漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-036061
漏洞标题:07073主站及多个分站设计不当可破解他人账号密码
相关厂商:07073.com
漏洞作者: niliu
提交时间:2013-09-04 10:37
修复时间:2013-10-19 10:37
公开时间:2013-10-19 10:37
漏洞类型:设计缺陷/逻辑错误
危害等级:低
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-09-04: 细节已通知厂商并且等待厂商处理中
2013-09-04: 厂商已经确认,细节仅向厂商公开
2013-09-14: 细节向核心白帽子及相关领域专家公开
2013-09-24: 细节向普通白帽子公开
2013-10-04: 细节向实习白帽子公开
2013-10-19: 细节向公众公开
简要描述:
07073主站及60多个分站设计不当可任意登陆他人账号
详细说明:
主站及所有分站均存在此问题,
登陆是无验证码也无登陆错误次数限制,
导致可爆破他人密码。
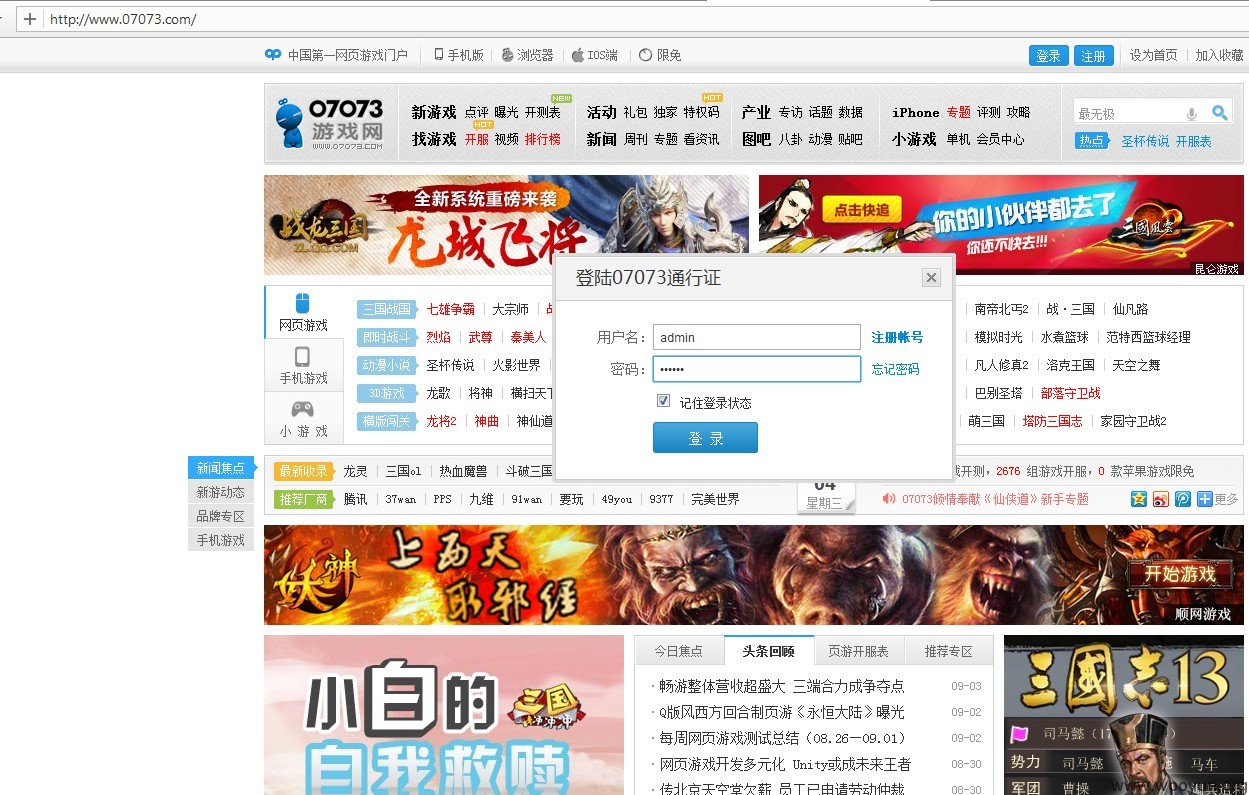
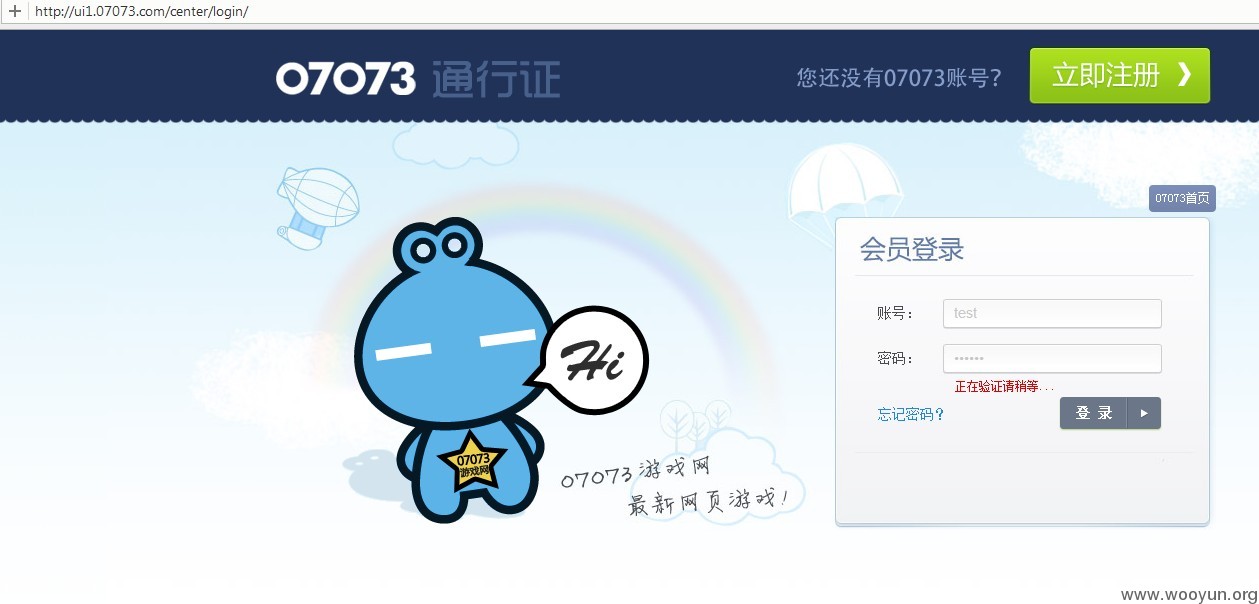
