漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0156219
漏洞标题:苏宁多站多处运维不当(涉及CDN\IM部署\后台绕过\Redis未授权访问等)
相关厂商:江苏苏宁易购电子商务有限公司
漏洞作者: _Thorns
提交时间:2015-11-27 13:37
修复时间:2016-01-11 15:32
公开时间:2016-01-11 15:32
漏洞类型:敏感信息泄露
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-27: 细节已通知厂商并且等待厂商处理中
2015-11-27: 厂商已经确认,细节仅向厂商公开
2015-12-07: 细节向核心白帽子及相关领域专家公开
2015-12-17: 细节向普通白帽子公开
2015-12-27: 细节向实习白帽子公开
2016-01-11: 细节向公众公开
简要描述:
苏宁多站多处运维不当(涉及CDN\IM部署\后台绕过\Redis未授权访问等)
详细说明:
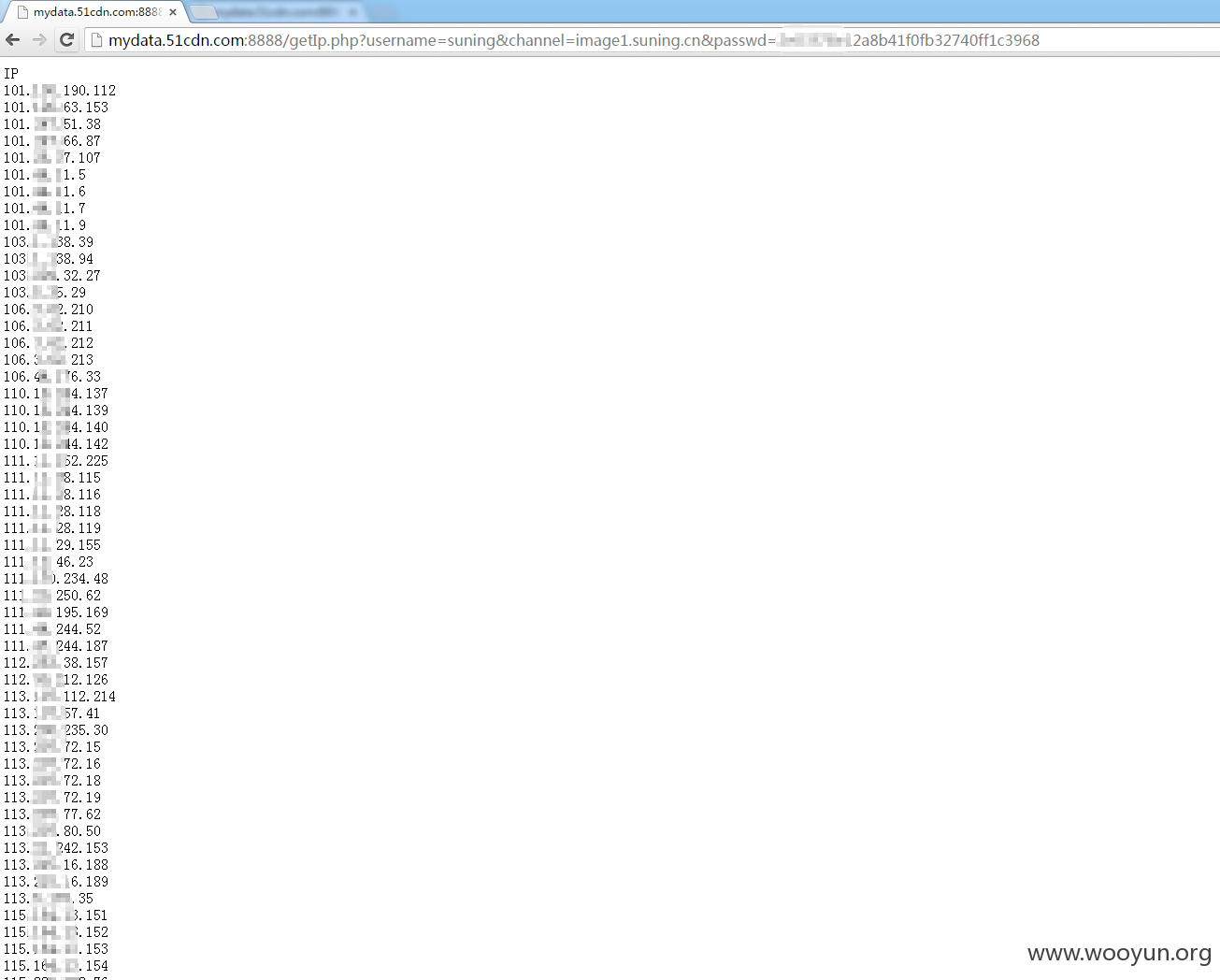
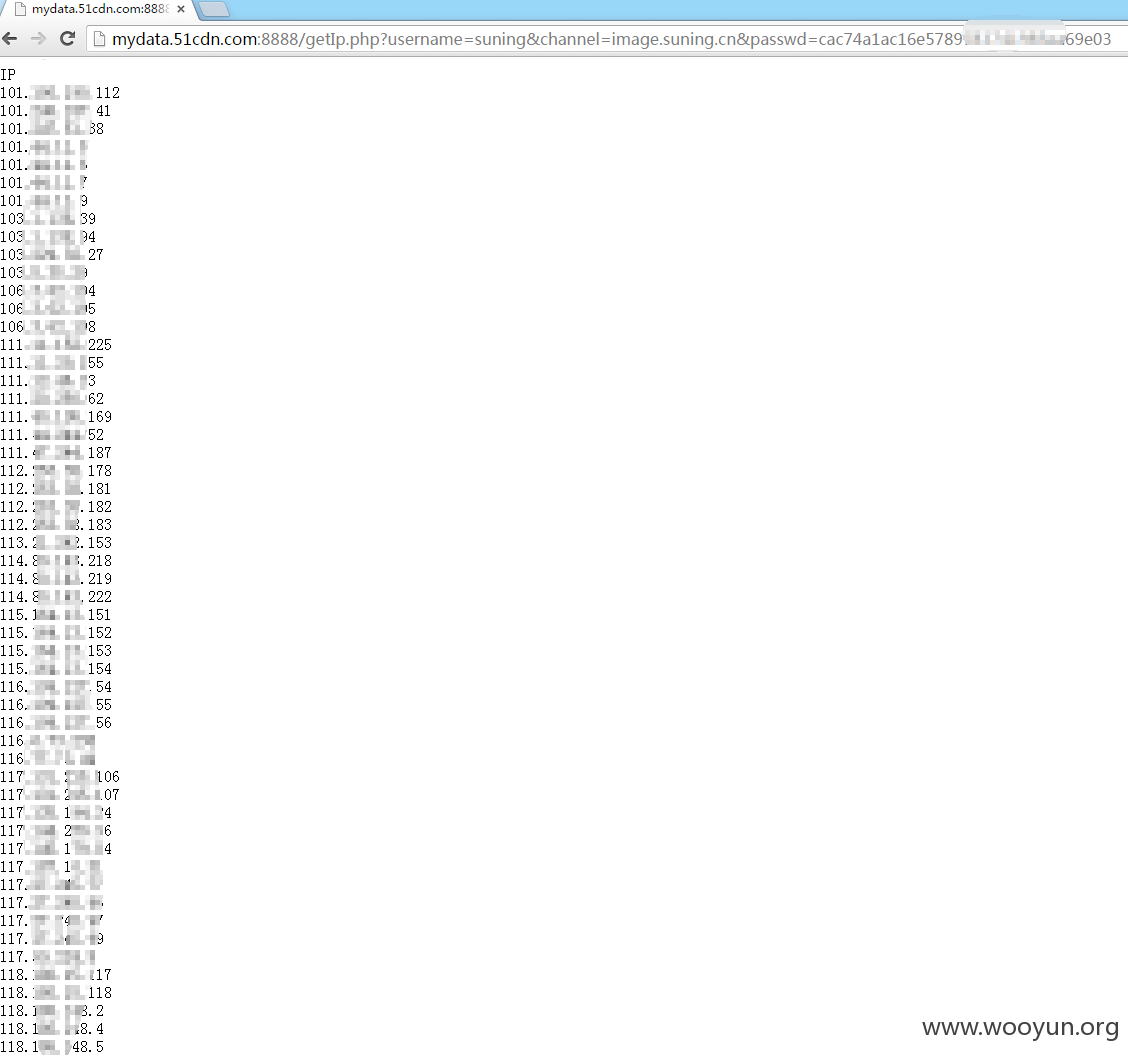
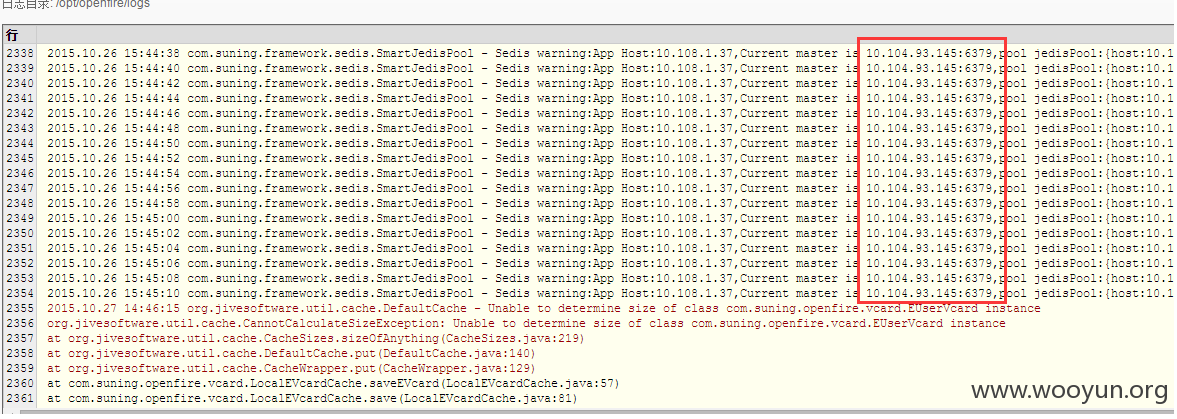
1.http://mydata.51cdn.com:8888/getIp.php?sername=suning&channel=www.suning.cn&passwd=6b3454d97580487b40******2c9d1b5c
