源码下载地址:http://epaper.uestc.edu.cn/epaper.tar.gz
下载解压看看发现
/var/www/admin/application/config/database.php
从这得知了数据库的用户名:root 密码:ukf8rz5gv8
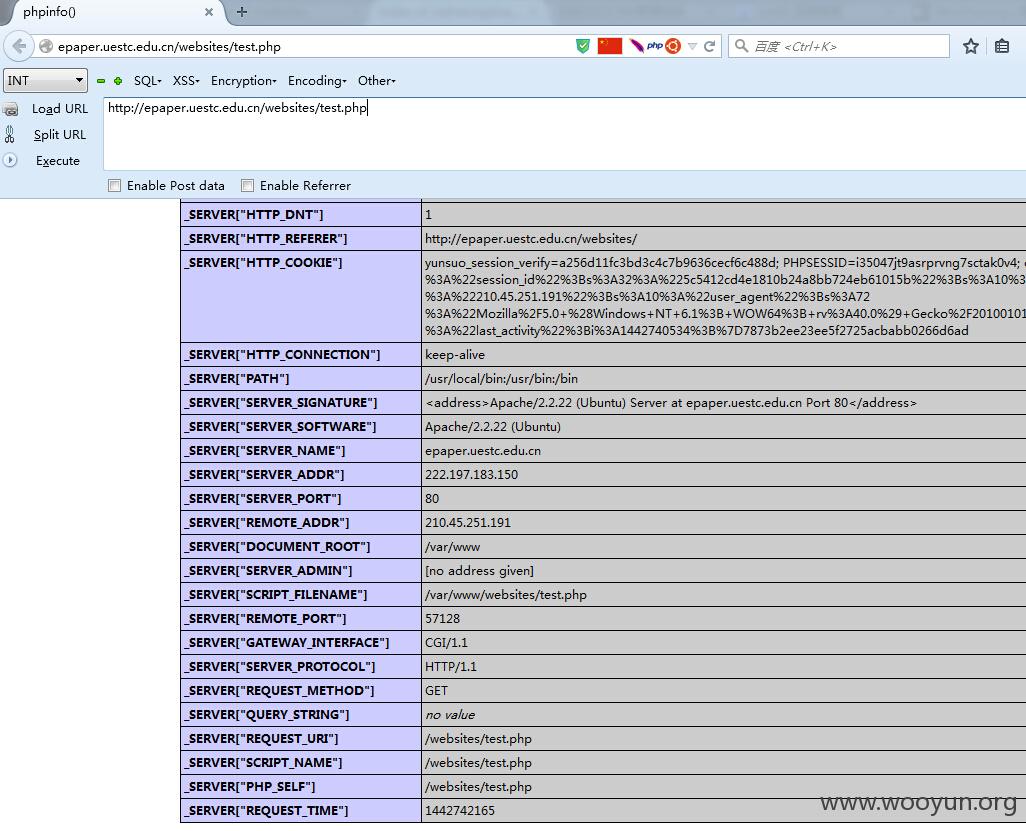
