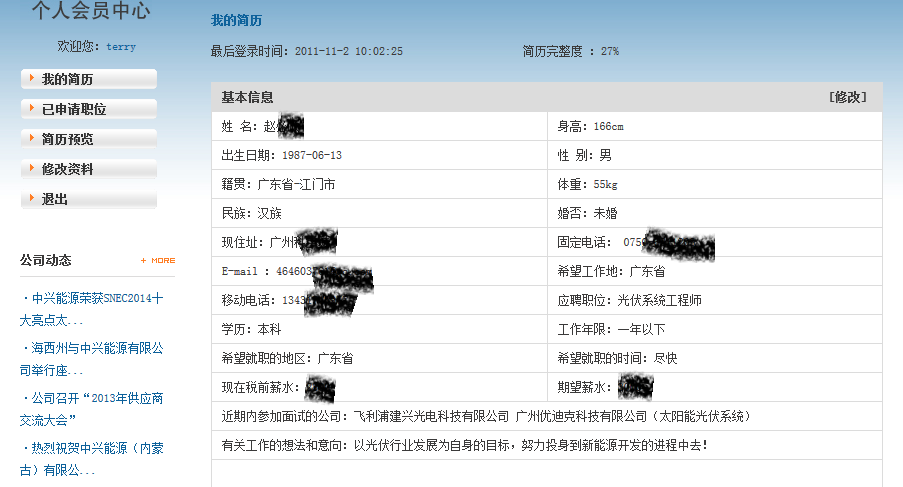
通过zte1314.Member获取会员用户名和密码,上千条记录都是求职简历,账号、密码、姓名、邮箱、手机、薪资、住址等齐全。。。
通过账号、密码可任意修改用户简历。
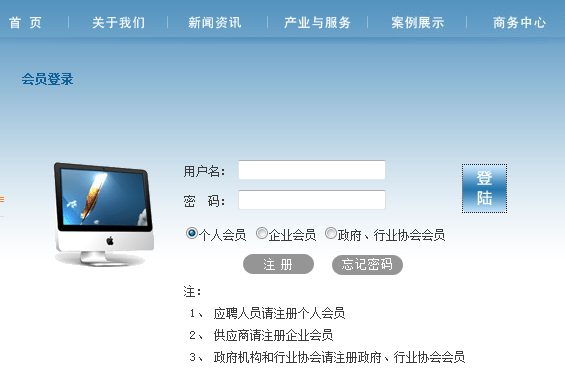
可直接点击登录查看。。。。
获取zte1314.SysA_Admin表中的管理员用户名和密码。
这里发现管理员账号后台弱口令
登陆后台 http://www.zte-e.com/manage/AdminLogin.aspx
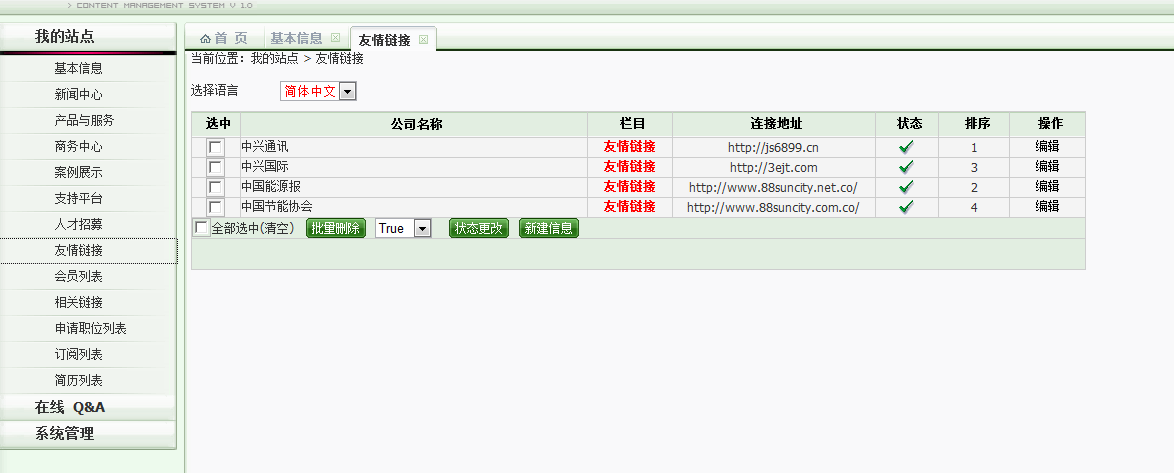
搞笑的是,这里中兴通讯的友情链接地址居然不是官方链接。。。
由于屏蔽了upload访问权限,获取不了webshell。
共264个数据库
选择zte1314库,获取表
通过zte1314.Member获取会员用户名和密码,上千条记录都是求职简历,账号、密码、姓名、邮箱、手机、薪资、住址等齐全。。。
通过账号、密码可任意修改用户简历。
可直接点击登录查看。。。。




获取zte1314.SysA_Admin表中的管理员用户名和密码。
这里发现管理员账号后台弱口令
登陆后台 http://www.zte-e.com/manage/AdminLogin.aspx

搞笑的是,这里中兴通讯的友情链接地址居然不是官方链接。。。
由于屏蔽了upload访问权限,获取不了webshell。
此外,通过旁注扫描,同IP地址上的网站普遍存在sql注入。