http://mydata.51cdn.com:8888/getIp.php?username=suning&channel=image.suning.cn&passwd=cac74a1ac16e578******1985ea69e03
http://mydata.51cdn.com:8888/getIp.php?username=suning&channel=image1.suning.cn&passwd=2e03f78e12a8b4******2740ff1c3968
密码打码了,放心!~
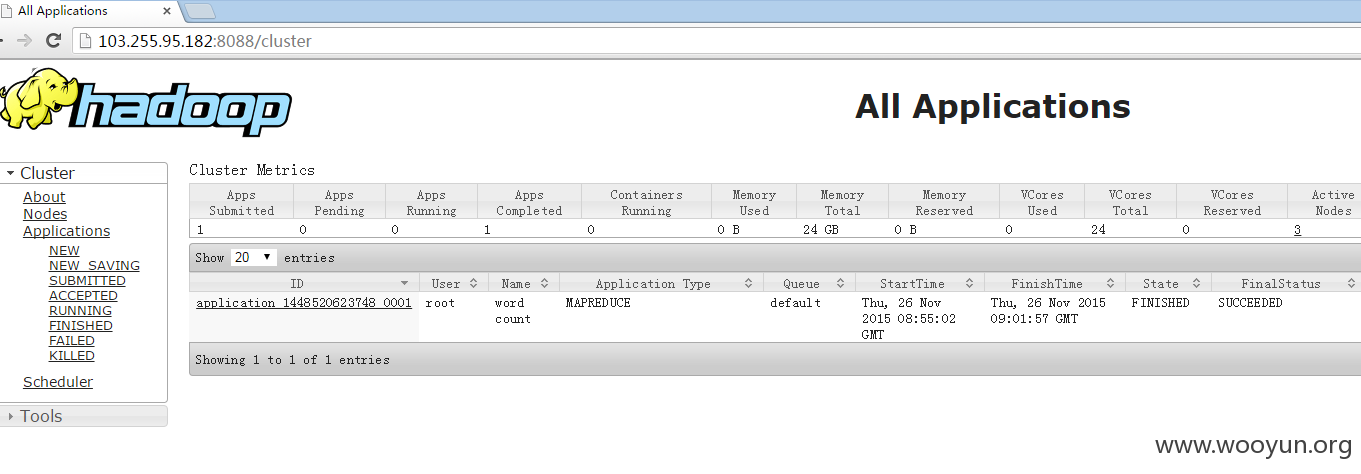
http://103.255.95.182:8088
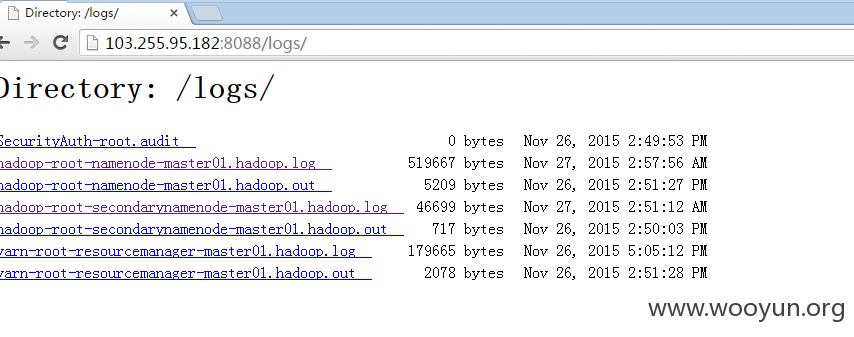
http://103.255.95.182:8088/logs/hadoop-root-namenode-master01.hadoop.log