以用户admin密码123456,
登陆时抓包如下
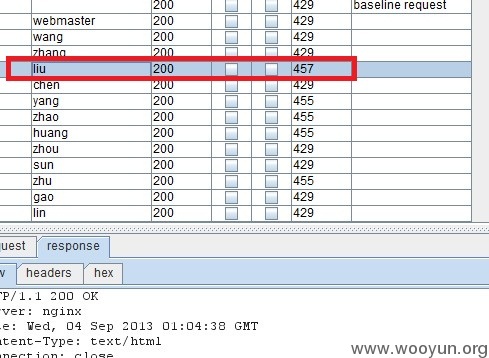
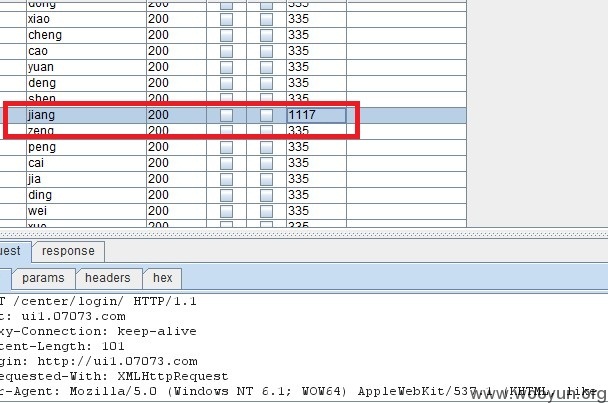
直接对用户名admin进行批量猜解
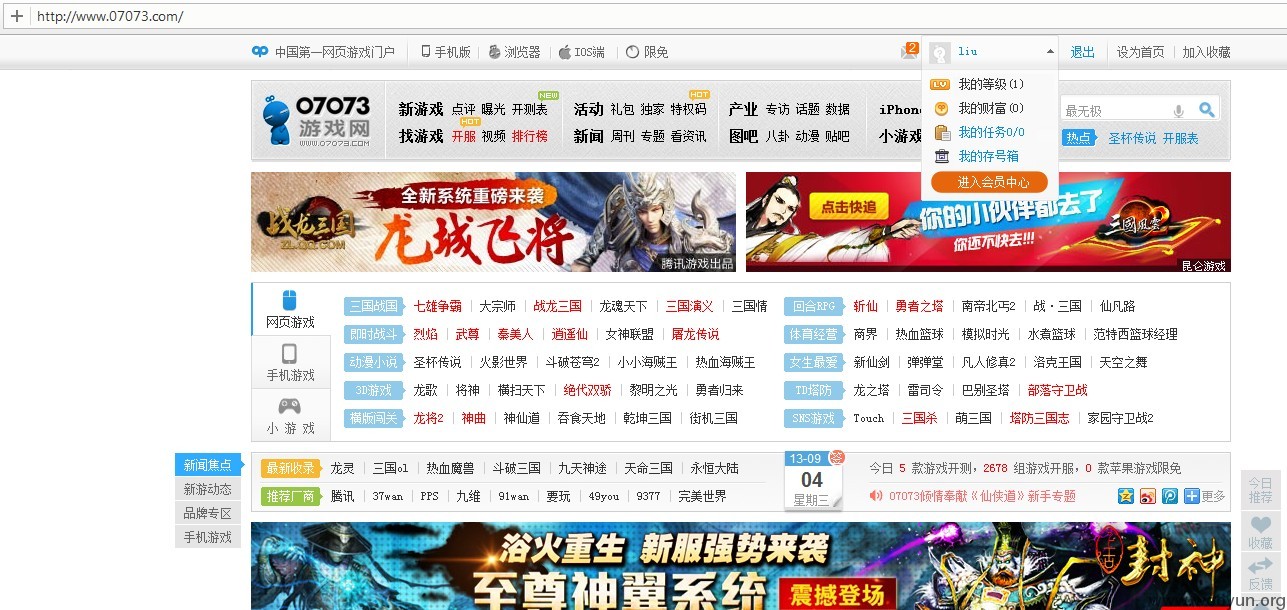
liu:123456
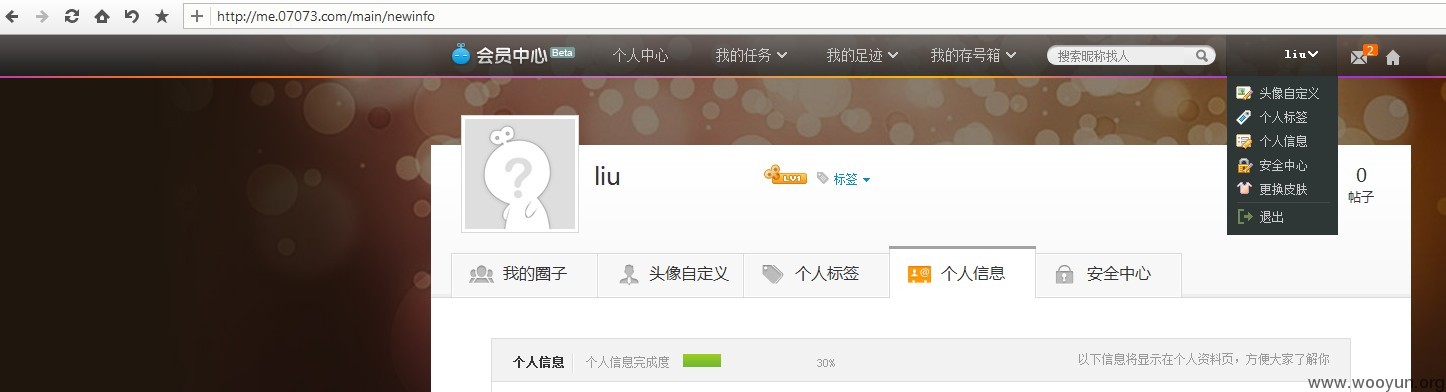
登陆截图
某分站:
以用户test密码111111登陆
登录时抓包如下