然后发现http://epaper.uestc.edu.cn/websites/目录可遍历,在这个目录里面发现test.php,点进去一看竟然是phpinfo
继续,发现phpmyadmin可以直接访问,http://epaper.uestc.edu.cn/phpmyadmin,使用上面得到的用户名密码登录
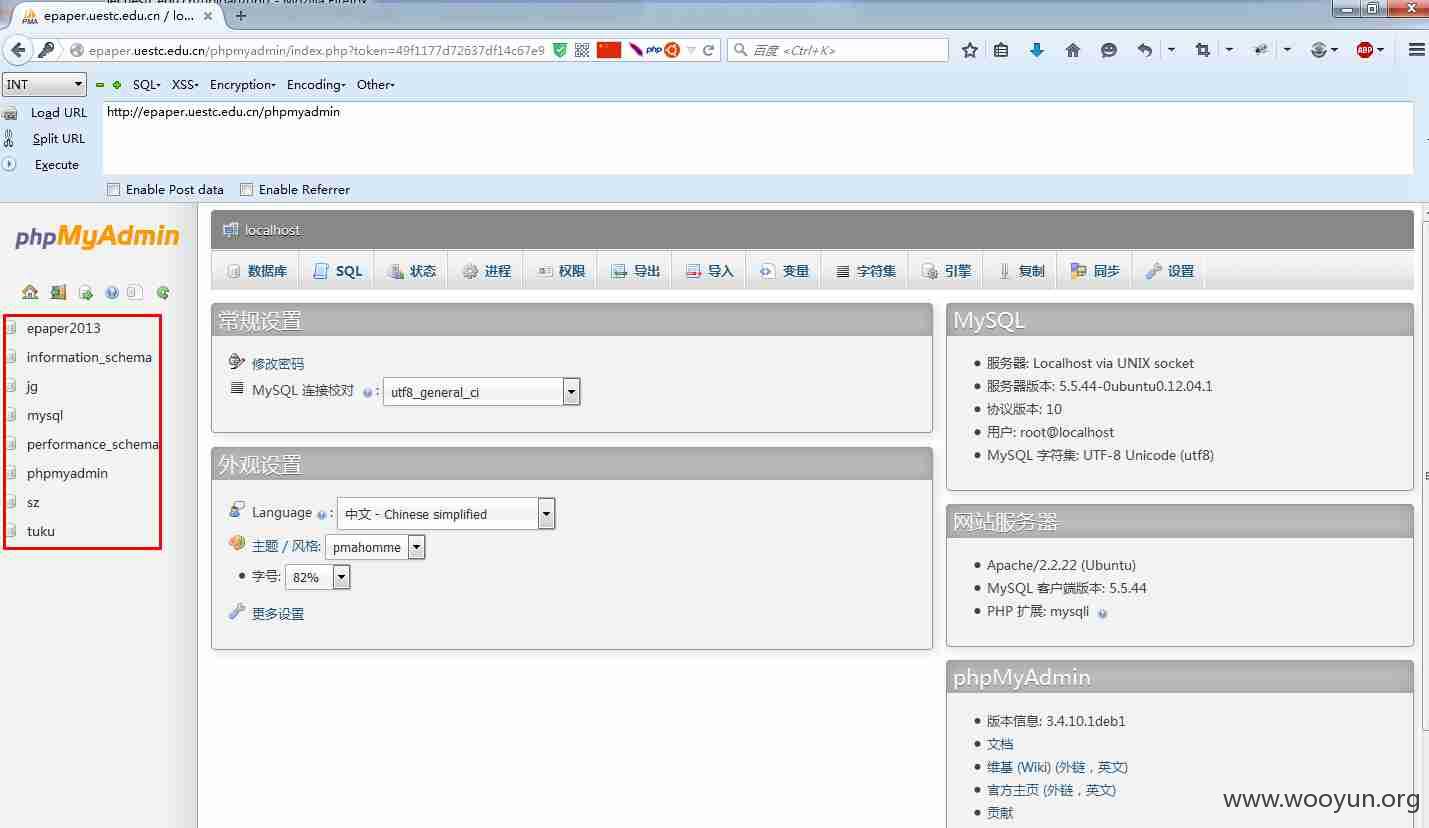
登进来后直奔我们的校报的用户密码(为什么不直接Getshell呢,因为竟然没写权限...)
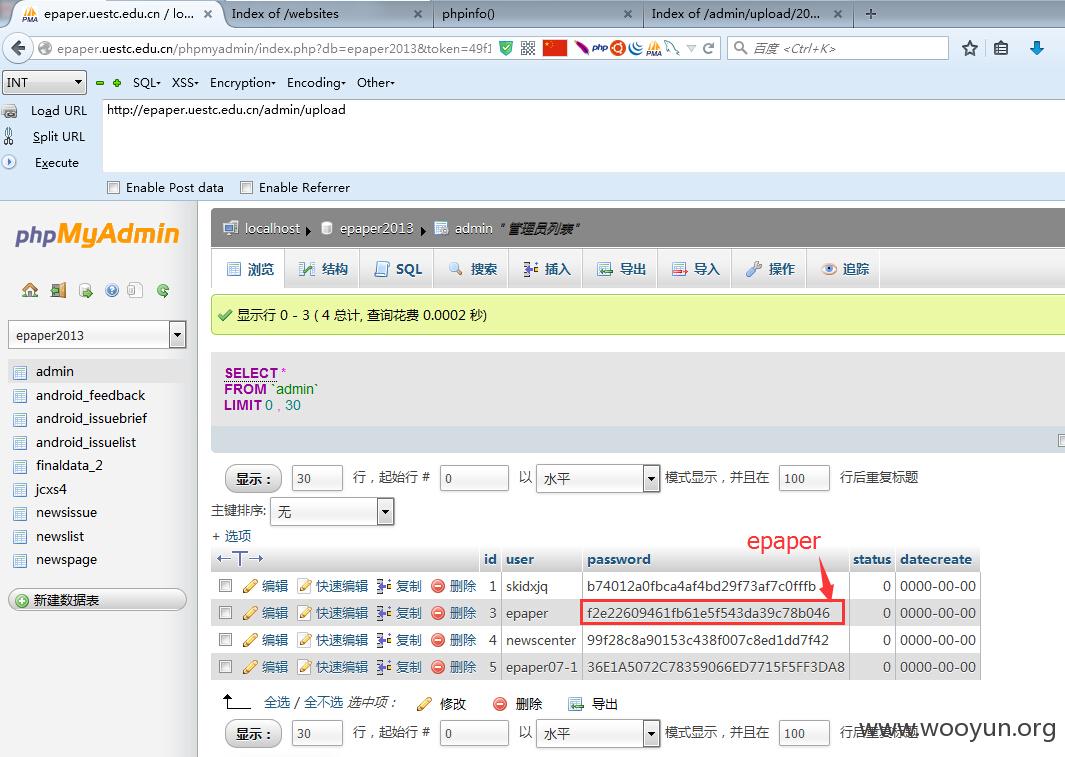
拿到用户名密码尝试登录,后台地址:http://epaper.uestc.edu.cn/admin/