漏洞证明:
2.这次的主角是我在对IP进行C扫描的时候无意发现苏宁核心服务器部署服务器
http://58.240.86.233:8888/
包含的系统有:
PQCS叫号机系统/
RF优化项目/
UED分享-2014-08-26/
其他非ITP项目/
物流监控平台/
物流移动工作站项目/
物流门户/
自提柜应用提升项目/
自提管理平台/
苏宁物流开放平台物流服务项目/
东西太多,不截那么多图了。
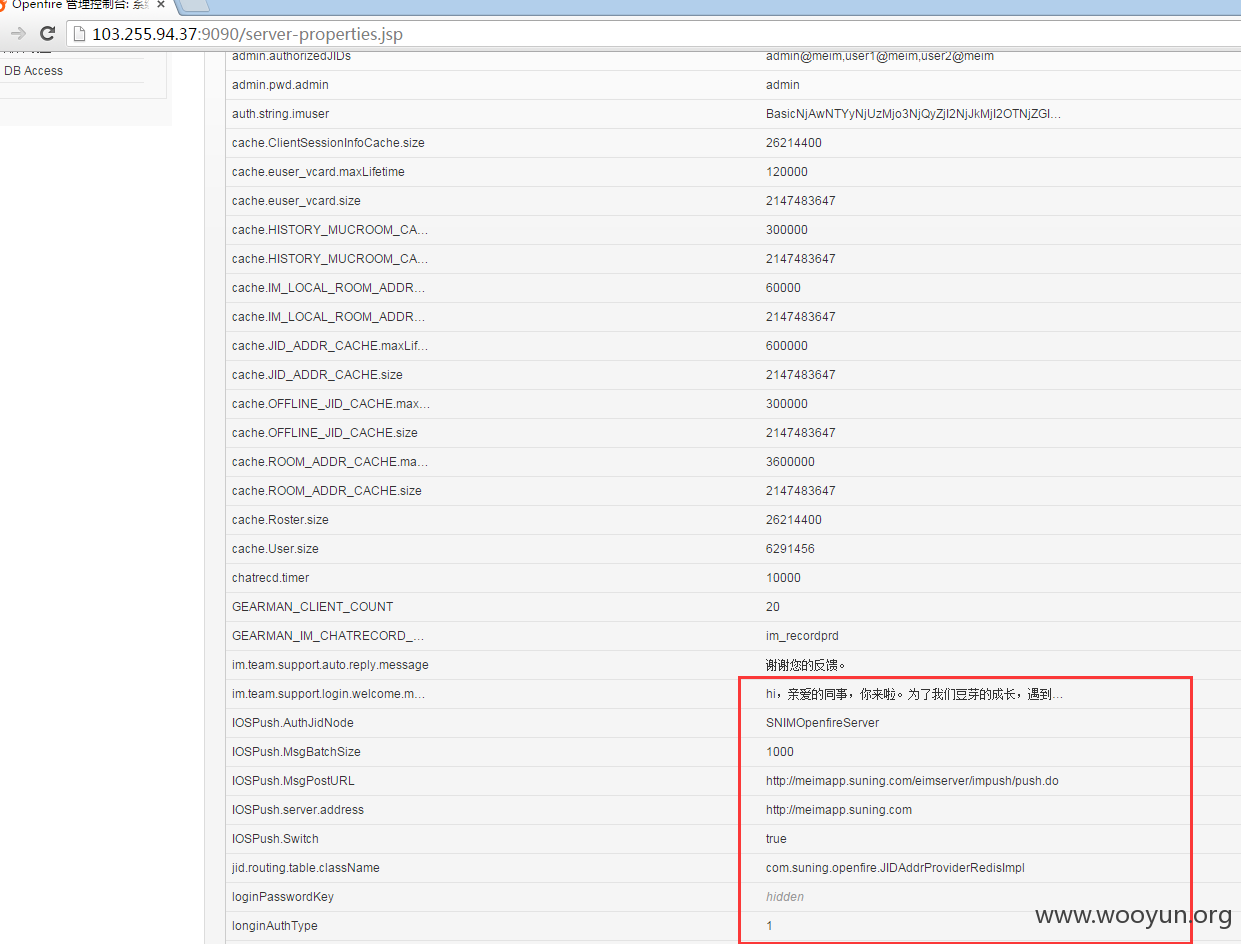
3.http://103.255.94.37:9090/index.jsp
http://103.255.94.36:9090/index.jsp
http://103.255.94.38:9090/index.jsp
