漏洞概要
关注数(24)
关注此漏洞
漏洞标题:土豆某系统SQL注入到Getshell
提交时间:2015-11-27 09:47
修复时间:2016-01-11 19:20
公开时间:2016-01-11 19:20
漏洞类型:文件上传导致任意代码执行
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-11-27: 细节已通知厂商并且等待厂商处理中
2015-11-27: 厂商已经确认,细节仅向厂商公开
2015-12-07: 细节向核心白帽子及相关领域专家公开
2015-12-17: 细节向普通白帽子公开
2015-12-27: 细节向实习白帽子公开
2016-01-11: 细节向公众公开
简要描述:
rt
详细说明:
http://xianchang03.danmu.tudou.com/login.do
土豆弹幕系统 之前报过弱口令 其实登录有个注入
admin' or '1'='1 直接bypass登录
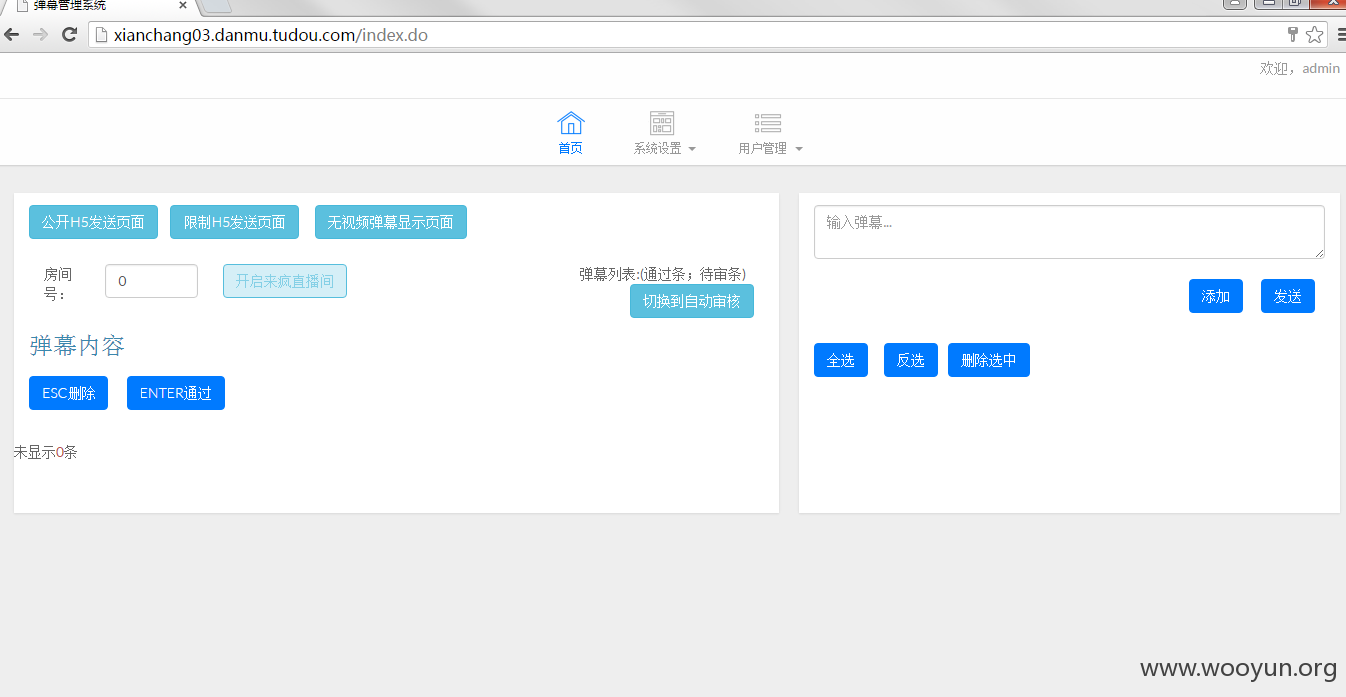
可以控制弹幕 不说
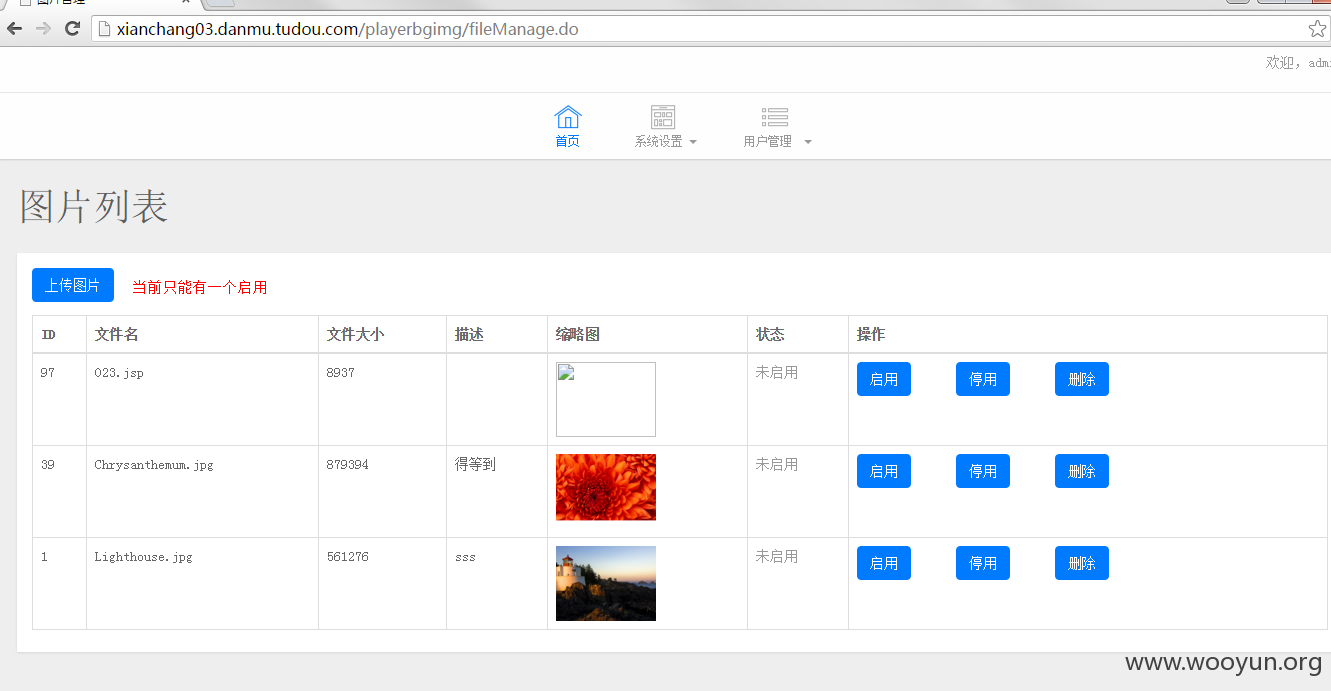
后台传图片 无任何过滤 可shell
内网中
漏洞证明:
http://xianchang03.danmu.tudou.com/login.do
土豆弹幕系统 之前报过弱口令 其实登录有个注入
admin' or '1'='1 直接bypass登录

可以控制弹幕 不说
后台传图片 无任何过滤 可shell

内网中
修复方案:
版权声明:转载请注明来源 玉林嘎@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-11-27 19:19
厂商回复:
确认漏洞,多谢玉林嘎。
最新状态:
暂无