还是以密码不变,对用户名参数userAccount进行批量破解
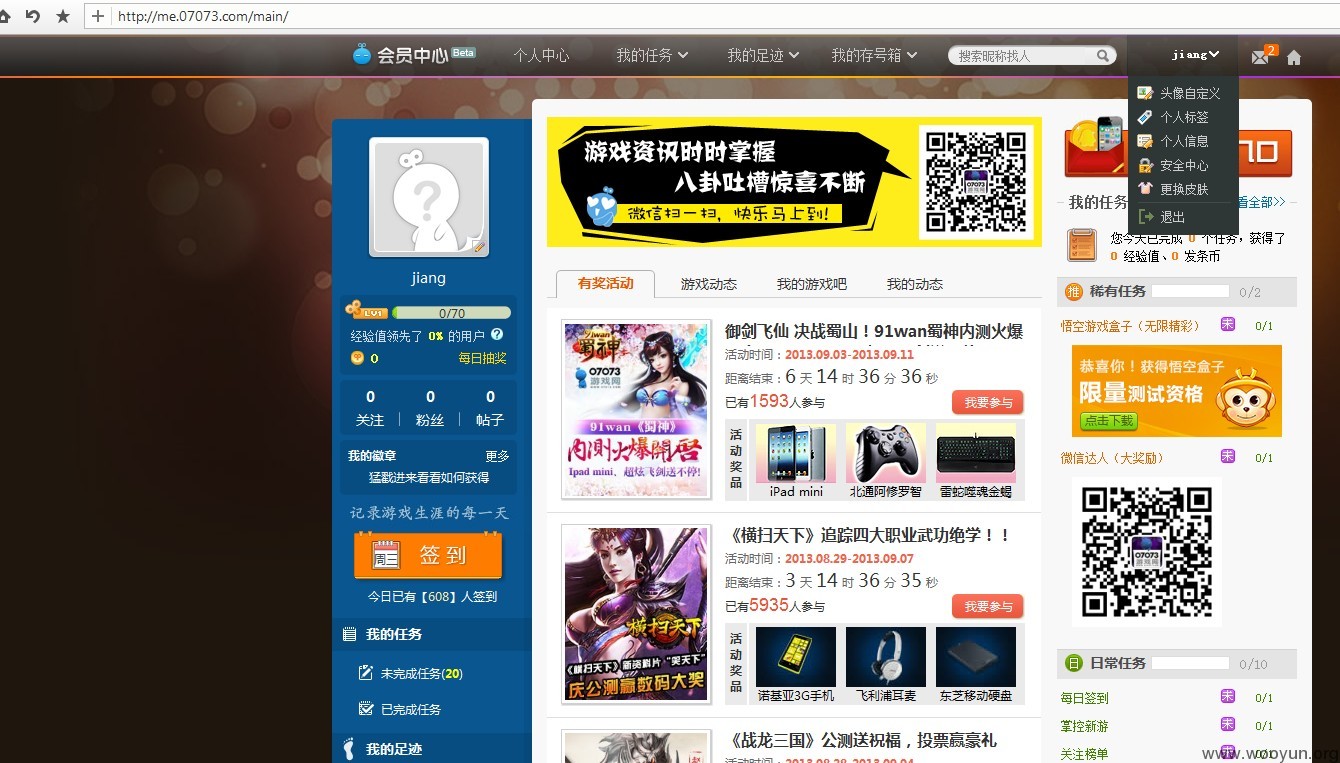
jiang:111111登陆截图
而且账号在各个分站都是通用的,什么游戏,论坛,贴吧什么的挺多的。
漏洞证明:
问题涉及全部分站六七十个吧
修复方案:
登陆时同一加上验证码吧!
求个小礼物~ :D
版权声明:转载请注明来源 niliu@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2013-09-04 10:46
厂商回复:
感谢,我们正努力解决该漏洞
最新状态:
暂无