http://103.255.94.39:9090/index.jsp
http://103.255.94.40:9090/index.jsp
http://103.255.94.41:9090/index.jsp
admin admin
域 远程服务器端口 删除
1 10.108.1.39 5269
2 10.108.1.37 5269
3 10.108.1.64 5269
4 10.108.1.63 5269
5 10.108.1.62 5269
6 10.108.1.61 5269
7 meim 5269
8 conference.meim 5269
9 pa.meim 5269
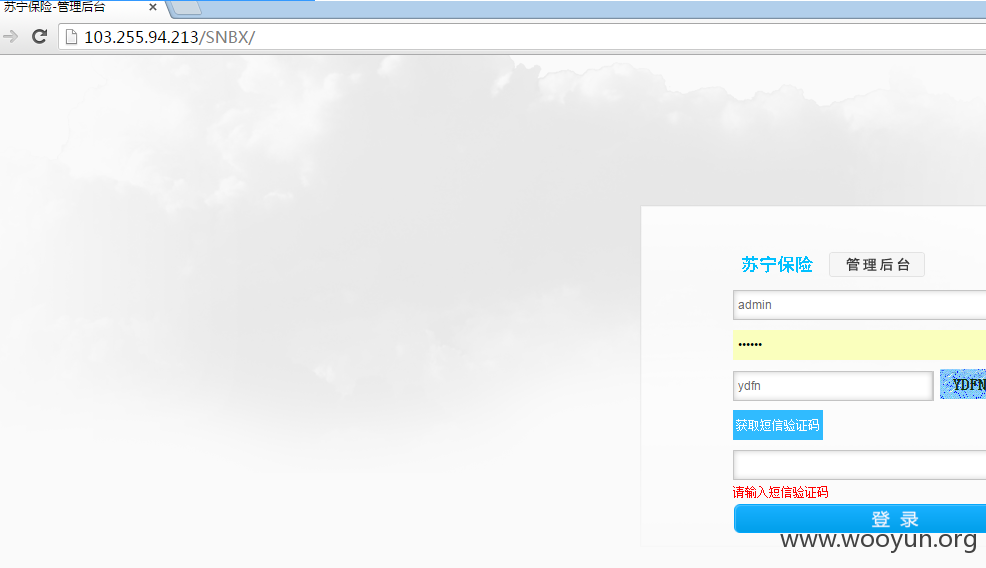
4.http://103.255.94.213/SNBX/
之前是存在弱口令,后来改成了这样,需要获取短信验证码