之后逛逛发现还有其他的网站管理员的账户密码,一个个来
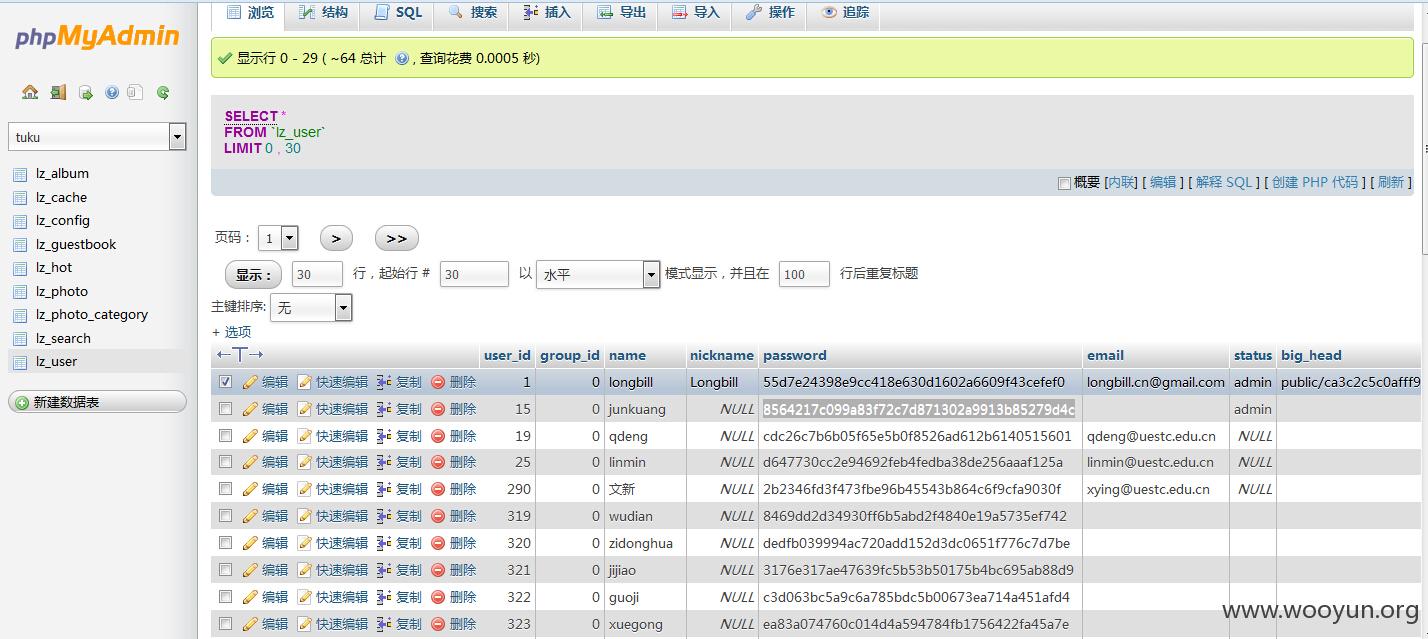
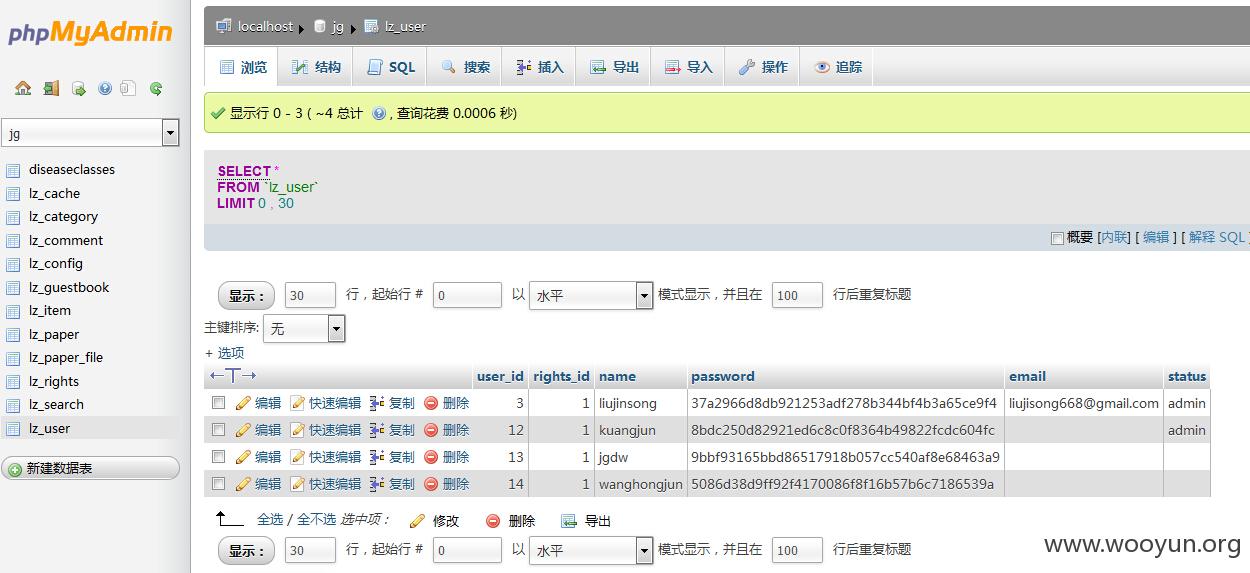
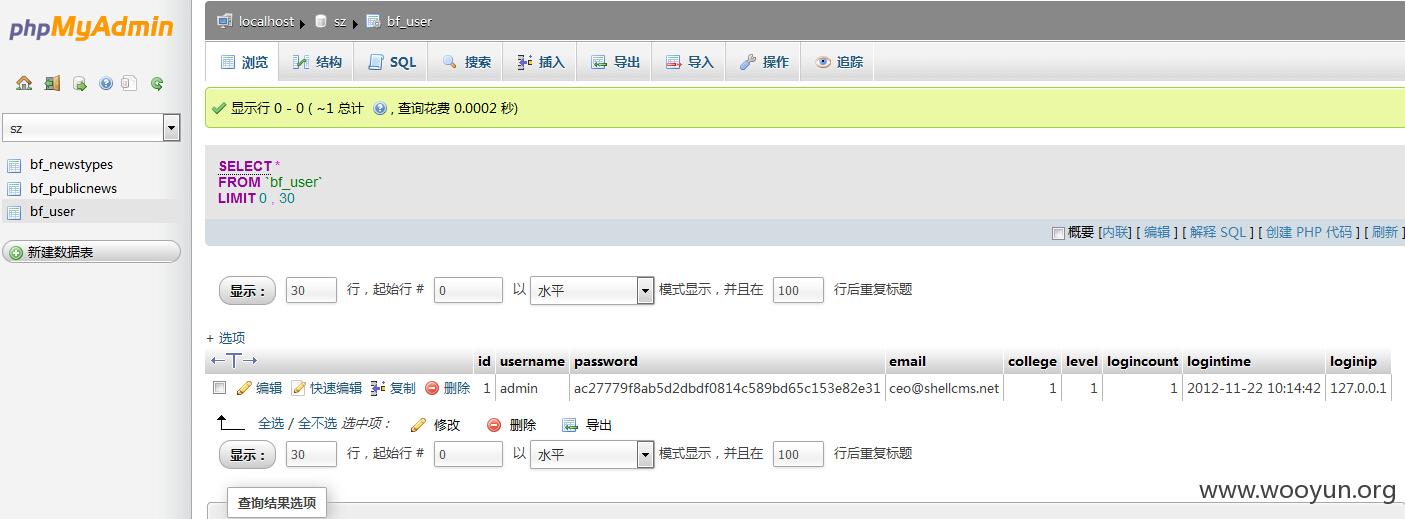
就这样吧,怕被老师请去喝茶不继续了。