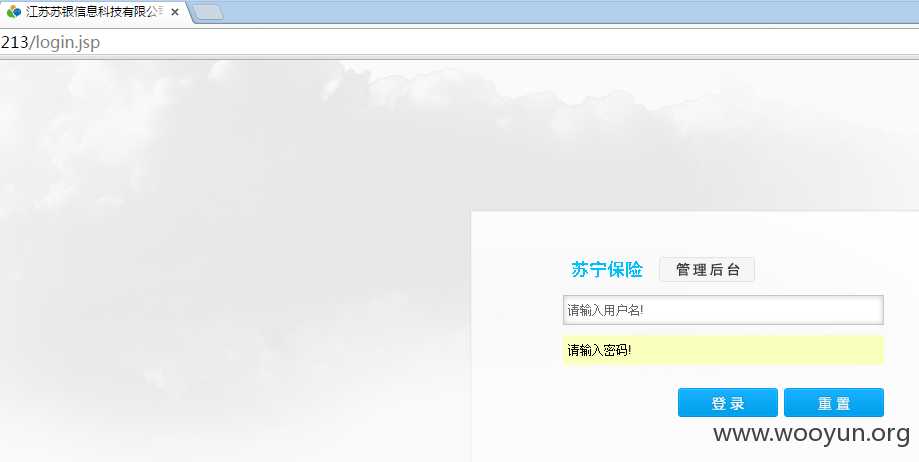
http://103.255.94.213/login.jsp
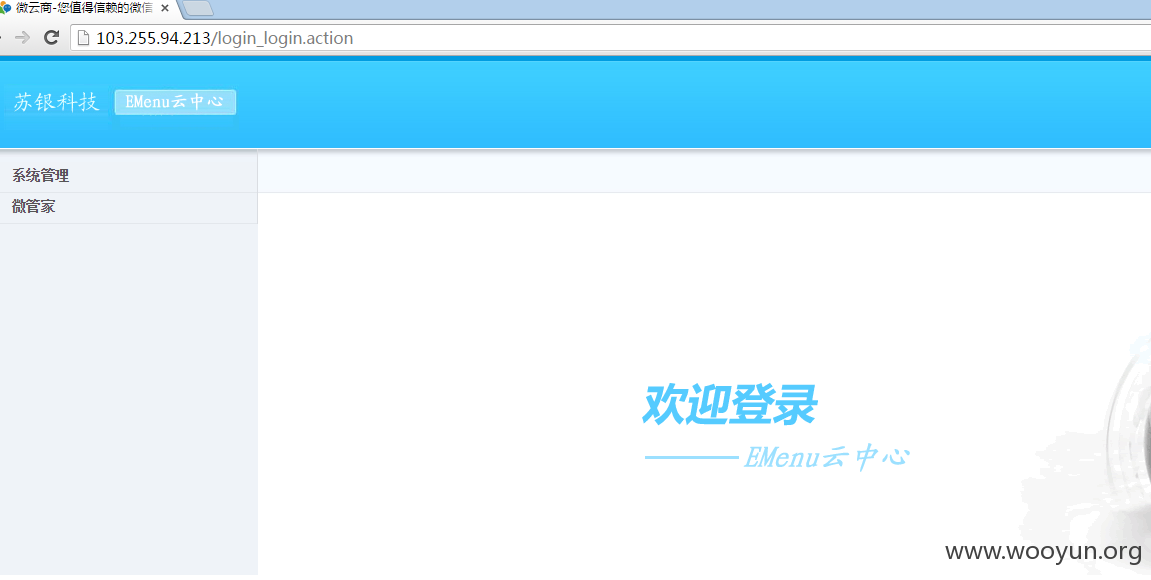
http://103.255.94.213/SNBX/Dealer_quit.action
这个登录居然不要验证码。
弱密码登录
admin 123456
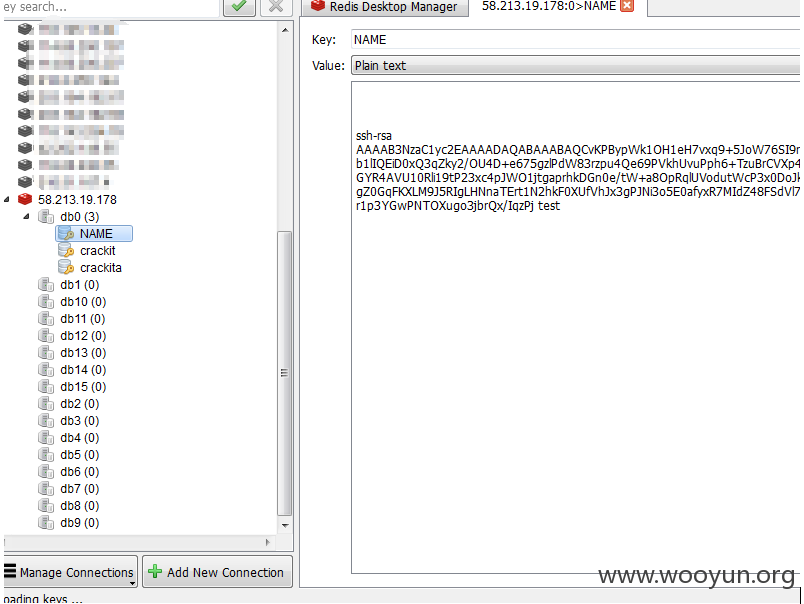
58.213.19.178 好像已经被日了
修复方案:
版权声明:转载请注明来源 _Thorns@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-11-27 14:12
厂商回复:
感谢提交。
最新状态:
暂无